-
Bug
-
Resolution: Unresolved
-
Undefined
-
None
-
1.2.2, 1.3
-
None
-
False
-
-
False
-
-
Description of problem:
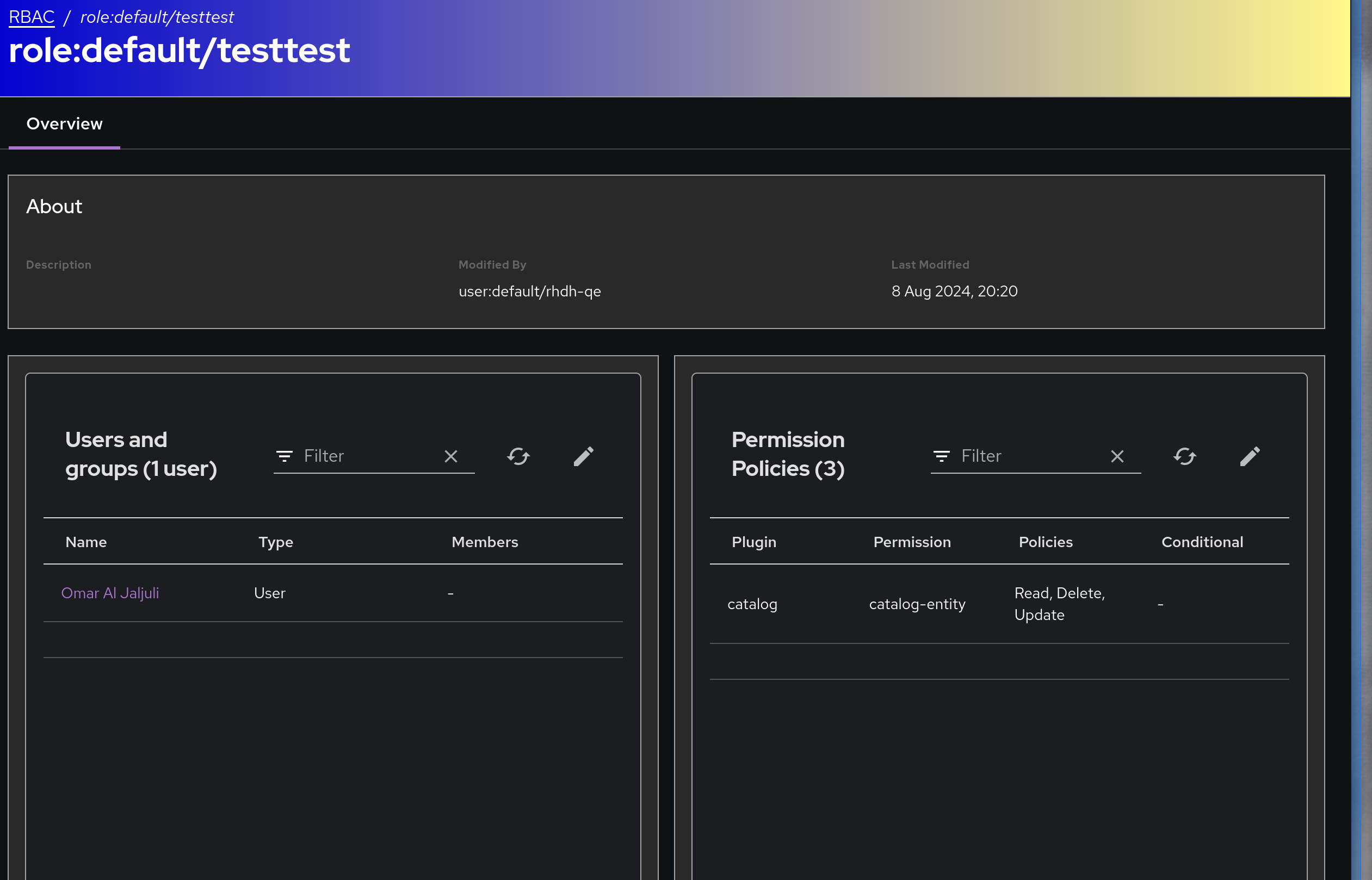
Permission policies with deny effect do not appear in UI. Checking roles with deny effect policies in the UI won't show said policy, which creates the issue of not being able to delete that policy from the UI. This is also an issue, because if you delete the role with the deny policy from the UI it will delete all it's policies except those with deny effect. Creating a role with the same name and with contradicting policies on the UI won't give you an error, but it will only show you the new non-denied policies.
While creating a permission policy with deny effect is not something that you can do in the UI component of the RBAC admin panel, you can do it using the RBAC REST API.
This could cause confusion for roles that were altered using both UI and backend RBAC REST API.
Prerequisites (if any, like setup, operators/versions):
- Using the RBAC REST API, add a permission policy to an existing role (or create a new role and add a permission policy to it) that denies access to policy
- Open RHDH and Log in with an admin user
- Navigate to Administration on the side panel and click on the RBAC tab
- Click on the role and observe no policies with deny
- Delete the role
- using the backend REST API call a GET request to get the list of all the policies and observe that the deny policy still exists
Actual results:
Expected results:
Reproducibility (Always/Intermittent/Only Once):
Build Details:
Additional info (Such as Logs, Screenshots, etc):
GET request for list of policies:
[... {"entityReference":"role:default/testtest","permission":"catalog-entity","policy":"read","effect":"deny","metadata":{"source":"rest"}},{"entityReference":"role:default/testtest","permission":"catalog-entity","policy":"read","effect":"allow","metadata":{"source":"rest"}},{"entityReference":"role:default/testtest","permission":"catalog-entity","policy":"delete","effect":"allow","metadata":{"source":"rest"}},{"entityReference":"role:default/testtest","permission":"catalog-entity","policy":"update","effect":"allow","metadata":{"source":"rest"}}
...]
In this case the permission to read catalog-entities is denied and not allowed