Description:
This is an issue of Quay 3.8.0 new feature "superuser full access", when enable flags "FEATURE_SUPERUSERS_FULL_ACCESS: true" and "FEATURE_RESTRICTED_USERS: true", and put user "tom001" on the white list, this normal user can create orgs and repo, superuser can view the organizations of this normal users on new UI, but can't create new repo under this user's organization, Pls review this issue.
FEATURE_RESTRICTED_USERS: true FEATURE_SUPERUSERS_FULL_ACCESS: true RESTRICTED_USERS_WHITELIST: - tom001 SUPER_USERS: - quay
Quay Image: quay-operator-bundle-container-v3.8.0-116
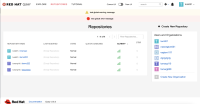
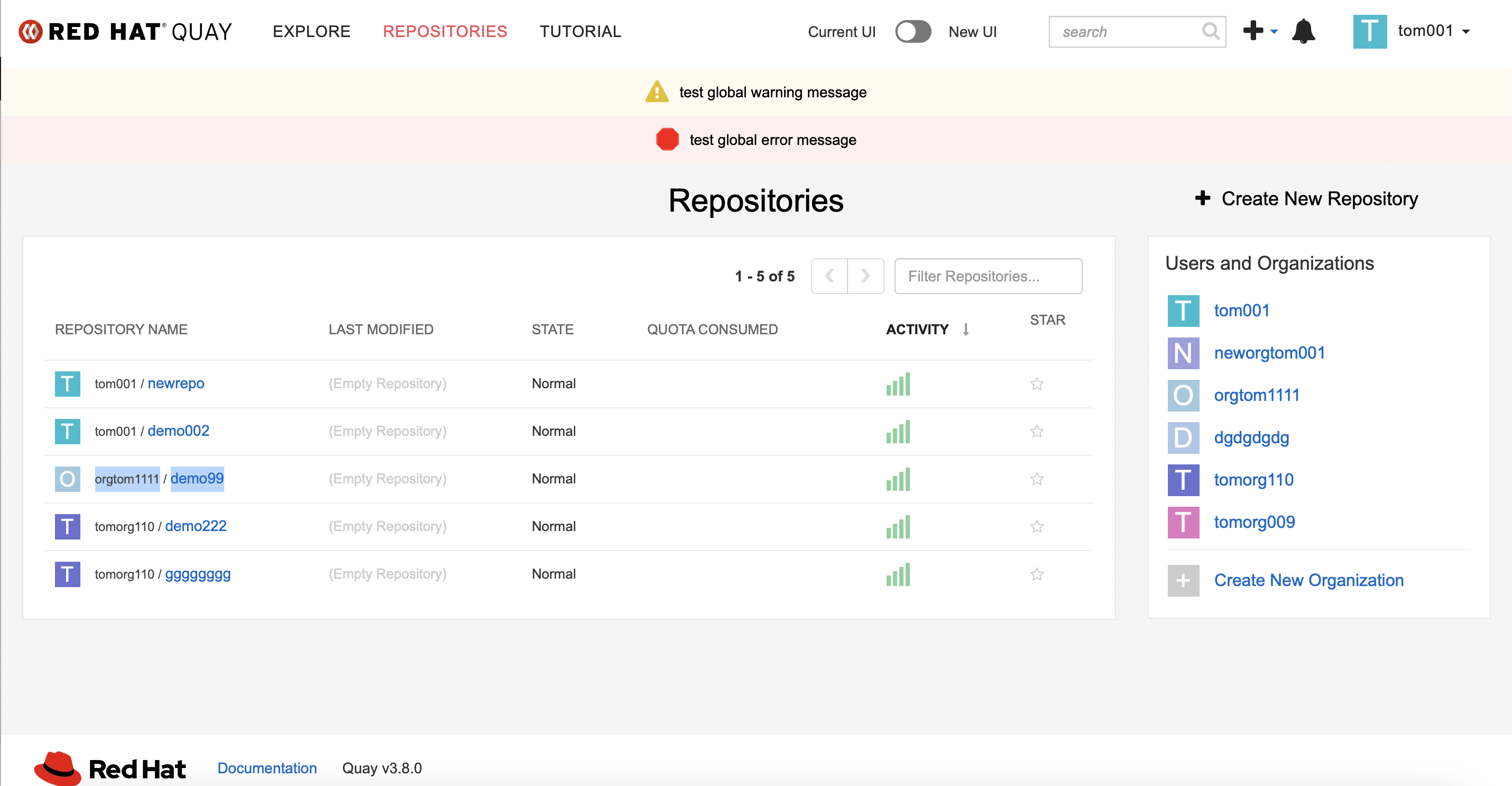
Normal user on the restricted white list can create org and repos:
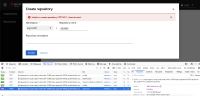
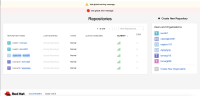
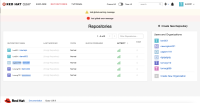
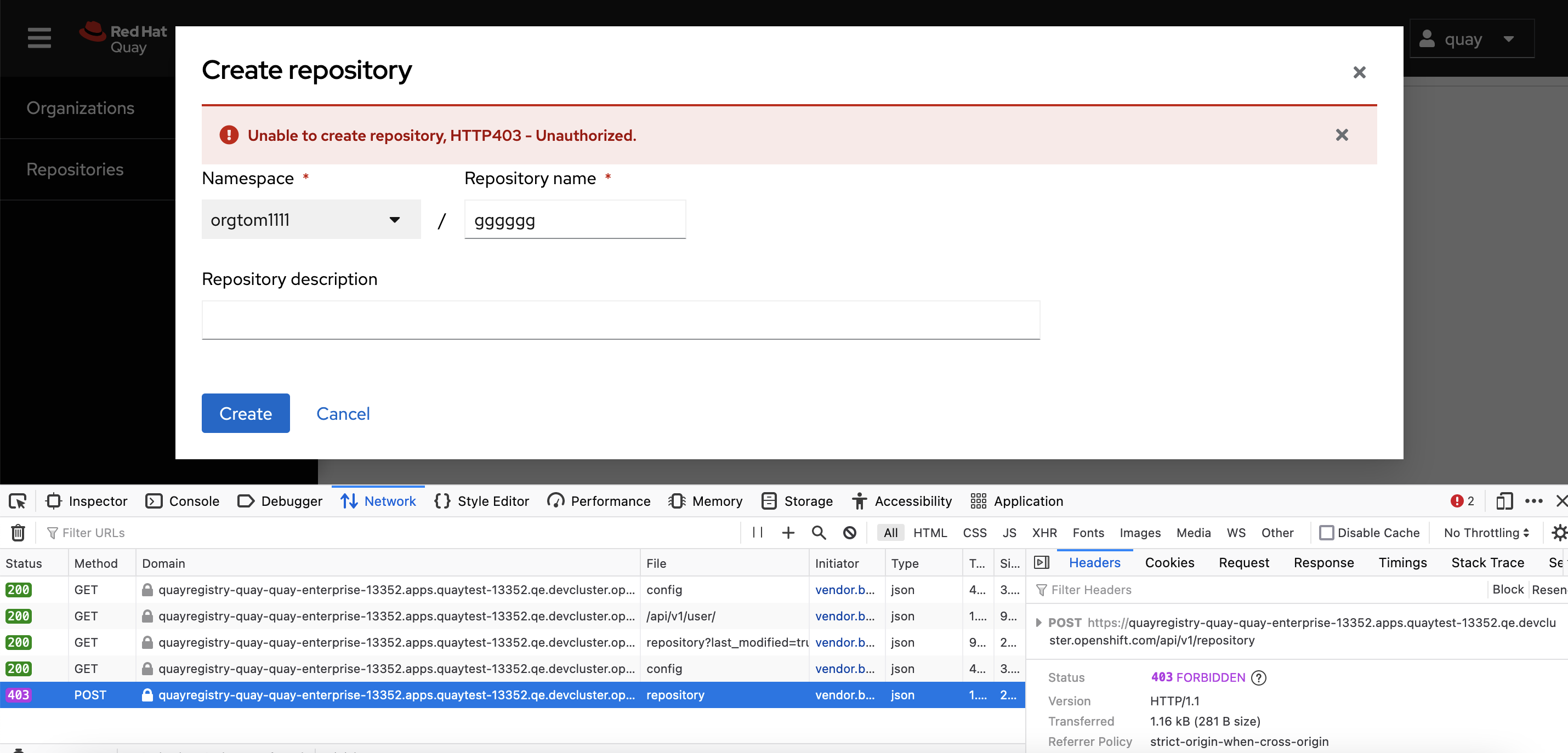
Superuser can't create new repo under normal user's organization when the normal user is on the restricted user white list:
ALLOW_PULLS_WITHOUT_STRICT_LOGGING: false AUTHENTICATION_TYPE: Database BROWSER_API_CALLS_XHR_ONLY: false BUILDLOGS_REDIS: host: quayregistry-quay-redis port: 6379 CREATE_NAMESPACE_ON_PUSH: true CREATE_PRIVATE_REPO_ON_PUSH: true CREATE_REPOSITORY_ON_PUSH_PUBLIC: true DATABASE_SECRET_KEY: wSb5IWTYs88Vkr4M2FXAKMmzub8s-Yu9cTPXcgcxZhgkvVUShorF7vss3VdBdblfJWt09AH-GYfsoFaK DB_CONNECTION_ARGS: autorollback: true threadlocals: true DB_URI: postgresql://quayregistry-quay-database:5E2sO0DQbD2-NqUM5GqJZtoBzcO4y7yhZ2uQ36MrGtkFxdUBxGf38R54aF5X93pm2wuMhNFHmrPfIIQb@quayregistry-quay-database:5432/quayregistry-quay-database DEFAULT_TAG_EXPIRATION: 2w DISTRIBUTED_STORAGE_CONFIG: default: - S3Storage - host: s3.us-east-2.amazonaws.com s3_access_key: ****** s3_bucket: quayaws13352 s3_secret_key: ****** storage_path: /datafile DISTRIBUTED_STORAGE_DEFAULT_LOCATIONS: - default DISTRIBUTED_STORAGE_PREFERENCE: - default ENTERPRISE_LOGO_URL: /static/img/RH_Logo_Quay_Black_UX-horizontal.svg EXTERNAL_TLS_TERMINATION: true FEATURE_BUILD_SUPPORT: false FEATURE_DIRECT_LOGIN: true FEATURE_EXTENDED_REPOSITORY_NAMES: true FEATURE_GENERAL_OCI_SUPPORT: true FEATURE_HELM_OCI_SUPPORT: true FEATURE_MAILING: false FEATURE_PROXY_CACHE: true FEATURE_PROXY_STORAGE: true FEATURE_QUOTA_MANAGEMENT: true FEATURE_REPO_MIRROR: true FEATURE_RESTRICTED_USERS: true FEATURE_SECURITY_NOTIFICATIONS: true FEATURE_SECURITY_SCANNER: true FEATURE_SUPERUSERS_FULL_ACCESS: true FEATURE_UI_V2: true FEATURE_USER_INITIALIZE: true PREFERRED_URL_SCHEME: https REGISTRY_TITLE: Red Hat Quay REGISTRY_TITLE_SHORT: Red Hat Quay REPO_MIRROR_INTERVAL: 30 REPO_MIRROR_TLS_VERIFY: true RESTRICTED_USERS_WHITELIST: - tom001 SECRET_KEY: lZCHPxNBwplPDOghYNfnj7tsgwD-2XkEBTZQstKc4MqjotXerZ7lVkag8rUoGBIsjLji4GTXl81Pi2cD SECURITY_SCANNER_INDEXING_INTERVAL: 30 SECURITY_SCANNER_V4_ENDPOINT: http://quayregistry-clair-app.quay-enterprise-13352.svc.cluster.local SECURITY_SCANNER_V4_NAMESPACE_WHITELIST: - admin SECURITY_SCANNER_V4_PSK: bTNDcnJNMDhPZU91M2xidTZnaUJRWkNLZklER0JOMHU= SERVER_HOSTNAME: quayregistry-quay-quay-enterprise-13352.apps.quaytest-13352.qe.devcluster.openshift.com SETUP_COMPLETE: true SUPER_USERS: - quay TAG_EXPIRATION_OPTIONS: - 2w TEAM_RESYNC_STALE_TIME: 60m TESTING: false USER_EVENTS_REDIS: host: quayregistry-quay-redis port: 6379
- is related to
-
PROJQUAY-4750 Quay superuser can't create new image repo under normal user's organization or normal user's namespace on new UI when enabled superuser full access
-
- New
-