-
Outcome
-
Resolution: Done
-
Major
-
None
-
None
-
Product / Portfolio Work
-
40% To Do, 0% In Progress, 60% Done
-
-
False
-
-
False
-
None
Outcome Overview
Once all Features and/or Initiatives in this Outcome are complete, what tangible, incremental, and (ideally) measurable movement will be made toward the company's Strategic Goal(s)?
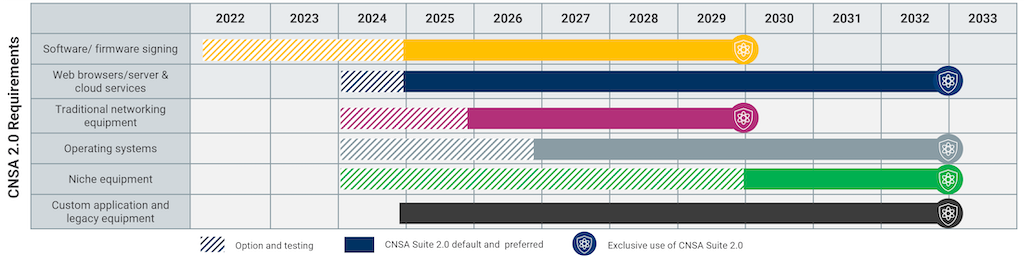
This outcome is about OpenShift 4.20+ support of Post Quantum Computing (PQC) algorithms in 2025 to support the NIST Commercial National Security Algorithm (CNSA) 2.0 deployment timeline. In 2025, the requirements are:
- Support and prefer PQC algorithms for software/firmware signing
- Support and prefer PQC algorithms for Web browser, Web servers and cloud services
This outcome is considered complete when OpenShift & Layered products offer a PQC method for digital signing, web-based transaction can use end-to-end PQC algorithms, and Red Hat cloud services also support PQC algorithms.
Success Measure
Q3: Complete testing of ML-KEM support in the OCP 4.20 control plane (100%)
Q4: Support ML-KEM in Service Mesh 3.x with OCP 4.20 + UBI 9.7 in an early dev preview mode
Further Information
To understand Post Quantum Cryptography and see a Kubernetes-based demo, please watch this IBM session from Kubecon NAM 2024: https://www.youtube.com/watch?v=6eQA15r6IHY (36 minutes)
Red Hat Links:
https://www.redhat.com/en/blog/red-hats-path-post-quantum-cryptography
https://www.redhat.com/en/blog/how-red-hat-integrating-post-quantum-cryptography-our-products
Also of interest:
Google Willow announcement blog: https://blog.google/technology/research/google-willow-quantum-chip/
Success Criteria
What is the success criteria for this strategic outcome? Avoid listing Features or Initiatives and instead describe "what must be true" for the outcome to be considered delivered.
Success means:
- Our customers can use PQC algorithms to check the digital signature of OCP & Layered bits
- Our customers can run PQC enabled web-based sessions, from their browser to the OCP application (and anything in between)
- Red Hat cloud services supports PQC algorithms (jjung@redhat.com will clarify this requirement, lacking info as of DEC 16, 2024)
Expected Results (what, how, when)
What incremental impact do you expect to create toward the company's Strategic Goals by delivering this outcome? (possible examples: unblocking sales, shifts in product metrics, etc. {}{} provide links to metrics that will be used post-completion for review & pivot decisions). {}For each expected result, list what you will measure and +when you will measure it (ex. provide links to existing information or metrics that will be used post-completion for review and specify when you will review the measurement such as 60 days after the work is complete)
This is NIST roadmap to support PQC, and not following it creates risks:
- Failure to comply would jeopardize our NAM Public Sector customers, who must obey the NIST roadmap.
- We already have customer inquiries, meaning we need to provide a roadmap and progress to support PQC or risk letting competitors occupy the space we don't fill.
- Quantum Computer progress is dynamic, and the roadmap NIST provides (full PQC support by 2030-2032) is based on the current estimated progress of the technology. A breakthrough might require switching to PQC algorithms sooner than planned, and we cannot fall behind the NIST timeline.
This is a must-do, not an optional functionality.
Post Completion Review – Actual Results
After completing the work (as determined by the "when" in Expected Results above), list the actual results observed / measured during Post Completion review(s).
- depends on
-
OCPSTRAT-1364 Support TLS v1.3: Improve validation of TLS Modern Profile for Control-Plane components
-
- Closed
-
- is related to
-
RUN-2452 Digest change from sha256
-
- Closed
-
- links to