-
Feature Request
-
Resolution: Not a Bug
-
Normal
-
None
-
rhacs-3.x
-
None
-
Product / Portfolio Work
-
None
-
False
-
-
None
-
None
-
None
-
None
-
None
-
None
-
None
-
None
-
None
USER PROBLEM
The customer wants to integrate seccomp profiles and control with ACS policy which deployment or container doesn't have seccomp profile.
Reproduce:
Firstly, you should copy the attached JSON to /var/lib/kubelet/seccomp/ directory. (If you have 1 or more node, you should copy this json to all nodes related directory.
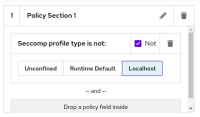
Then you should run a pod. You can use the attached pod.YAML file. Then, let's create acs policy, You can create a policy like the attached acs1.jpg screenshot.
According to this policy, I expect the ACS show violation which doesn't have any seccomp policy. But It cannot show.
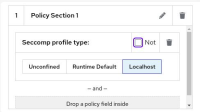
However, when you create a policy like acs2.jpg screenshot, ACS shows the containers which have a seccomp profile.