-
Bug
-
Resolution: Done
-
Major
-
netobserv-ocp4.12
-
None
-
None
-
Quality / Stability / Reliability
-
False
-
-
None
-
Important
-
None
-
None
-
NetObserv - Sprint 228, NetObserv - Sprint 229, NetObserv - Sprint 230, NetObserv - Sprint 231, NetObserv - Sprint 232
-
None
-
None
-
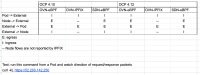
In Network Traffic. under Query Options, the last sentence in the tooltip for "Reporter node" says:
Cluster ingress traffic is only reported by destination nodes, and cluster egress by source nodes.
However, the opposite is happening.
Steps to reproduce the problem:
- In Network Traffic, in Query Options, select "Destination". This is the default.
- Filter on a pod where you will make a web request.
- ssh into that pod.
- Make a curl request to a web site. It's easier to see if you use an IP address to avoid DNS traffic. Example:
curl -kL https://52.200.142.250
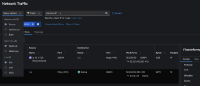
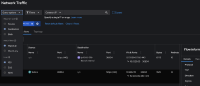
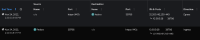
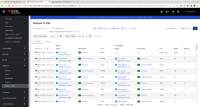
- In the Flow table, you will only see traffic from that pod going out to the Internet to dest port 443 (see 01-dest.png, 1st row). There will be no return traffic. This means it is the source node reporting egress traffic, even though "Destination" is selected.
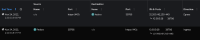
- Now in Query Options, select "Source". Do the same curl request. This time, it shows only the return traffic from the web site to your pod (see 02-source.png, 1st row). This means it is the destination node reporting ingress traffic.
- depends on
-
NETOBSERV-759 Add a way to identify agent in flows
-
- Closed
-
- is cloned by
-
NETOBSERV-1109 Reporter node behaves the opposite of what it says (conversations)
-
- Closed
-
- links to