-
Feature Request
-
Resolution: Won't Do
-
Normal
-
None
-
None
-
None
-
None
-
Product / Portfolio Work
-
None
-
False
-
-
None
-
None
-
None
-
None
-
None
-
None
-
None
-
None
-
None
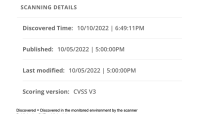
,1. CVE detection date as a timer for policy enforcement
2. Customer is developing a vulnerability lifecycle process allow time to rebuild business applications with CVEs present. CVE date will be the key used to begin a vulnerability lifecycle to track against SLA level enforcement. Example: A policy needs to be created to enforce CVEs at 30/60/90 days. That policy will use the CVE detection date as day 1 and policy will enforce at X amount of days, allowing an SLA for image updates.
3. Business requirement is to work develop an SLA for image update, development, testing and promotion through Dev/Pre-prod/Prod environments. This SLA provides multiple dates, depending on the environment. Successful development of the request will be that a policy can be developed to enforce based on CVE detection time.
4. Red Hat Advanced Cluster Security