-
Bug
-
Resolution: Done
-
Critical
-
None
-
False
-
False
-
Quay Enterprise
-
The client is using the follwing part of the Dockerfile to build their images:
FROM php:8.0.10-apache-bullseye # Requirements for PHP Extensions # ext-zip requires libzip-dev libzip4 zlib1g-dev RUN apt-get update \ && apt-get install -y libzip-dev libzip4 unzip zip zlib1g-dev \ && apt autoremove -y \ && apt-get clean \ && rm -rf /var/lib/apt/lists/* # Enable aditional PHP Extensions RUN docker-php-ext-install zip
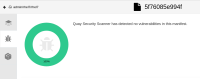
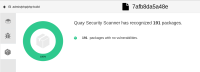
The base image is 2 months old. When this image is pushed to Quay 3.6 backed with Clair v4, the image is passed. Green. On the other hand, Quay.io backed with Clair v2 shows 203 vulnerabilities in the same image, of which 1 is marked critical with a severity 9.8:
https://security-tracker.debian.org/tracker/CVE-2019-19814 - linux-libc-dev package, marked as linux in Quay.io
This is a CVE detected in the Apache webserver also used in the image:
https://security-tracker.debian.org/tracker/CVE-2021-39275
The client also used a very old RHEL 7 based image from our own registry for another test:
The image is graded as F on registry.redhat.io. Again, Quay 3.6 backed by Clair v4 does not show any vulnerabilities. Screenshots of Quay.io results and Quay 3.6 results for the specific images are attached.
Plesae check.
- is duplicated by
-
PROJQUAY-3073 Investigate Debian Bullseye apache image
-
- Closed
-
-
PROJQUAY-3074 Investigate ancient RHEL7 image
-
- Closed
-
- is related to
-
PROJQUAY-2804 Debian data improvement
-
- Closed
-
- relates to
-
PROJQUAY-2649 Clair v4 debian matching source/binary packages
-
- Closed
-