-
Bug
-
Resolution: Obsolete
-
Major
-
None
-
quay-v3.7.9, quay-v3.8.0
-
False
-
-
False
Description of problem:
The keystone authentication doesn't work for getting user token in loop.
Version-Release number of selected component (if applicable):
quay 3.7.9
quay 3.8.0
How reproducible:
always
Steps to Reproduce:
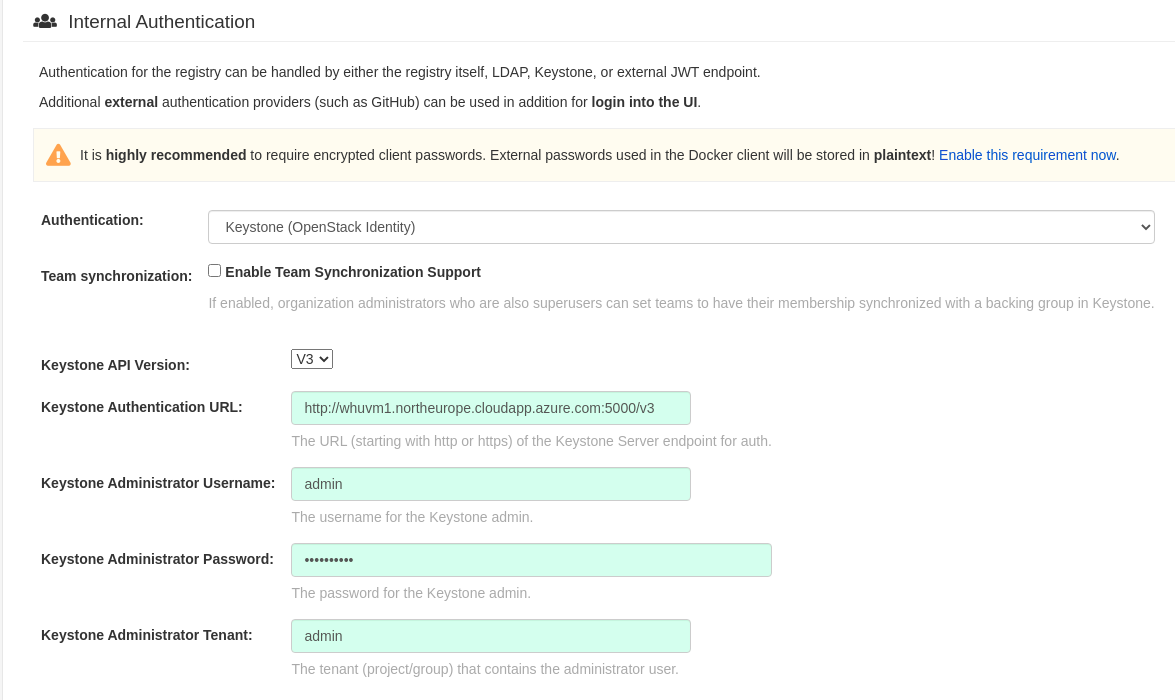
1. enable keystone authentication in config-tool UI
Keystone API Version: v3
Keystone Authentication URL: http://whuvm1.northeurope.cloudapp.azure.com:5000/v3
Keystone Administrator Username: admin
Keystone Administrator Password: ADMIN_PASS
Keystone Administrator Tenant: admin
2. reconfigure the quay
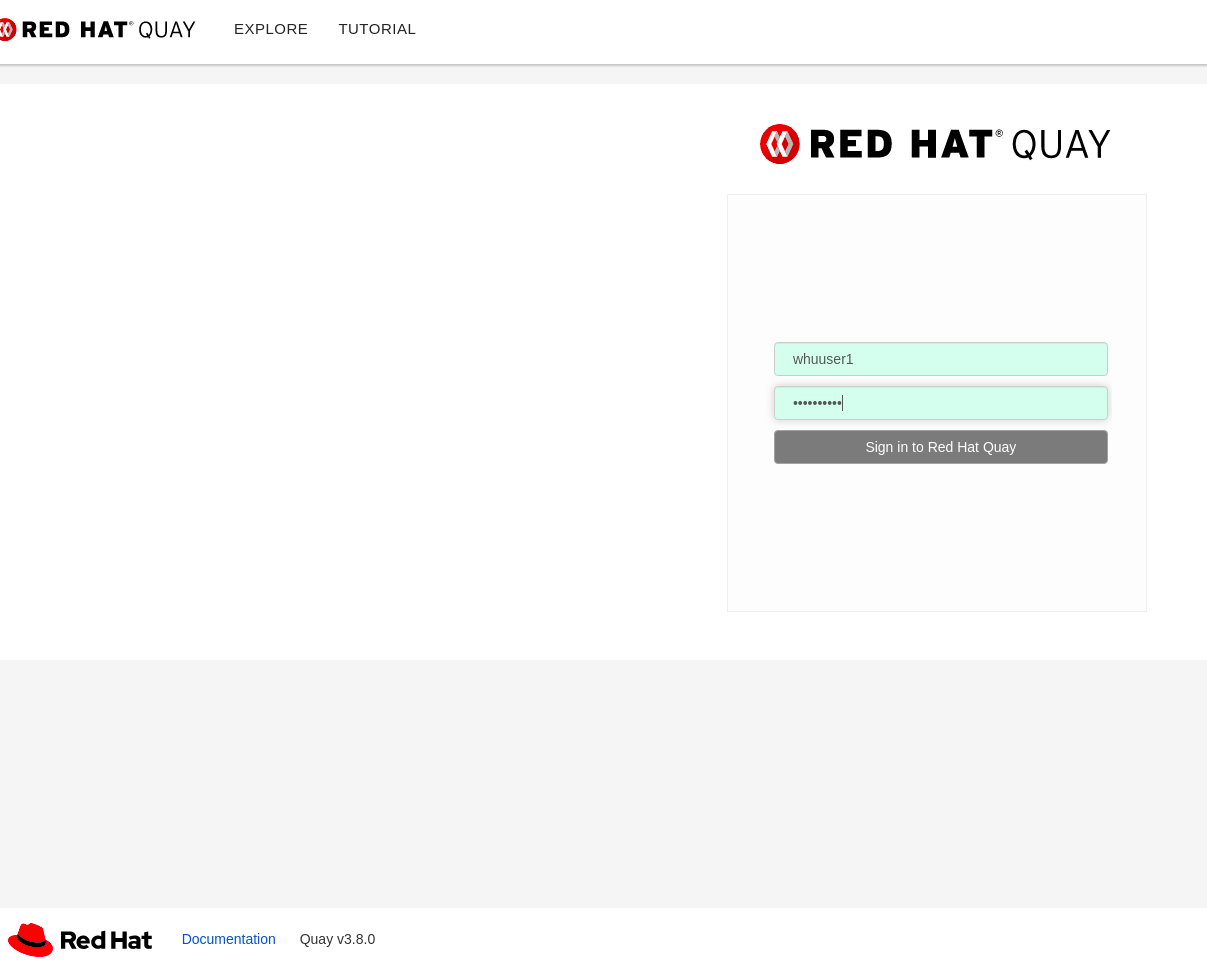
3. use keystone user to log in quay
Actual results:
The login process will be stuck at getting user token. The login page will stop here.
Expected results:
The keystone authentication should be successful.
Additional info:
In test environment, set up a keystone server like below
* Set up a VM in any cloud platform(Operating system : Linux (redhat 8.6)), open 5000 port to public network, start a keystone service by keystone image
------------------------------ $ podman run -d --rm --name keystone --net host -e IPADDR=10.3.0.4 docker.io/openio/openstack-keystone Trying to pull docker.io/openio/openstack-keystone:latest... Getting image source signatures Copying blob 7c4d210b98c8 done Copying blob 2d473b07cdd5 done Copying blob 82a0ef184707 done Copying config 71e5835046 done Writing manifest to image destination Storing signatures 9d4468c9b6131b5851299878719ea7b3b3d96548032d957e26be5c81d734c788 ------------------------------ $ podman ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 9d4468c9b613 docker.io/openio/openstack-keystone:latest /keystone-v3.sh 10 seconds ago Up 10 seconds ago keystone
- add test users
$ export OS_IDENTITY_API_VERSION="3" $ export OS_AUTH_URL="http://whuvm1.northeurope.cloudapp.azure.com:5000/v3" $ export OS_USER_DOMAIN_ID="default" $ export OS_PROJECT_DOMAIN_ID="default" $ export OS_PROJECT_NAME="admin" $ export OS_USERNAME="admin" $ export OS_PASSWORD="ADMIN_PASS" $ openstack --os-auth-url http://whuvm1.northeurope.cloudapp.azure.com:5000/v3 --os-project-domain-name default --os-user-domain-name default --os-project-name admin --os-username admin token issue +------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+ | Field | Value | +------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+ | expires | 2022-10-20T07:37:17+0000 | | id | gAAAAABjUOydJx4RhnqTgDQ3e-6BfuzO_uTqBaMm3t4PbhcuKXYiwT8WiLJn4Yq6Btf9XeeMIGVM3nm6LxbJvyE7-PIG3bcXvKFkKHhz6aTTd991zmfHXTdC6awTIY1PvbU8wcHA1tFK475YkumGTVxT3Z3thZ3eCSSi3bQD6rsxCa4mqlwgRfs | | project_id | 9d7826c33c7c4c7c9360d9e5ccc97c62 | | user_id | 047b493ab7754cfab0c9c5d5294d5246 | +------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+------------------------------ $ openstack project create --domain default --description "whu keystone test project" whuproject +-------------+----------------------------------+ | Field | Value | +-------------+----------------------------------+ | description | whu keystone test project | | domain_id | default | | enabled | True | | id | dc8b496599ff455c816409d7589dcf05 | | is_domain | False | | name | whuproject | | options | {} | | parent_id | default | | tags | [] | +-------------+----------------------------------+ $ openstack role create whurole +-----------+----------------------------------+ | Field | Value | +-----------+----------------------------------+ | domain_id | None | | id | c6281c7410e048b1a9e7b3a0749810c1 | | name | whurole | | options | {} | +-----------+----------------------------------+ $ openstack user create --domain default --password ADMIN_PASS whuuser1 +---------------------+----------------------------------+ | Field | Value | +---------------------+----------------------------------+ | domain_id | default | | enabled | True | | id | 08d4a32b6f314dc2ba22194d9eee2cb3 | | name | whuuser1 | | options | {} | | password_expires_at | None | +---------------------+----------------------------------+ $ openstack role add --project whuproject --user whuuser1 whurole $ openstack --os-auth-url http://whuvm1.northeurope.cloudapp.azure.com:5000/v3 --os-project-domain-name default --os-user-domain-name default --os-project-name whuproject --os-username whuuser1 token issue +------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+ | Field | Value | +------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+ | expires | 2022-10-20T07:37:26+0000 | | id | gAAAAABjUOym-a8NsWoTaw2Q8gP1e4FM8zi9DG5XZ7g8lZYfiOfy_Znj-edlD5_ScH5tuxzAiQwP-arNXhBIqHtYslTntLdyXH-OX-feMrbZyPutgB2uA_veByVqrBPg6W1y0SncK7S-RZKynj35_MYsEjzsKjsINrAyXBCojp44PlN3moBCC4I | | project_id | dc8b496599ff455c816409d7589dcf05 | | user_id | 08d4a32b6f314dc2ba22194d9eee2cb3 | +------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+ $ openstack user list +----------------------------------+----------+ | ID | Name | +----------------------------------+----------+ | 047b493ab7754cfab0c9c5d5294d5246 | admin | | 6b73cbc255b14ec58652ab53da21cf14 | swift | | 5b6a42096f0040d3ae786b1a12618a0d | demo | | 08d4a32b6f314dc2ba22194d9eee2cb3 | whuuser1 | +----------------------------------+----------+
Got below logs from quay pod log
gunicorn-web stdout | 2022-10-20 07:05:19,159 [210] [DEBUG] [keystoneauth.identity.v3.base] Making authentication request to http://whuvm1.northeurope.cloudapp.azure.com:5000/v3/auth/tokens gunicorn-web stdout | 2022-10-20 07:05:19,159 [206] [DEBUG] [keystoneauth.identity.v3.base] Making authentication request to http://whuvm1.northeurope.cloudapp.azure.com:5000/v3/auth/tokens gunicorn-web stdout | 2022-10-20 07:05:19,693 [206] [DEBUG] [keystoneauth.identity.v3.base] {"token": {"issued_at": "2022-10-20T07:05:19.000000Z", "audit_ids": ["Rsp20vW8QF28QEYsiZZ5kg"], "methods": ["password"], "expires_at": "2022-10-20T08:05:19.000000Z", "user": {"password_expires_at": null, "domain": {"id": "default", "name": "Default"}, "id": "047b493ab7754cfab0c9c5d5294d5246", "name": "admin"}}} gunicorn-web stdout | 2022-10-20 07:05:20,079 [210] [DEBUG] [keystoneauth.identity.v3.base] {"token": {"issued_at": "2022-10-20T07:05:20.000000Z", "audit_ids": ["GkX2RbV7TAuxcPUh0xSoaw"], "methods": ["password"], "expires_at": "2022-10-20T08:05:20.000000Z", "user": {"password_expires_at": null, "domain": {"id": "default", "name": "Default"}, "id": "047b493ab7754cfab0c9c5d5294d5246", "name": "admin"}}} gunicorn-web stdout | 2022-10-20 07:05:31,678 [206] [DEBUG] [keystoneauth.identity.v3.base] Making authentication request to http://whuvm1.northeurope.cloudapp.azure.com:5000/v3/auth/tokens gunicorn-web stdout | 2022-10-20 07:05:32,208 [206] [DEBUG] [keystoneauth.identity.v3.base] {"token": {"issued_at": "2022-10-20T07:05:32.000000Z", "audit_ids": ["7Mic-3AnS5GABnnyiSyYjQ"], "methods": ["password"], "expires_at": "2022-10-20T08:05:32.000000Z", "user": {"password_expires_at": null, "domain": {"id": "default", "name": "Default"}, "id": "08d4a32b6f314dc2ba22194d9eee2cb3", "name": "whuuser1"}}} gunicorn-web stdout | 2022-10-20 07:05:32,209 [206] [DEBUG] [keystoneauth.identity.v3.base] Making authentication request to http://whuvm1.northeurope.cloudapp.azure.com:5000/v3/auth/tokens
Attach the whole log in Attachment.
After researching OpenStack API Documentation, got this information
Tokens have IDs, which the Identity API returns in the X-Subject-Token response header.
As example
$ curl --location --request POST 'http://18.117.110.13:5000/v3/auth/tokens' \ --header 'Content-Type: application/json' \ --header 'Authorization: Basic cXVheTpwYXNzd29yZA==' \ --data-raw '{ "auth": { "identity": { "methods": [ "password" ], "password": { "user": { "name": "demo", "password": "DEMO_PASS", "domain": { "name":"Default" } } } } } }' -v Note: Unnecessary use of -X or --request, POST is already inferred. * Uses proxy env variable NO_PROXY == 'nexus.apps.quaytest-12437.qe.devcluster.openshift.com' * Trying 18.117.110.13:5000... * Connected to 18.117.110.13 (18.117.110.13) port 5000 (#0) > POST /v3/auth/tokens HTTP/1.1 > Host: 18.117.110.13:5000 > User-Agent: curl/7.79.1 > Accept: */* > Content-Type: application/json > Authorization: Basic cXVheTpwYXNzd29yZA== > Content-Length: 398 > * Mark bundle as not supporting multiuse * HTTP 1.0, assume close after body < HTTP/1.0 201 Created < Date: Thu, 20 Oct 2022 09:59:05 GMT < Server: WSGIServer/0.1 Python/2.7.5 < X-Subject-Token: gAAAAABjURvpga7UyoC_yG7Zks5pIMa3LDNqpecus-dP7SYmP-01ztnPJCW7cohq5yO27x6VdPaqH1BAXLk2g7iLTx2Zz40sDVMvp5iffs7xO8sL5Kz1b_QwnsGzXWXMGfPJURoxiqfGNyLjtHhuDFxCQY-LBEVEtxFd7Fq5wpjNaUUMo3FcRTA < Vary: X-Auth-Token < Content-Type: application/json < Content-Length: 1865 < x-openstack-request-id: req-0c317adb-eaa6-4bb7-b0e1-d80cd0fd1ed6 < * Closing connection 0 {"token": {"is_domain": false, "methods": ["password"], "roles": [{"id": "8e08037289f54394a07a0ac54f6c02f5", "name": "admin"}, {"id": "c78ba9cee3c44c47865b1d45c5ebc388", "name": "reader"}, {"id": "83638953dd134b539adb81a99e22a413", "name": "member"}], "expires_at": "2022-10-20T10:59:05.000000Z", "project": {"domain": {"id": "default", "name": "Default"}, "id": "522e5b077c6b47cda6221bc89169c096", "name": "demo"}, "catalog": [{"endpoints": [{"region_id": "RegionOne", "url": "http://18.117.110.13:35357", "region": "RegionOne", "interface": "admin", "id": "441a6a94b7ed419bbc643a6acb5bf39f"}, {"region_id": "RegionOne", "url": "http://18.117.110.13:5000", "region": "RegionOne", "interface": "internal", "id": "4e0eb3d6c8ec4db4858bc6e572bfe775"}, {"region_id": "RegionOne", "url": "http://18.117.110.13:5000", "region": "RegionOne", "interface": "public", "id": "9266baf64c4e4b1684643c7a1ac5ddf5"}], "type": "identity", "id": "1f3e786ed46445a4b76f0bb198209d62", "name": "keystone"}, {"endpoints": [{"region_id": "RegionOne", "url": "http://18.117.110.13:6007/v1/AUTH_522e5b077c6b47cda6221bc89169c096", "region": "RegionOne", "interface": "public", "id": "0c1be4d2e58a48e4a9d11b53b7b22118"}, {"region_id": "RegionOne", "url": "http://18.117.110.13:6007/v1/AUTH_522e5b077c6b47cda6221bc89169c096", "region": "RegionOne", "interface": "internal", "id": "76ce783ff82a4eeaa5a7f540d26daf60"}, {"region_id": "RegionOne", "url": "http://18.117.110.13:6007/v1", "region": "RegionOne", "interface": "admin", "id": "9be2c92e6cb5480cb485716ac82da352"}], "type": "object-store", "id": "35a731ffa6f041bfb3e31b54882f2eea", "name": "openio-swift"}], "user": {"password_expires_at": null, "domain": {"id": "default", "name": "Default"}, "id": "794018e418dd44baa541d963e3e255b9", "name": "demo"}, "audit_ids": ["OqYS0616SfiMeHpZ6cwPWA"], "issued_at": "2022-10-20T09:59:05.000000Z"}}%
If quay just parses the response payload, quay can't get the token.
I guess that is why quay keeps trying to request token in log.