-
Feature Request
-
Resolution: Unresolved
-
Undefined
-
None
-
None
-
None
-
None
-
Product / Portfolio Work
-
None
-
False
-
-
None
-
None
-
-
-
-
-
None
-
-
None
Update: Until this capability is available, use this KCS and the attached whitepaper to share with the customer inquiring about Malware detection: https://access.redhat.com/solutions/7049002
--------------------------------
CUSTOMER PROBLEM
Customers who must comply with PCI-DSS regulations work with auditors who take the PCI-DSS requirements for antimalware scanning literally. To comply with their auditors requirements, they must demonstrate use of a malware scanning solution. Customers would like to have malware scanning added to RHACS capabilities.
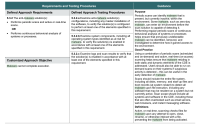
The solution must address the following PCI-DSS v4 requirements. The following is extracted from the PCI-DSS v4 requirements document, requirement 5, page 111.
- 5.2 Malicious software (malware) is prevented, or detected and addressed.
- 5.3 Anti-malware mechanisms and processes are active, maintained, and monitored.
Screenshots from the document are attached for additional detail.
USERS
End-users are RHACS users / cluster admins / security teams and compliance teams.
ACCEPTANCE CRITERIA
MVP Solution - Phase 1
- The solution can be deployed on one or more OpenShift clusters.
- The solution can evaluate images deployed on OpenShift
- The solution can evaluate RHCOS nodes
- The solution performs periodic scans on a running cluster at a pre-defined interval (Daily , weekly, monthly)
- A real-time scan can be initiated by the end user
- The solution reports its results in a human readable format. Options for the MVP can include a .csv file.
- A log of scans run with timestamps and links to output
 is maintained
is maintained - The solution can be kept current with updated malware data (e.g. malware signatures)
Improvements - Phase 2
- Policies can be defined for solution results
- Alerts can be fired on solutions results
- Malware updates can be automated and scheduled on a regular basis
- Solution results are visible in the RHACS console and can be filtered and sorted
- A report in .csv format can be exported from the RHACS console
- End-users are able to configure the scan interval
Improvements - Phase 3
- Solution results can be leveraged in an overall risk calculation
CI - MUST be running successfully with tests automated
Release Technical Enablement
-
- End-user documentation must be available
- Slides for CEE enablement must exist and a training session must be scheduled
- Slides for field enablement must exist and be shared with the field
QUESTIONS
This section should specify what questions we are trying to answer for the customer with this set of features.
ACTIONS
Enable customers to provide a regular malware scanning report to their compliance auditors.
CONSIDERATIONS
In the future, we may want to offer malware scanning at build time and enable deploy-time policies.
UX/UI
Generally mocks should be attached to individual stories. However, if mocks combine multiple individual stories in order to enable the best user interaction, then the mocks should be linked here and this section should denote which stories are encompassed by the mocks.
DELIVERY PRIORITY
This section should outline the desired order of delivery for stories comprising this epic.