-
Not Started
-
Not Started
-
Not Started
-
Not Started
-
Not Started
-
Not Started
-
https://gitlab.cee.redhat.com/red-hat-3scale-documentation/3scale-documentation/merge_requests/174, https://gitlab.cee.redhat.com/red-hat-3scale-documentation/3scale-documentation/commit/94f50b7f5b050087b796d013618aaf3b2a817ef5, https://gitlab.cee.redhat.com/red-hat-3scale-documentation/3scale-documentation/commit/a9fa0f3f719fec6033dce27d024acc056e22cfdd
-
Sprint 2020-57, integration-doc-2020-01-27
8.2.1. Configuring with RH SSO
Since OpenShift OAuth server is not RHSSO, 8.2.1 conflicts with 8.2.1.1. RH-SSO in 8.2.1 should be general OAuth Server.
Ensure that users have proper permissions to view cluster projects containing discoverable services.
For example, to give <user> view permission for the <namespace> project, use this command:
oc adm policy add-role-to-user view <user> -n <namespace>
Please go into detail, since it's difficult to find what user and namespace mean here. It's the admin user of a namespace that has a service should be discovered.
8.3. Discovering services
Procedure
Log in to the 3scale Administration Portal.
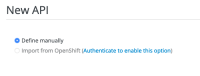
From the Admin Portal’s Dashboard, click New API.
Choose Import from OpenShift.
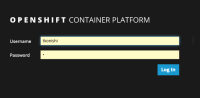
When OAuth token isn't valid, 3scle should be authorised by the namespace admin like this:
So please add a note for the process.
- blocks
-
THREESCALE-4050 Update Service Discovery doc to incorporate peer review comments
-
- Closed
-