-
Bug
-
Resolution: Done-Errata
-
Undefined
-
rhel-9.6
-
openscap-1.3.13-1.el9_7
-
No
-
Important
-
rhel-security-compliance
-
2
-
False
-
False
-
-
No
-
None
-
Pass
-
Manual
-
Unspecified Release Note Type - Unknown
-
Unspecified
-
Unspecified
-
Unspecified
-
None
What were you trying to do that didn't work?
I was trying to review compliance checks in an OpenSCAP generated HTML report (STIG profile) and expected the output to show the correct mapping between regex patterns and the target filepaths.
What is the impact of this issue to you?
This causes confusion when interpreting results
 Please provide the package NVR for which the bug is seen:
Please provide the package NVR for which the bug is seen:
scap-security-guide-doc-0.1.76-1.el9.noarch
openscap-1.3.12-1.el9_6.x86_64
How reproducible is this bug?:
100% reproducible.
Steps to reproduce
Run a scan using oscap with STIG profile:
oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_stig --report /tmp/stig.html /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
Open stig.html in a browser.[^stig.html]
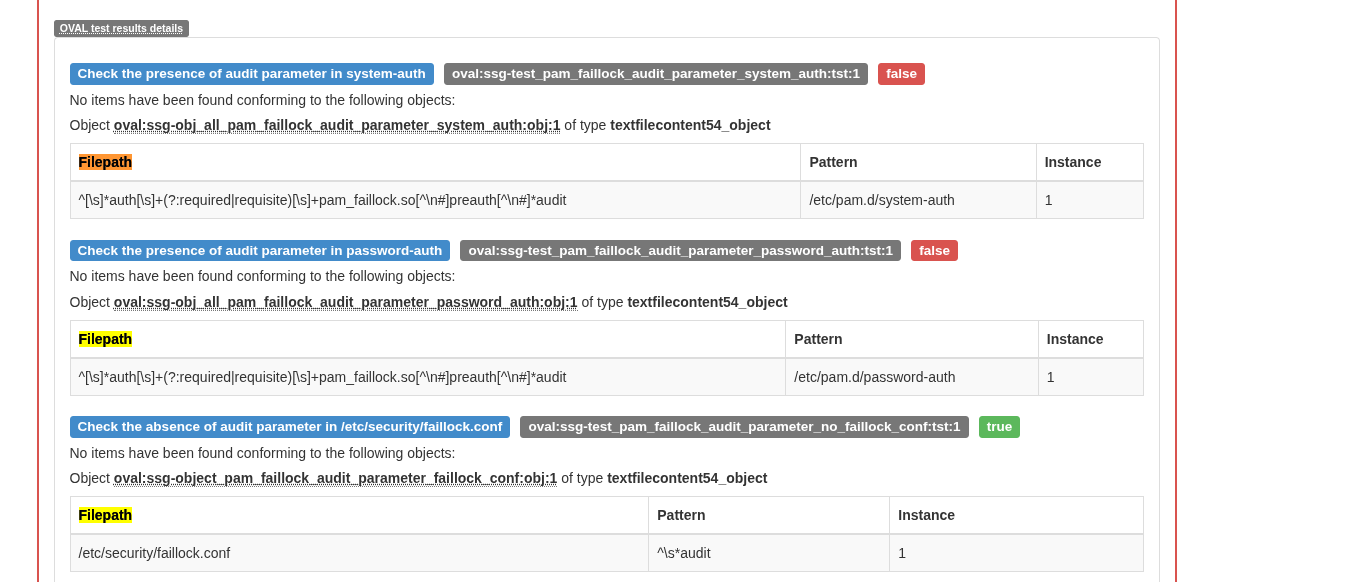
Locate columns with Filepath | Pattern | Instance fielld.
$ grep -E '<tr><td>[^<]*[\\^.*].*</td><td>/etc/.*</td>' stig.html <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^[\s]*auth[\s]+(?:required|requisite)[\s]+pam_faillock.so[^\n#]preauth[^\n#]*audit</td><td>/etc/pam.d/system-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the presence of audit parameter in password-auth</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^[\s]*auth[\s]+(?:required|requisite)[\s]+pam_faillock.so[^\n#]preauth[^\n#]*audit</td><td>/etc/pam.d/password-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the absence of audit parameter in /etc/security/faillock.conf</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^[\s]*auth[\s]+(?:required|requisite)[\s]+pam_faillock.so[^\n#]preauth[^\n#]*audit</td><td>/etc/pam.d/system-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the absence of audit parameter in password-auth</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^[\s]*auth[\s]+(?:required|requisite)[\s]+pam_faillock.so[^\n#]preauth[^\n#]*audit</td><td>/etc/pam.d/password-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the expected audit value in in /etc/security/faillock.conf</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^\s*auth\N+pam_unix\.so</td><td>/etc/pam.d/system-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">no more that one pam_unix.so is expected in auth section of password-auth</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^\s*auth\N+pam_unix\.so</td><td>/etc/pam.d/password-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">One and only one occurrence is expected in auth section of system-auth</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td><table><tr><td>3</td></tr><tr><td>^[\s]*auth[\s]+.+[\s]+pam_faillock.so[\s]+[^\n]*deny=([0-9]+)</td></tr></table></td><td>/etc/pam.d/system-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the expected deny value in password-auth</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td><table><tr><td>3</td></tr><tr><td>^[\s]*auth[\s]+.+[\s]+pam_faillock.so[\s]+[^\n]*deny=([0-9]+)</td></tr></table></td><td>/etc/pam.d/password-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the absence of deny parameter in /etc/security/faillock.conf</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^[\s]*deny[\s]*=[\s]*([0-9]+)</td><td>/etc/security/faillock.conf</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the absence of deny parameter in system-auth</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^[\s]*auth[\s]+.+[\s]+pam_faillock.so[\s]+[^\n]*deny=([0-9]+)</td><td>/etc/pam.d/system-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the absence of deny parameter in password-auth</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^[\s]*auth[\s]+.+[\s]+pam_faillock.so[\s]+[^\n]*deny=([0-9]+)</td><td>/etc/pam.d/password-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the expected deny value in /etc/security/faillock.conf</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td><table><tr><td>900</td></tr><tr><td>^[\s]*auth[\s]+.+[\s]+pam_faillock.so[\s]+[^\n]*fail_interval=([0-9]+)</td></tr></table></td><td>/etc/pam.d/system-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the expected fail_interval value in password-auth</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td><table><tr><td>900</td></tr><tr><td>^[\s]*auth[\s]+.+[\s]+pam_faillock.so[\s]+[^\n]*fail_interval=([0-9]+)</td></tr></table></td><td>/etc/pam.d/password-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the absence of fail_interval parameter in /etc/security/faillock.conf</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^[\s]*fail_interval[\s]*=[\s]*([0-9]+)</td><td>/etc/security/faillock.conf</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the absence of fail_interval parameter in system-auth</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^[\s]*auth[\s]+.+[\s]+pam_faillock.so[\s]+[^\n]*fail_interval=([0-9]+)</td><td>/etc/pam.d/system-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the absence of fail_interval parameter in password-auth</span> <strong>textfilecontent54_object</strong></h5><table class="table table-striped table-bordered"><thead><tr><th>Filepath</th><th>Pattern</th><th>Instance</th></tr></thead><tbody><tr><td>^[\s]*auth[\s]+.+[\s]+pam_faillock.so[\s]+[^\n]*fail_interval=([0-9]+)</td><td>/etc/pam.d/password-auth</td><td>1</td></tr></tbody></table><h4><span class="label label-primary">Check the expected fail_interval value in /etc/security/faillock.conf</span>
Expected results
- Filepath" column should show actual file locations, like /etc/pam.d/system-auth
- "Pattern" column should show the regex used to check those files
Actual results
The columns are inverted: regex appears under "Filepath", and actual filepath under "Pattern"
- links to
-
 RHBA-2025:157153
openscap bug fix and enhancement update
RHBA-2025:157153
openscap bug fix and enhancement update