-
Task
-
Resolution: Done
-
Major
-
None
-
None
-
None
-
None
-
False
-
-
False
-
-
This task is to remove a group of downstream patches, identified as the patches that make OpenJDK honor the RHEL crypto-policies in place, including the FIPS crypto-policy, which is a special case requiring a special automation on the Java Security Providers configuration.
Alternatives have been explored in OPENJDK-1686, with Alternative #2 already implemented and Alternative #1 proposed upstream. In parallel, a third alternative has also been proposed upstream, and is liked here for reference.
Every patch is listed as a sub-task, to be closed once we are able to remove this patch in a future OpenJDK 22 build, and in a OpenJDK 21 build assuming the work referred in this task is upstreamed. You can refer the full fips-21u-75ffdc48eda.patch list of included commits, which corresponds to java-21-openjdk-21.0.0.0.35-1.el8.
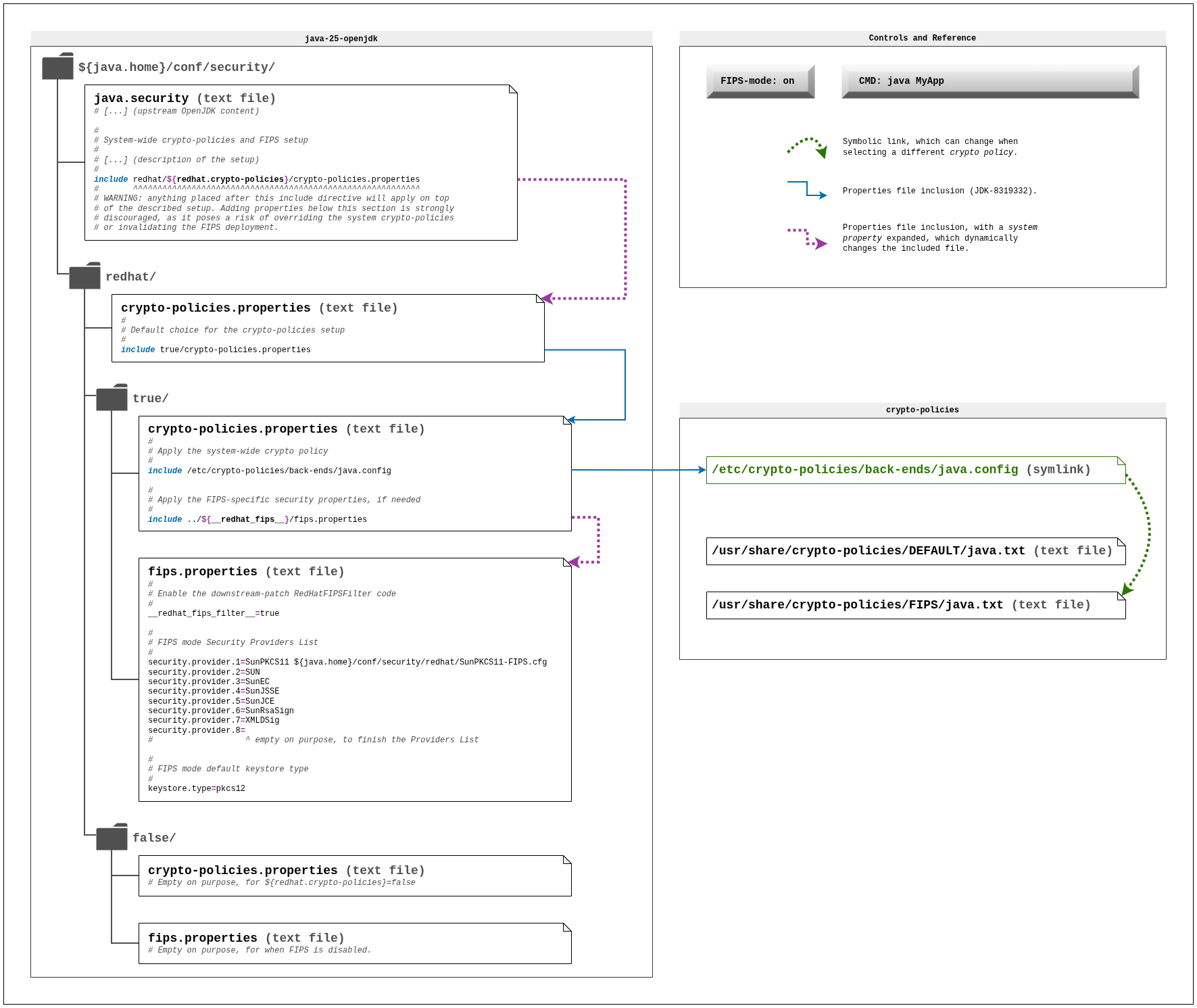
Following is a design for the Red Hat build of OpenJDK 25, to implement the crypto-policies and FIPS setup, leveraging the upstream JDK-8319332: Security properties files inclusion enhancement.
System-wide crypto-policies and FIPS setup of the Red Hat build of OpenJDK 25 (OPENJDK-1686, alternative #1)
Red Hat build of OpenJDK 25 will include the following configuration changes, depicted in the following interactive diagram (use the two control buttons to interact):
To keep the diagram readable and reduce its size, I omitted a big comment in java.security where the setup is fully described. Here is the complete excerpt that the Red Hat Build of OpenJDK will append to ${java.home}/conf/security/java.security:
# # System-wide crypto-policies and FIPS setup # # The following crypto-policies setup automatically detects when the system # is in FIPS mode and configures OpenJDK accordingly. If OpenJDK needs to # ignore the system and disable its FIPS setup, just disable the usage of # the system crypto-policies, by any of the methods described below. # # The redhat.crypto-policies system property is a boolean switch that # controls the usage on a per-run basis. For example, pass # -Dredhat.crypto-policies=false to disable the system crypto-policies. # # This setup consists of the following files in $JAVA_HOME/conf/security: # # 'redhat/false/crypto-policies.properties' (policies usage disabled file) # Empty file, applied when the boolean switch is passed as false. # # 'redhat/true/crypto-policies.properties' (policies usage enabled file) # Performs the crypto-policies and FIPS setup, applied when the boolean # switch is passed as true. # # 'redhat/crypto-policies.properties' (policies usage default file) # Determines the default choice by including one of the previous files, # applied when the boolean switch is not passed. # The system crypto-policies usage is enabled by default: # include true/crypto-policies.properties # # To enable or disable the usage of the crypto-policies on a per-deployment # basis, edit the policies usage default file, changing the included file. # For example, execute the following command to persistently disable the # crypto-policies: # sed -i s/true/false/ $JAVA_HOME/conf/security/redhat/crypto-policies.properties # Applications can still override this on a per-run basis, for example by # passing -Dredhat.crypto-policies=true. # # To disable the redhat.crypto-policies boolean switch, modify the following # include directive as follows. Replace ${redhat.crypto-policies} by true to # force-apply the system crypto-policies: # include redhat/true/crypto-policies.properties # Remove or comment out the include directive to force-disable the setup: # #include redhat/${redhat.crypto-policies}/crypto-policies.properties # include redhat/${redhat.crypto-policies}/crypto-policies.properties # ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^ # WARNING: anything placed after this include directive will apply on top # of the described setup. Adding properties below this section is strongly # discouraged, as it poses a risk of overriding the system crypto-policies # or invalidating the FIPS deployment.
And here is the ${java.home}/conf/security/redhat/SunPKCS11-FIPS.cfg file content:
name = FIPS
library = /path/to/lib/libnssadapter.so
slot = 3
nssUseSecmod = false
attributes(*,CKO_SECRET_KEY,*)={ CKA_SIGN=true CKA_ENCRYPT=true }
NSS Native FIPS Key Import Export Adapter (OPENJDK-2135)
${java.home}/lib/libnssadapter.so is built from the OPENJDK-2135 development, and will be shipped along other Red Hat build of OpenJDK 25 libraries.
Remaining Red Hat build of OpenJDK 25 FIPS patch
With the JDK-8315487: Security Providers Filter work still pending, we need to keep a reduced version of the downstream FIPS patch.
Also, we are introducing a temporary __redhat_fips__ system property as a downstream patch. After some emails exchange with Sean Mullan (Oracle engineer and Lead of the OpenJDK Security Group), we realized an upstream proposal for a system property that reflects the /proc/sys/crypto/fips_enabled status is very unlikely to be accepted. We'll explore other alternatives, or come back to the RHEL-107438 approach.
A pull request with this patch has been integrated to the fips-25u branch: ![]() rh-openjdk/jdk#40 Implement OpenJDK 25 FIPS patch (for
rh-openjdk/jdk#40 Implement OpenJDK 25 FIPS patch (for OPENJDK-4184).
- is blocked by
-
OPENJDK-1686 Explore support of crypto-policies in the context of Temurin builds
-
- Closed
-
- is depended on by
-
OPENJDK-4184 Include new FIPS patch in OpenJDK 25 portable build [portable: java-25-openjdk]
-
- Closed
-
- is related to
-
RHEL-107438 FIPS crypto policy should now include ${java.home}/conf/security/java.security.fips
-
- Closed
-
- links to
-
JDK-8309330 Allow java.security to be extended via a properties directory
-
JDK-8319332 Security properties files inclusion
-
 openjdk/jdk#14277
8309330: Allow java.security to be extended via a properties directory
openjdk/jdk#14277
8309330: Allow java.security to be extended via a properties directory
-
 openjdk/jdk#16483
8319332: Security properties files inclusion
openjdk/jdk#16483
8319332: Security properties files inclusion