-
Epic
-
Resolution: Done
-
Major
-
openshift-4.10, openshift-4.11, openshift-4.12
-
[Spike] Explore the option of creating private S3 bucket to host OIDC endpoint
-
In Progress
-
None
-
False
-
-
False
-
Not Selected
-
None
-
None
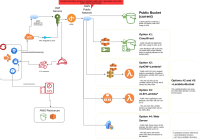
Currently, ccoctl creates a public S3 bucket to host OIDC endpoint that is accessible over the internet. Many customers have complained about this approach as their security policies do not allow creation of public S3 bucket. As part of this spike, we need to explore if there is any way we can make it private. Some of the options explored by SPLAT team are in the attached diagram (private_S3_options.png). We need to explore if any of those options are feasible.
- is related to
-
CCO-221 Document restricting access to OIDC S3 for STS installations using AWS CloudFront
-
- Closed
-
-
CCO-222 Add ccoctl option to create private s3 bucket with OIDC configurations served through public CloudFront URL
-
- Closed
-
- relates to
-
RFE-3614 Define custom domain in CloudFront to host OIDC public URL
-
- Refinement
-
-
RFE-2898 OCP on AWS with manual STS requires private S3 bucket to host OIDC endpoint
-
- Closed
-
-
CCO-281 AWS STS Implement procedure for migrating from a public s3 bucket OIDC to a private s3 bucket OIDC with CloudFront Distribution
-
- To Do
-