-
Bug
-
Resolution: Unresolved
-
Normal
-
None
-
rhel-10.2
-
No
-
Moderate
-
1
-
rhel-virt-hwe-arm-1
-
0
-
QE ack
-
False
-
False
-
-
None
-
Red Hat Enterprise Linux
-
Split items
-
None
-
None
-
Unspecified
-
Unspecified
-
Unspecified
-
-
aarch64
-
Windows
-
None
What were you trying to do that didn't work?
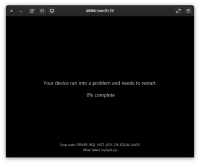
QE was attempting to test the pvpanic functionality on a Windows ARM guest by triggering a Blue Screen of Death (BSoD) via an NMI injection from the QEMU monitor, but failed with an error. A BSoD can be triggered successfully using other methods, such as Microsoft's "NotMyFault" utility.
Please provide the package NVR for which bug is seen:
- DISTRO=RHEL-10.1-20250824.1
- CPU=Ampere-1a
- pvpanic drivers Elizabeth provided, which contain binaries for both architectures.
- kernel-6.12.0-122.el10.aarch64
- swtpm-0.9.0-5.el10.aarch64
- qemu-kvm-core-10.0.0-12.el10.aarch64
How reproducible:
Always.
Steps to reproduce:
1. Start a Windows ARM VM with the pvpanic device enabled.
2. Inside the Windows guest, configure the registry to trigger a crash dump on NMI:
- Open Registry Editor (regedit).
- Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\CrashControl.
- Create a new DWORD (32-bit) Value named NMICrashDump.
- Set the value of NMICrashDump to 1.
3. From the QEMU monitor, attempt to inject an NMI to trigger the BSoD.
{"execute":"inject-nmi"}
Expected results:
The VM should receive the NMI, immediately trigger a BSoD as configured by the registry key, and generate a crash dump file.
Actual results
The NMI injection fails, and the QEMU monitor returns an error:
{"error": {"class": "GenericError", "desc": "machine does not provide NMIs"}}
Qemu cmdline:
# cat win11_01.sh
/usr/libexec/qemu-kvm \
-name guest=win11,debug-threads=on \
-blockdev '{"node-name": "file_aavmf_code", "driver": "file", "filename": "/usr/share/edk2/aarch64/QEMU_EFI-silent-pflash.raw", "auto-read-only": true, "discard": "unmap"}' \
-blockdev '{"node-name": "drive_aavmf_code", "driver": "raw", "read-only": true, "file": "file_aavmf_code"}' \
-blockdev '{"node-name": "file_aavmf_vars", "driver": "file", "filename": "/root/avocado/data/avocado-vt/avocado-vt-vm1_rhel101-aarch64-4k-virtio-scsi_qcow2_filesystem_VARS.qcow2", "auto-read-only": true, "discard": "unmap"}' \
-blockdev '{"node-name": "drive_aavmf_vars", "driver": "raw", "read-only": false, "file": "file_aavmf_vars"}' \
-m 8192 \
-smp 8 \
-cpu 'host' \
-machine virt,gic-version=host,pflash0=drive_aavmf_code,pflash1=drive_aavmf_vars,memory-backend=mem-machine_mem \
-object '{"size": 8589934592, "mem-path": "/dev/shm", "share": true, "id": "mem-machine_mem","qom-type": "memory-backend-file"}' \
-nodefaults -vnc 0.0.0.0:14 -monitor stdio -enable-kvm \
-device ramfb \
-device '{"driver":"qemu-xhci","p2":15,"p3":15,"id":"usb"}' \
-device '{"driver":"usb-tablet","id":"input0","bus":"usb.0","port":"1"}' \
-device '{"driver":"usb-kbd","id":"input1","bus":"usb.0","port":"2"}' \
-drive file=/home/kvm_autotest_root/iso/windows/winutils.iso,media=cdrom,if=none,id=drivers -device '{"driver":"usb-storage","drive":"drivers"}' \
-drive file=/home/virtio-win-prewhql-0.1-290-arm64.iso,media=cdrom,if=none,id=drivers_win -device '{"driver":"usb-storage","drive":"drivers_win"}' \
-device '{"driver":"pcie-root-port","port":8,"chassis":1,"id":"pci.1","bus":"pcie.0","multifunction":true,"addr":"0x2"}' \
-device '{"driver":"pcie-root-port","port":9,"chassis":2,"id":"pci.2","bus":"pcie.0","addr":"0x2.0x1"}' \
-device '{"driver":"pcie-root-port","port":10,"chassis":3,"id":"pci.3","bus":"pcie.0","addr":"0x2.0x2"}' \
-device '{"driver":"pcie-root-port","port":11,"chassis":4,"id":"pci.4","bus":"pcie.0","addr":"0x2.0x3"}' \
-device '{"driver":"pcie-root-port","port":12,"chassis":5,"id":"pci.5","bus":"pcie.0","addr":"0x2.0x4"}' \
-blockdev '{"driver":"file","filename":"/home/win11_01.qcow2","node-name":"libvirt-2-storage","auto-read-only":true,"discard":"unmap"}' \
-blockdev '{"node-name":"libvirt-2-format","read-only":false,"discard":"unmap","driver":"qcow2","file":"libvirt-2-storage","backing":null}' \
-device '{"driver":"virtio-scsi-pci","bus":"pci.3","addr":"0x0"}' \
-device '{"driver": "scsi-hd", "id": "image1", "drive": "libvirt-2-format", "write-cache": "on"}' \
-netdev '{"type":"tap","id":"hostnet0"}' \
-device '{"driver":"virtio-net-pci","netdev":"hostnet0","id":"net0","mac":"52:54:00:dc:d6:7d","bus":"pci.4","addr":"0x0"}' \
-device '{"driver":"virtio-gpu-pci","id":"video0","max_outputs":1,"bus":"pci.5","addr":"0x0"}' \
-chardev socket,id=chrtpm,path=/tmp/guest-swtpm14.sock \
-device '{"driver":"tpm-tis-device","tpmdev":"tpm-tpm0","id":"tpm0"}' \
-tpmdev emulator,id=tpm-tpm0,chardev=chrtpm \
-qmp tcp:localhost:4444,server,wait=off \
-device '{"driver": "vmcoreinfo"}' \
-device pvpanic-pci,bus=pcie.0,addr=0x7
- relates to
-
RHEL-115784 [virtio-win] Create a test package of pvpanic that combine pvpanic and pvpanic-pci
-
- Release Pending
-