-
Bug
-
Resolution: Duplicate
-
Undefined
-
None
-
rhel-9.0.0
-
None
-
Moderate
-
rhel-bootloader
-
ssg_display
-
None
-
False
-
False
-
-
None
-
None
-
None
-
None
-
If docs needed, set a value
-
-
aarch64
-
None
-
57,005
Description of problem:
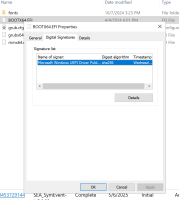
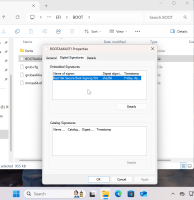
RedHat 9.0 ARM boot loader is not signed with Microsoft signature
the x86_64 ISO is good signed with Microsoft signature
we want to ask is there any reason for this?
is there a plan to fix it? e.g RHEL9.1?
Version-Release number of selected component (if applicable):
9.0
How reproducible:
[root@pek2-gosv-16-dhcp39 ~]# uname -a
Linux pek2-gosv-16-dhcp39.eng.vmware.com 5.14.0-70.13.1.el9_0.aarch64 #1 SMP Thu Apr 14 12:36:51 EDT 2022 aarch64 aarch64 aarch64 GNU/Linux
[root@pek2-gosv-16-dhcp39 ~]# keyctl list %:.builtin_trusted_keys
3 keys in keyring:
447350985: ---lswrv 0 0 asymmetric: Red Hat Enterprise Linux kernel signing key: 76e54d490ad76bac12a481dd1c97a49f459edd0a
886021945: ---lswrv 0 0 asymmetric: Red Hat Enterprise Linux kpatch signing key: 4d38fd864ebe18c5f0b72e3852e2014c3a676fc8
954122109: ---lswrv 0 0 asymmetric: Red Hat Enterprise Linux Driver Update Program (key 3): bf57f3e87362bc7229d9f465321773dfd1f77a80
compare to the example output from
https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/9/html-single/managing_monitoring_and_updating_the_kernel/index#signing-kernel-modules-for-secure-boot_managing-monitoring-and-updating-the-kernel
there is no Microsoft keys list in the builtin_trusted_keys
[root@pek2-gosv-16-dhcp39 ~]# keyctl list %:.platform
5 keys in keyring:
696217033: ---lswrv 0 0 asymmetric: VMware, Inc.: 4ad8ba0472073d28127706ddc6ccb9050441bbc7
361952854: ---lswrv 0 0 asymmetric: Red Hat Secure Boot (CA key 1): 4016841644ce3a810408050766e8f8a29c65f85c
482794800: ---lswrv 0 0 asymmetric: Microsoft Windows Production PCA 2011: a92902398e16c49778cd90f99e4f9ae17c55af53
967857386: ---lswrv 0 0 asymmetric: Microsoft Corporation UEFI CA 2011: 13adbf4309bd82709c8cd54f316ed522988a1bd4
1072875068: ---lswrv 0 0 asymmetric: VMware, Inc.: VMware Secure Boot Signing: 04597f3e1ffb240bba0ff0f05d5eb05f3e15f6d7
Actual results:
the boot loader is only signed with Microsoft Keys
and the OS will not load by default with secure boot enabled
user need manually add RedHat key to UEFI dbx to get secure boot work.
Expected results:
expect the ARM boot loader also signed with Microsoft signature
so user can enable secure boot without additional steps.
Additional info:
- is blocked by
-
RHEL-4344 Please update grub2 to support PE/COFF decompressor
-
- Closed
-
- external trackers