-
Bug
-
Resolution: Can't Do
-
Normal
-
None
-
rhel-9.6
-
None
-
No
-
Low
-
rhel-virt-tools
-
ssg_virtualization
-
3
-
False
-
False
-
-
None
-
None
-
None
-
None
-
-
x86_64
-
None
Description of problem:
v2v can't convert win11-efi-secure guest with vtpm from VMware
Version-Release number of selected component (if applicable):
virt-v2v-2.7.1-2.el9.x86_64
libguestfs-1.54.0-3.el9.x86_64
guestfs-tools-1.52.2-2.el9.x86_64
libvirt-libs-10.10.0-1.el9.x86_64
qemu-img-9.1.0-6.el9.x86_64
nbdkit-server-1.38.5-1.el9.x86_64
libnbd-1.20.3-1.el9.x86_64
How reproducible:
100%
Steps:
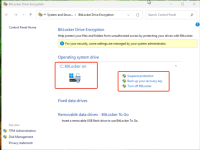
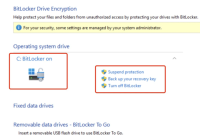
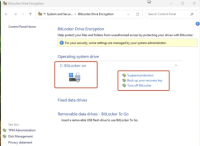
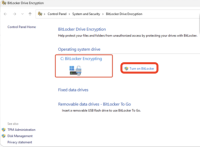
1. Install win11-efi with tpm using latest iso 'windows_11_x64_official_dvd.iso' on VMware, and can see C drive of the guest is encrypted by bitlocker even if bitlocker isn't activated, please check screenshot 'win11-with-tpm-installed-by-latest-version-iso.png'
2.Convert a win11-efi-secure guest with vtpm from VMware by virt-v2v
# virt-v2v -ic vpx://root@10.73.212.129/Folder/Datacenter/Cluster/10.73.225.34/?no_verify=1 -it vddk -io vddk-libdir=/home/vddk8.0.3 -io vddk-thumbprint=CB:9F:B1:9D:33:49:6C:60:AD:3C:A5:16:77:91:5F:CD:1B:24:B1:43 -ip /home/passwd esx8.0-win11-efi-secureboot-with-vtpm [ 0.0] Setting up the source: -i libvirt -ic vpx://root@10.73.212.129/Folder/Datacenter/Cluster/10.73.225.34/?no_verify=1 -it vddk esx8.0-win11-efi-secureboot-with-vtpm [ 1.8] Opening the source Enter key or passphrase ("/dev/sda3"): virt-v2v: could not find key to open LUKS encrypted /dev/sda3. Try using --key on the command line. Original error: cryptsetup_open: cryptsetup exited with status 1: Activation of partially decrypted BITLK device is not supported. (0)
Actual Result:
As above description
Excepted Result:
Fix the bug
Additional info:
1. v2v can convert win11-efi-secure guest without vtpm from VMware
# virt-v2v -ic vpx://non-admin%40vsphere.local@10.73.212.129/data/10.73.212.36/?no_verify=1 -it vddk -io vddk-libdir=/home/vddk8.0.3 -io vddk-thumbprint=CB:9F:B1:9D:33:49:6C:60:AD:3C:A5:16:77:91:5F:CD:1B:24:B1:43 -ip /home/passwd esx8.0-win11-x86_64-efi [ 0.0] Setting up the source: -i libvirt -ic vpx://non-admin%40vsphere.local@10.73.212.129/data/10.73.212.36/?no_verify=1 -it vddk esx8.0-win11-x86_64-efi [ 1.6] Opening the source [ 5.7] Inspecting the source [ 10.3] Checking for sufficient free disk space in the guest [ 10.3] Converting Windows 10 Enterprise (win11) to run on KVM virt-v2v: This guest has virtio drivers installed. [ 16.3] Setting a random seed virt-v2v: warning: random seed could not be set for this type of guest [ 16.3] SELinux relabelling [ 16.4] Mapping filesystem data to avoid copying unused and blank areas [ 17.9] Closing the overlay [ 18.1] Assigning disks to buses [ 18.1] Checking if the guest needs BIOS or UEFI to boot virt-v2v: This guest requires UEFI on the target to boot. [ 18.1] Setting up the destination: -o libvirt [ 19.6] Copying disk 1/1 █ 100% [****************************************] [ 547.9] Creating output metadata [ 547.9] Finishing off
- is cloned by
-
RHEL-70854 v2v can't convert win11-efi-secure guest with vtpm: "Activation of partially decrypted BITLK device is not supported" [rhel-10.0]
-
- Closed
-