-
Feature Request
-
Resolution: Unresolved
-
Undefined
-
None
-
None
-
None
-
None
-
Product / Portfolio Work
-
None
-
False
-
-
None
-
None
-
None
-
-
None
-
None
-
None
-
None
-
None
Goal Summary
OpenShift 4.20 introduces support for mounting Open Container Initiative (OCI) compliant images or artifacts directly into pods using image volumes. This allows workloads to access files from an OCI registry without embedding them in the base image.
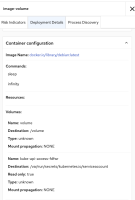
Currently, RHACS does not detect or classify this volume type, showing it as unknown. This RFE requests adding native RHACS support to identify, scan, and control OCI image volumes.
Goals and Expected User Outcomes
• RHACS should recognize and display OCI image volumes as a specific type (e.g., imageVolume).
• Security teams gain visibility into which pods use OCI image volumes and from which registries.
• Policies and admission controls can be extended to validate and block untrusted or unsigned OCI references.
• RHACS vulnerability scanning should be extended to analyze the contents of OCI image volumes, including binaries (e.g., Go executables), JAR files, and libraries, ensuring no vulnerable or unapproved components are introduced through mounted images.
Acceptance Criteria
• OCI-based volumes (volumes.image.reference) are detected and labeled as imageVolume.
• RHACS UI and API show the registry, image reference, and mount path.
• Policies can restrict usage to trusted registries or signed images.
• RHACS Scanner can inspect OCI volume contents for known vulnerabilities in binaries, JARs, and libraries.
Success Criteria / KPIs
• 100% of pods using OCI image volumes are detected.
• Admission control blocks policy violations (e.g., untrusted sources).
• Vulnerability scans successfully detect issues in mounted OCI volume content.
Use Case Example
https://docs.redhat.com/en/documentation/openshift_container_platform/4.20/html-single/nodes/index#nodes-pods-image-volume
Currently, RHACS shows:
Type: unknown
This allows OCI-mounted content to bypass both detection and vulnerability scanning, introducing potential security blind spots.