-
Bug
-
Resolution: Cannot Reproduce
-
Major
-
None
-
rhel-10.0
-
Yes
-
Important
-
rhel-virt-windows
-
ssg_virtualization
-
None
-
QE ack
-
False
-
False
-
-
None
-
Red Hat Enterprise Linux
-
None
-
None
-
New Test Coverage
-
-
x86_64
-
Windows
-
None
What were you trying to do that didn't work?
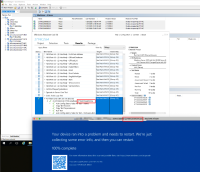
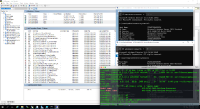
QE found a BSOD in netkvm & virtio_win_pvpanic whql tests using qemu-kvm-9.1.0-11.el10 on the ws2025 WHQL tests with prewhql271. The BSOD frequently happens when the HLK client is installed for a while. The reproduction does not need to run any netkvm tests. We just need to wait a second for the HLK client to be installed, and then BSOD happens with 100% on ws2025.
Please provide the package NVR for which bug is seen:
- CPU=AMD EPYC 7313 16-Core Processor
- virtio-win-prewhql-0.1-271
- kernel-6.12.0-41.el10.x86_64
- edk2-ovmf-20241117-1.el10.noarch
- swtpm-0.9.0-4.el10.x86_64
- qemu-kvm-core-9.1.0-10.el10.x86_64
How reproducible:
100%
Steps to reproduce
1. Boot a Win2025 VM using qemu-kvm-9.1.0-11.el10.
2. Install the HLK client(eg: \\<your_hlk_server>\HLKInstall\Client\setup.bat).
3. Wait for a while for the HLK client to be installed.
Expected results
Normal to boot.
Actual results
BSOD, Stop code is "HYPERVISOR ERROR"
Additional Notes:
- My "svm|vmx" CPU flag is always open.
- Even though one test case has passed, BSOD still happens.
- AFAIK, Xiaoling's whql test does not encounter this issue even using qemu-kvm-9.1.0-11.el10.
The whole Qemu command line:
```
/usr/libexec/qemu-kvm \
-name 271NIC256435C26 \
-enable-kvm \
-m 8G \
-smp 8 \
-uuid 9e1b9f5f-445d-4e2a-a8c1-12e449ddacb6 \
-nodefaults \
-cpu EPYC,hv_stimer,hv_synic,hv_time,hv_vpindex,hv_relaxed,hv_spinlocks=0x1fff,hv_vapic,hv_frequencies,hv_runtime,hv_tlbflush,hv_reenlightenment,hv_stimer_direct,hv_ipi,svm=on \
-chardev socket,id=charmonitor,path=/tmp/271NIC256435C26,server=on,wait=off \
-mon chardev=charmonitor,id=monitor,mode=control \
-rtc base=localtime,driftfix=slew \
-boot order=cd,menu=on \
-device piix3-usb-uhci,id=usb \
-blockdev driver=file,cache.direct=off,cache.no-flush=on,filename=271NIC256435C26,node-name=my_file \
-blockdev driver=raw,node-name=my,file=my_file \
-device ide-hd,drive=my,id=ide0-0-0,bus=ide.0,unit=0,bootindex=1 \
-blockdev driver=file,cache.direct=off,cache.no-flush=on,filename=/home/kvm_autotest_root/iso/ISO/Win2025/windows_server_2025_x64_official_dvd.iso,node-name=my_cd,read-only=on \
-blockdev driver=raw,node-name=mycd,file=my_cd,read-only=on \
-device ide-cd,drive=mycd,id=ide0-1-0,bus=ide.1,bootindex=2 \
-cdrom 271NIC256435C26.iso \
-device usb-tablet,id=input0 \
-vnc 0.0.0.0:3 \
-blockdev driver=file,cache.direct=off,cache.no-flush=on,filename=/home/kvm_autotest_root/iso/windows/FOD.iso,node-name=my_iso,read-only=on \
-blockdev driver=raw,node-name=myiso,file=my_iso,read-only=on \
-device ide-cd,drive=myiso,id=ide0-1-1,bus=ide.4 \
-blockdev node-name=file_ovmf_code,driver=file,filename=271NIC256435C26_ovmf/OVMF_CODE.secboot.fd,auto-read-only=on,discard=unmap \
-blockdev node-name=drive_ovmf_code,driver=raw,read-only=on,file=file_ovmf_code \
-blockdev node-name=file_ovmf_vars,driver=file,filename=271NIC256435C26_ovmf/OVMF_VARS.fd,auto-read-only=on,discard=unmap \
-blockdev node-name=drive_ovmf_vars,driver=raw,read-only=off,file=file_ovmf_vars \
-machine q35,pflash0=drive_ovmf_code,pflash1=drive_ovmf_vars \
-device pcie-root-port,bus=pcie.0,id=root1.0,multifunction=on,port=0x10,chassis=1,addr=0x7 \
-device pcie-root-port,bus=pcie.0,id=root2.0,port=0x11,chassis=2,addr=0x7.0x1 \
-netdev tap,script=/etc/qemu-ifup1,downscript=no,id=hostnet0 \
-device e1000e,bus=root1.0,netdev=hostnet0,id=net0,mac=00:52:0c:75:f5:22 \
-vga std \
-netdev tap,script=/etc/qemu-ifup-private,downscript=no,id=hostnet1,vhost=on \
-device virtio-net-pci,netdev=hostnet1,bus=root2.0,id=net1,speed=1000,mac=00:52:11:29:ee:3e \
-monitor telnet:localhost:3000,server,nowait
```