-
Feature Request
-
Resolution: Won't Do
-
Major
-
None
-
None
-
None
-
Product / Portfolio Work
-
None
-
False
-
-
None
-
None
-
-
None
-
None
-
None
-
None
-
None
-
None
-
None
1. Proposed title of this feature request
CMPv2 support for certificate management in OpenShift.
2. What is the nature and description of the request?
In RHEL 9, support has been added for better certificate management via Certificate Management Protocol (CMP, RFC 4210), the Certificate Request Message Format (CRMF), and HTTP transfer (RFC 6712). CMP messages are self-contained with protection independent of transfer mechanism, therefore they support end-to-end security. Request is to provide CMPv2 support in the solutions using certificates in OpenShift based applications. If the functionality has already been developed in RHEL/RHCOS, the thought was that it may be possible that all that is needed is kernel modification or perhaps they would need userspace packages as well for Openshift.
Certificate Management Requirements:
A. Securing the DU-CU interface
The interface between the DU and the CU must be secured by IPsec as per 3GPP. The DU and/or CU NF will have CMPv2 functionality which will enroll/ renew the TLS certs with the operator CA*. Today, most operator CAs support CMPv2 because this is the protocol specified in 3GPP.
*The operator CA refers to the Certificate Authority (CA) server of the Telco Service Provider
B. Accessing OpenShift services/interfaces
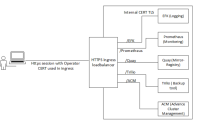
The current framework in OpenShift only provides manual operator CERT configuration option but not automatic enrollment or renewal. Our understanding is the implementation would be based on using OpenShift’s HTTPS load balancer for all external communication to internal services (as logging, monitoring, mirror/registry, backups, ACM, etc, :
<see attached - Figure1>
In this scenario, clarification will be needed during feature development regarding how this HTTPS load balancer will obtain operator CERT over CMPv2. Will it use TLS termination and/or key management?
CMPv2 has two options one is with Vendor CA and another is PSK option. Ideally both options are supported.
CMPv2 specifies following features:
- Certificate enrollment
- Certificate update
- Own certificate revocation
- Cross certification request
- Key pair recovery
3. Why is this needed? (List the business requirements here)
Security/Compliance- RAN deployments have benefited from the standardization of CMPv2 to be used for automated certificate management. Operator X.509 certificates are used for mutual authentication while establishing secure connections using IPsec and TLS protocols.
All network elements in an Open RAN, i.e. O-CU-CP, O-CU-UP O-DU and O-RU, support X.509 certificate-based authentication and related features such as auto-enrollment and auto-re-enrollment with an operator Certificate Authority (CA) server using a protocol such as 3GPP-specified CMPv2.
Like any micro-service, the expectation will be to use CA signed X.509 certificates to authenticate before communicating over the E2 interface of an O-CU-CP, O-CU-UP and O-DU performs a CMPv2-based certificate enrollment procedure in compliance with 3GPP with the CA server to obtain an operator certificate. The operator certificate is used for subsequent authentication when establishing an IPSec or a TLS connection.
4. List any affected packages or components.?
Openshift, Cert-Manager