-
Bug
-
Resolution: Done
-
Major
-
None
-
RH-SSO-7.6.5
-
False
-
-
False
-
-
On a confidential client using Authorization, create one resource with 2 scopes and User-Managed Access Enabled:
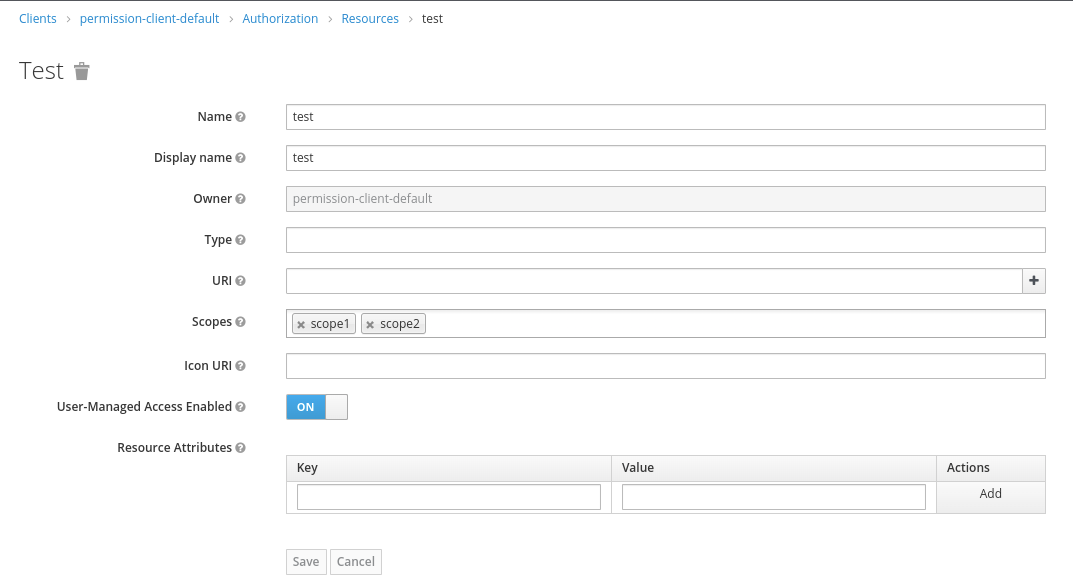
Assign the user to the permission and just one of the scopes(in my case i have assigned the scope1):
#!/bin/bash export REALM="permissions-test" export CLIENT_ID="permission-client-default" export CLIENT_SECRET="HumjZDHltnIixH3kLvrrfKDvPw2Q59td"export ACCESS_TOKEN=$( curl \ -d "client_id=${CLIENT_ID}" \ -d "client_secret=${CLIENT_SECRET}" \ -d "grant_type=client_credentials" \ "http://localhost:8080/auth/realms/${REALM}/protocol/openid-connect/token" \ | jq -r '.access_token' ) curl -X POST "http://localhost:8080/auth/realms/${REALM}/authz/protection/permission/ticket" \ -H "Authorization: Bearer ${ACCESS_TOKEN}" \ -H "Content-Type: application/json" \ -d '{ "resource": "8f6ccd63-8399-4266-aae4-a919c9d8776d", "requester": "084db0fc-4331-4241-9c22-89f84b8e522d", "granted": true, "scopeName": "scope1" }' | jq { "id": "47c4e482-e01d-4ef4-8dd6-277a47d634a8", "owner": "4a6cc3bb-9b19-4107-8a64-f36fcfbd5505", "resource": "8f6ccd63-8399-4266-aae4-a919c9d8776d", "scope": "bf5981fd-84c2-4e5e-b75c-9b993063d1cb", "granted": true, "requester": "084db0fc-4331-4241-9c22-89f84b8e522d" }
After that, query the permission by Id and by Name:
export REALM="permissions-test" export CLIENT_ID="permission-client-default" export CLIENT_SECRET="HumjZDHltnIixH3kLvrrfKDvPw2Q59td" export TEST_USER="testuser" export TEST_USER_PASSWORD="abc123" export RESOURCE_ID="8f6ccd63-8399-4266-aae4-a919c9d8776d" export RESOURCE_NAME="test" export ACCESS_TOKEN=$( curl \ -d "client_id=${CLIENT_ID}" \ -d "client_secret=${CLIENT_SECRET}" \ -d "grant_type=password" \ -d "username=${TEST_USER}" \ -d "password=${TEST_USER_PASSWORD}" \ "http://localhost:8080/auth/realms/${REALM}/protocol/openid-connect/token" \ | jq -r '.access_token' \ ) curl -X POST http://localhost:8080/auth/realms/${REALM}/protocol/openid-connect/token \ -H "Authorization: Bearer ${ACCESS_TOKEN}" \ --data "grant_type=urn:ietf:params:oauth:grant-type:uma-ticket" \ --data "audience=${CLIENT_ID}" \ --data "permission=${RESOURCE_ID}" \ --data "response_mode=permissions" \ | jq # Result by resourceID: [ { "scopes": [ "scope1" ], "rsid": "8f6ccd63-8399-4266-aae4-a919c9d8776d", "rsname": "test" } ] curl -X POST http://localhost:8080/auth/realms/${REALM}/protocol/openid-connect/token \ -H "Authorization: Bearer ${ACCESS_TOKEN}" \ --data "grant_type=urn:ietf:params:oauth:grant-type:uma-ticket" \ --data "audience=${CLIENT_ID}" \ --data "permission=${RESOURCE_NAME}" \ --data "response_mode=permissions" \ | jq # Result by resourceName: [ { "scopes": [ "scope1", "scope2" ], "rsid": "8f6ccd63-8399-4266-aae4-a919c9d8776d", "rsname": "test" } ]
Even that i have assigned just `scope1` to the `test` resource. When calling the permissions endpoint using the resourceName, both scopes are retrieved.
This was tested since version 7.5 to 7.6.6. RHBK 22 is also affected.
- links to
- mentioned on