-
Feature Request
-
Resolution: Unresolved
-
Major
-
None
-
openshift-4.17.z
-
None
-
Product / Portfolio Work
-
None
-
False
-
-
None
-
None
-
None
-
-
None
-
None
-
None
-
None
-
None
1. Proposed Title of the Feature Request
Enhance OpenShift GitOps (RHOG) operator images to address compliance findings for non-root container execution and removal of example SSL certificate/key files flagged by security scanners
2. Nature and Description of the Request
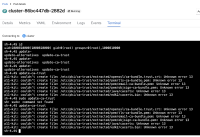
The customer has reported compliance issues detected by a third-party image scanning tool (Twistlock) against the OpenShift GitOps (RHOG) operator images. These findings are reported as compliance violations, not explicit CVEs.
Customer mentioned this as request to resolve and provide tentative date for release of RHOG operator images in v1.16 or v1.18 with fix for the compliance issues.
Compliance Findings Reported by Customer
- Container running as root user (gitops-rhel8){}
-
- Presence of SSL certificate and key files under /usr/share/doc (argocd-rhel8)*
Customer scanner output:
- Presence of SSL certificate and key files under /usr/share/doc (argocd-rhel8)*
/usr/share/doc/perl-IO-Socket-SSL/certs/client-key.enc
/usr/share/doc/perl-IO-Socket-SSL/certs/client-key.pem
/usr/share/doc/perl-IO-Socket-SSL/certs/proxyca.pem
/usr/share/doc/perl-IO-Socket-SSL/certs/server-ecc-key.pem
/usr/share/doc/perl-IO-Socket-SSL/certs/server-key.enc
/usr/share/doc/perl-IO-Socket-SSL/certs/server-key.pem
/usr/share/doc/perl-IO-Socket-SSL/certs/server-wildcard.pem
/usr/share/doc/perl-IO-Socket-SSL/certs/server2-key.pem
/usr/share/doc/perl-IO-Socket-SSL/certs/sub-server.pem
/usr/share/doc/perl-Net-SSLeay/examples/server_key.pem
– argocd-rhel8
The customer’s compliance tooling flags their presence as potential sensitive material.
Affected RHOG Operator Images (Customer Provided)
- registry.redhat.io/openshift-gitops-1/gitops-rhel8@sha256:1a4d9d6d6c917a161fa3797fedf722a1ba9211eaa4c52cf976bebb629eabe40c
- registry.redhat.io/openshift-gitops-1/argocd-rhel8@sha256:1935460f871ad2cc9fe097e1a7e32a67b4b4a3c58aa0412cffc28823f4ffb49f
Additional Customer Context
- Business Impact: Compliance Issue
- Scanning Tool: Twistlock image scanner
- CVE Association:{}
- Customer confirmed no CVE is directly reported for the above findings
- Findings are categorized strictly as compliance violations{}
- Recent Updates/Changes: Unknown
- Troubleshooting Performed:{}
- Customer attempted to identify associated CVEs
- No CVEs found; findings remain compliance-only
- When did the issue start:{}
- 2025-12-23T04:47:17+00:00
3. Why Does the Customer Need This? (Business Requirements)
- The customer operates in a regulated, compliance-driven environment where container images must pass automated security and compliance scans.
- Third-party tooling (Twistlock) blocks or flags deployments due to:
- Containers running as root
- Presence of certificate/key files, even if unused
- Although no active vulnerabilities are present, the findings require:
- Formal risk acceptance, or
- Engineering remediation in vendor-provided images
- The customer is requesting official remediation in Red Hat–provided RHOG images rather than:
- Maintaining custom image rebuilds
- Creating scanner exceptions
- The customer specifically asked for fixes to be considered in RHOG operator versions v1.16 or v1.18 (or later) and for a tentative release timeline.
4. Affected Packages or Components
Images
- openshift-gitops-1/gitops-rhel8
- openshift-gitops-1/argocd-rhel8
Components
- OpenShift GitOps (RHOG) Operator
- Argo CD container image
- RHEL8 base image configuration
- relates to
-
GITOPS-8929 Remove unused packages and depednency in GitOps component images
-
- New
-