-
Bug
-
Resolution: Done
-
Normal
-
None
-
None
-
None
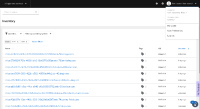
I have a user that is not assigned in any group. The user is not an org admin and the "Custom default access" group is modified to have no roles at all.
If I log in as an org admin user from the same organization as the user mentioned above and navigate to User Access -> Users and there I click on the non org admin user, it doesn't show any permissions and it says "To configure user access to applications create at least one role". This all looks right in the UI, but the issue appears in the API.
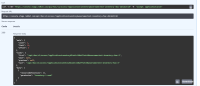
If I call the RBAC API on the "/access" endpoint and I try to get permissions for my non org admin user, I'll get following results:
GET /access/?application=inventory&username=test-inventory-rbac-2&limit=10
{
"meta": {
"count": 1,
"limit": 10,
"offset": 0
},
"links": {
"first": "/api/rbac/v1/access/?application=inventory&limit=10&offset=0&username=test-inventory-rbac-2",
"next": null,
"previous": null,
"last": "/api/rbac/v1/access/?application=inventory&limit=10&offset=0&username=test-inventory-rbac-2"
},
"data": [
{
"resourceDefinitions": [],
"permission": "inventory:*:read"
}
]
}
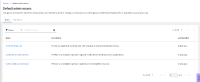
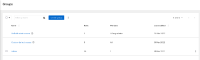
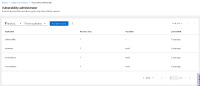
So it returns a permission, even though the user is not assigned to any custom group and the "Custom default access" group has no permissions. If I look at the "Default admin access" group, there is a "Vulnerability administrator" role which includes "inventory:*:read" permission, so I think that's where the permission is coming from. This is a bug, because the "test-inventory-rbac-2" is not an org admin and so should not have permissions from the "Default admin access" group.
All of the above was observed in Stage.
Account number: 6389571
Org admin username: test-inventory-rbac
Non org admin username: test-inventory-rbac-2
- relates to
-
RHCLOUD-19296 RBAC UI says that all users are members of "Default admin access" group
-
- Closed
-
-
RHCLOUD-19297 [RFE] Ability to update "Default admin access" group
-
- Closed
-