-
Bug
-
Resolution: Done
-
Undefined
-
1.2
-
None
-
False
-
-
False
-
-
Bug Fix
-
Done
-
-
Description of problem:
We are preparing demo/MVP for customer, with integration with azure devops. After configurating the azure entra sso and azure org data import, we can login rhdh using azure entra sso, but we find the user session can not associate with the azure user entity imported. We think the problem is caused by the auth login in source code (backstage-showcase/packages/backend/src/modules/authProvidersModule.ts at main · janus-idp/backstage-showcase (github.com)), which using id instead of username/email for microsoft. Here is the slack thread debugging and talking on this issues.
Prerequisites (if any, like setup, operators/versions):
We use instance on demo.redhat.com, and hack the configuration to do the testing, Here is the patch we used.
data: dynamic-plugins.yaml: | plugins: - disabled: false package: ./dynamic-plugins/dist/backstage-plugin-azure-devops - disabled: false package: ./dynamic-plugins/dist/backstage-plugin-azure-devops-backend-dynamic # - disabled: false # package: ./dynamic-plugins/dist/backstage-plugin-scaffolder-backend-module-azure-dynamic # - disabled: false # integrity: >- # sha512-WxRXsTppHKxzMHpUvEiQR3rYPypSHDHABAqegjareHYEXgA5uVBsRW2zES6GpOeei45KnxGL+NcuoKQezg1D7A== # package: '@backstage/plugin-azure-devops@0.4.4' # - disabled: false # integrity: >- # sha512-wHZC7riqyakSzPrxM1+edu1Et99Q0gAd0WXxrnclUo7lT45+xvqYxzbdVR9Kr7OHr/6AugMghJZV1BzCxl2+PQ== # package: '@backstage/plugin-azure-devops-backend@0.6.5' - disabled: false integrity: >- sha512-H3d4UThnU+EUCFfH3lBPvm0mYXdAQ/GG4blg71Oe8nfjm9eN9yATxq8r74430Xyi1xn+2HVbVbLyvWpgpIp/ig== package: '@backstage/plugin-catalog-backend-module-azure@0.1.38' - disabled: false integrity: >- sha512-C7qhlHOQeXMNMPekgEoTdTiVq2hHdZkHvUHpb4EyCOE8MzGFx1LTl7r7ch4jiFkr15YQuqOImYUc/JhGNnes8A== package: '@backstage/plugin-catalog-backend-module-msgraph@0.5.26' # - disabled: false # integrity: >- # sha512-eBfl2rPN3HrgECEeHS9uw9Y4xaAQgzNu7qn/kYarqTRi3Rnn5V8zMm5jU4gcqfcxdBbdpUb9HpRvOqk9V96VSA== # package: '@backstage/plugin-azure-devops-common@0.4.2' # - disabled: false # integrity: >- # sha512-iRxCHis0E2CemuEQ/CQvk9O5vVw3dRA/EOLvo4Ms1scfFDdJqogHH+KiVzEOf5nhf3YUmPpMT0cB+G4kx+th9A== # package: '@backstage/plugin-auth-backend-module-azure-easyauth-provider@0.1.1'upstream: backstage: extraEnvVars: - name: AZURE_CLIENT_ID value: <change me to secret value> - name: AZURE_CLIENT_SECRET value: <change me to secret value> - name: AZURE_TENANT_ID value: <change me to secret value> - name: AZURE_TOKEN value: <change me to secret value> - name: AZURE_ORG value: wangzheng422 - name: KEYCLOAK_BASE_URL value: https://keycloak-backstage.apps.cluster-qjwdr.sandbox928.opentlc.com/auth - name: KEYCLOAK_LOGIN_REALM value: backstage - name: KEYCLOAK_REALM value: backstage - name: KEYCLOAK_CLIENT_ID valueFrom: secretKeyRef: key: CLIENT_ID name: keycloak-client-secret-backstage - name: KEYCLOAK_CLIENT_SECRET valueFrom: secretKeyRef: key: CLIENT_SECRET name: keycloak-client-secret-backstage appConfig: integrations: azure: - host: dev.azure.com credentials: - organizations: - ${AZURE_ORG} personalAccessToken: ${AZURE_TOKEN} # clientId: ${AZURE_CLIENT_ID} # clientSecret: ${AZURE_CLIENT_SECRET} # tenantId: ${AZURE_TENANT_ID} auth: environment: production providers: microsoft: production: clientId: ${AZURE_CLIENT_ID} clientSecret: ${AZURE_CLIENT_SECRET} tenantId: ${AZURE_TENANT_ID} domainHint: ${AZURE_TENANT_ID} additionalScopes: - Mail.Send signIn: resolvers: # typically you would pick one of these - resolver: idMatchingUserEntityAnnotation - resolver: emailMatchingUserEntityProfileEmail - resolver: emailLocalPartMatchingUserEntityName - resolver: emailMatchingUserEntityAnnotation signInPage: microsoft catalog: locations: # https://dev.azure.com/wangzheng422/demo/_git/service-demo?path=%2Forg.yaml&version=GBmain&_a=contents # https://github.com/wangzheng422/backstage-customize/blob/data/org.yaml - target: https://dev.azure.com/wangzheng422/demo/_git/service-demo?path=%2Forg.yaml&version=GBmain&_a=contents type: url rules: - allow: [Group, User] - target: https://github.com/wangzheng422/red-hat-developer-hub-software-templates/blob/wzh-hack/templates/azure/dotnet-frontend/template.yaml type: url rules: - allow: [Template] providers: azureDevOps: yourProviderId: # identifies your dataset / provider independent of config changes organization: wangzheng422 project: '*' repository: '*' # this will match all repos starting with service-* path: /catalog-info.yaml schedule: # optional; same options as in TaskScheduleDefinition # supports cron, ISO duration, "human duration" as used in code frequency: { minutes: 30 } # supports ISO duration, "human duration" as used in code timeout: { minutes: 3 } microsoftGraphOrg: default: tenantId: ${AZURE_TENANT_ID} clientId: ${AZURE_CLIENT_ID} clientSecret: ${AZURE_CLIENT_SECRET} user: filter: > accountEnabled eq true and userType eq 'member' # select: ['id', 'displayName', 'mail'] # userPrincipalName eq 'demo-backstage@wangzheng422outlook.onmicrosoft.com' group: filter: > displayName eq 'demo-group-backstage' schedule: frequency: PT1H timeout: PT50M keycloakOrg: default: baseUrl: ${KEYCLOAK_BASE_URL} loginRealm: ${KEYCLOAK_LOGIN_REALM} realm: ${KEYCLOAK_REALM} clientId: ${KEYCLOAK_CLIENT_ID} clientSecret: ${KEYCLOAK_CLIENT_SECRET} schedule: # optional; same options as in TaskScheduleDefinition # supports cron, ISO duration, "human duration" as used in code frequency: { minutes: 1 } # supports ISO duration, "human duration" as used in code timeout: { minutes: 1 } initialDelay: { seconds: 15 } enabled: kubernetes: true techdocs: true argocd: true sonarqube: false keycloak: false # true -> false ocm: true github: false githubOrg: false gitlab: true jenkins: false permission: false azure: true azureDevOps: true microsoftGraphOrg: true keycloakOrg: false microsoft: true azureEasyAuth: false service: ports: backend: 4180 targetPort: backend
Steps to Reproduce
- login using azure entra sso
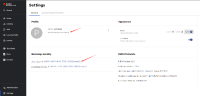
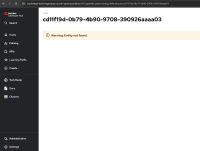
- in the setting of rhdh, click the user entity
- it report can not find.
Actual results:
user entity craeted with azure username as key, but the setting view of login session links to user entity with azure id as key, the the aut h login logic using id to match the user entity.
Expected results:
In the setting view, the login session can link to user entity imported correctly.
Reproducibility (Always/Intermittent/Only Once):
Always
Build Details:
RHDH Version: 1.2.0 Backstage Version: 1.26.5 Upstream: janus-idp/backstage-showcase main @ 0fbc913e Midstream: gitlab.cee.redhat.com/rhidp/rhdh rhdh-1-rhel-9 @ 9013daf3 Build Time: 2024-05-31T20:18:13Z
Additional info (Such as Logs, Screenshots, etc):
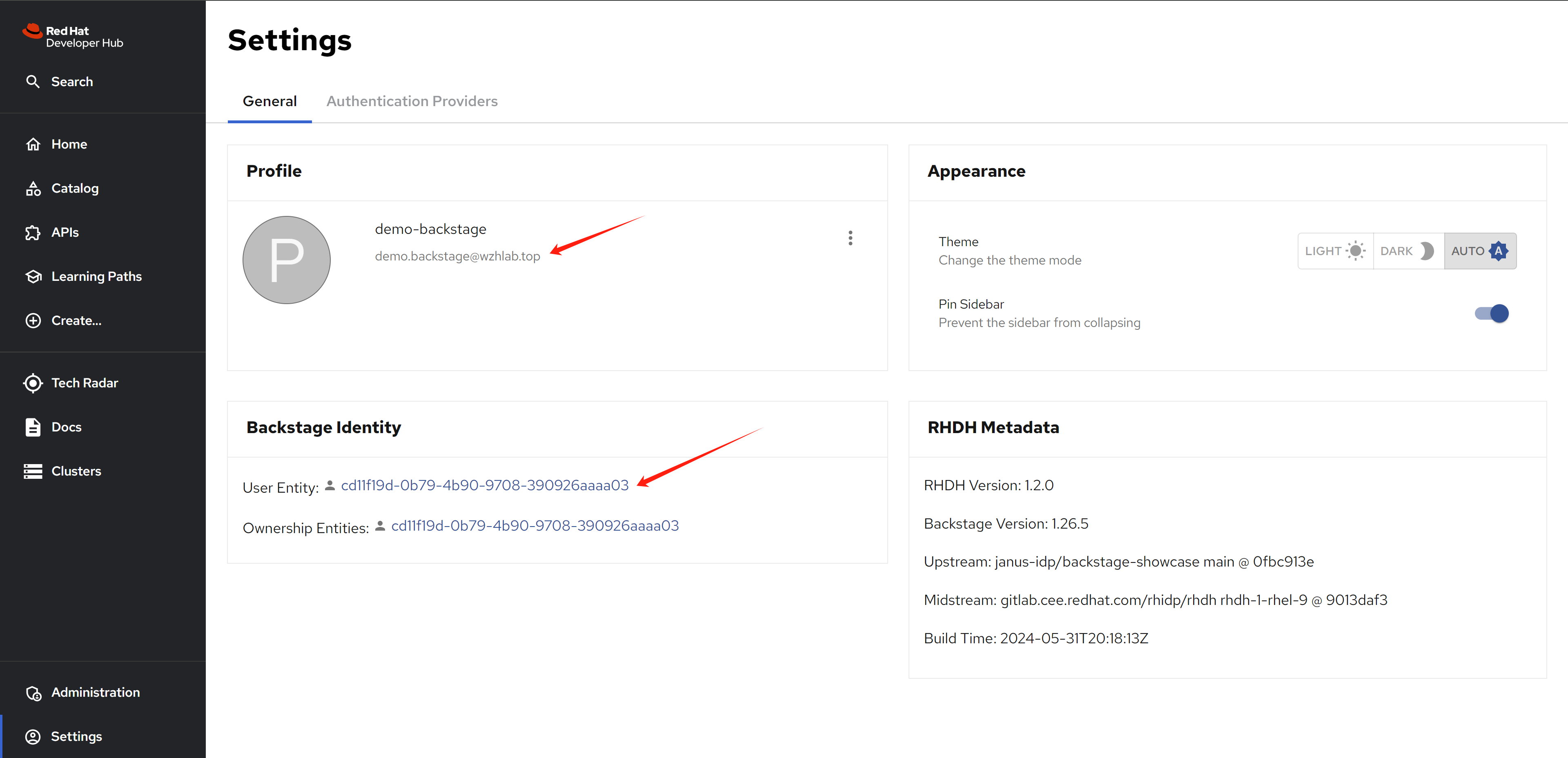
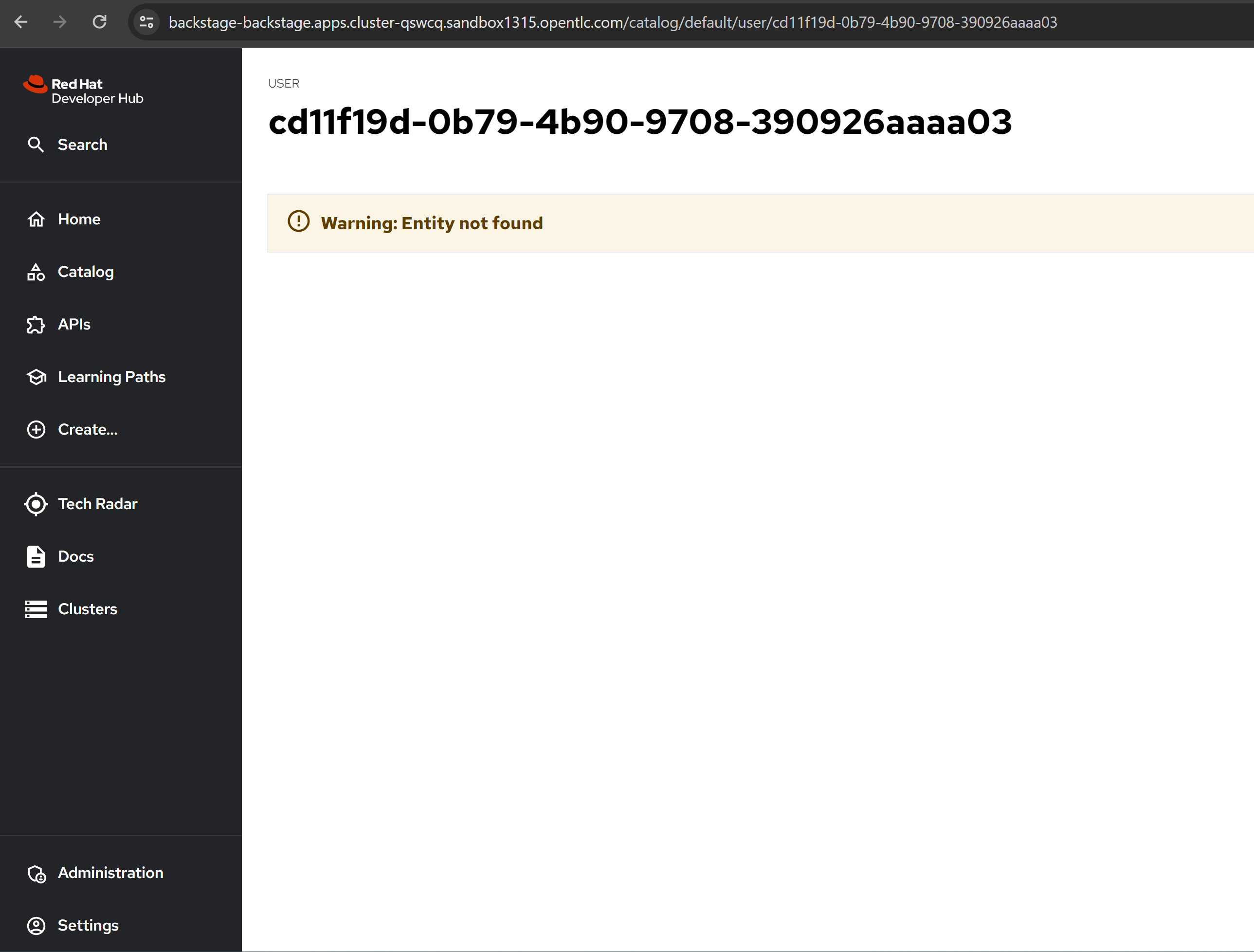
The user entity imported:
apiVersion: backstage.io/v1alpha1 kind: User metadata: namespace: default annotations: backstage.io/managed-by-location: msgraph:default/cd11f19d-0b79-4b90-9708-390926aaaa03 backstage.io/managed-by-origin-location: msgraph:default/cd11f19d-0b79-4b90-9708-390926aaaa03 microsoft.com/email: demo.backstage@wzhlab.top graph.microsoft.com/user-id: cd11f19d-0b79-4b90-9708-390926aaaa03 name: demo.backstage_wzhlab.top uid: f0159c5e-66d3-48c5-a7a6-6d1642e888e3 etag: 3855e339d338fa2830b2429a3c9dfb0b917174ac relations: - type: memberOf targetRef: group:default/demo-group-backstage target: kind: group namespace: default name: demo-group-backstage spec: profile: displayName: demo-backstage email: demo.backstage@wzhlab.top memberOf: - group:default/demo-group-backstage