-
Bug
-
Resolution: Obsolete
-
Major
-
None
-
quay-v3.5.0
-
False
-
False
-
Undefined
-
Description:
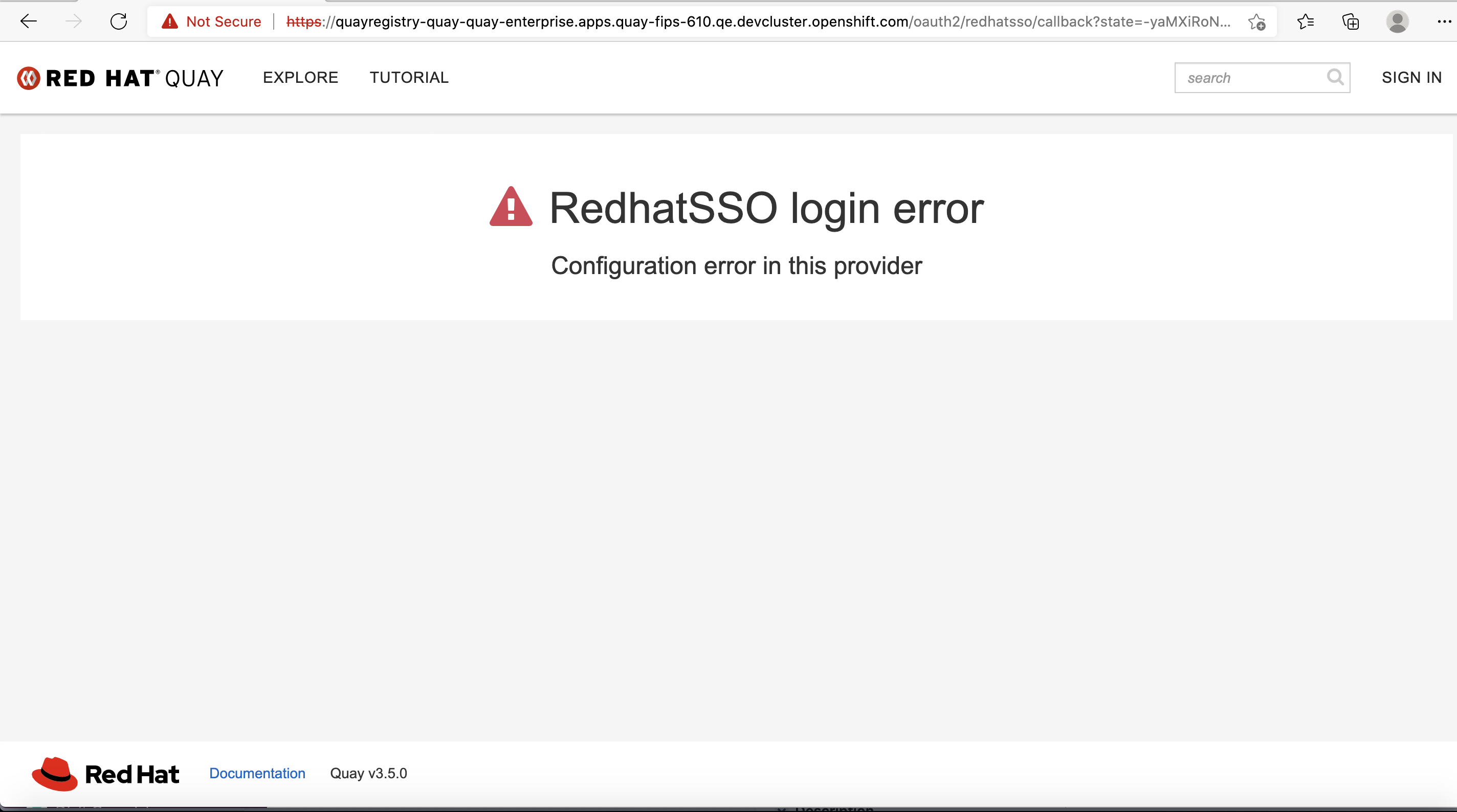
This is an issue found when enabled LDAP and OIDC Provider with Quay config editor, after select "Binding Field" of OIDC Provider as 'None', login quay with OIDC SSO user, get error "RedhatSSO login error,Configuration error in this provider", checked Quay App Pod Logs, get following error:
The expected behavior is if allow quay customer to choose None, then as the comments described "If none selected, a user unique to *Quay will be created on initial login with this OIDC provider. This is not the recommended setup.*"
If the behavior is not allow to choose None in this situation, then quay config editor should not provide option 'None'
gunicorn-web stdout | 2021-03-29 09:30:55,180 [249] [DEBUG] [endpoints.oauth.login] Got oauth bind field name of ""
gunicorn-web stdout | 2021-03-29 09:30:55,180 [249] [ERROR] [endpoints.oauth.login] Missing lookup value for OAuth login
Quay Version:
oc get pod NAME READY STATUS RESTARTS AGE quay-operator.v3.5.0-7489b8c4f-r4r6j 1/1 Running 0 8h quayregistry-clair-app-588d4884c8-q9zw6 1/1 Running 0 21m quayregistry-clair-postgres-6d5bd88bd8-4pz9b 1/1 Running 0 6h28m quayregistry-quay-app-6dfc49d585-hnjc6 1/1 Running 0 21m quayregistry-quay-config-editor-76c96fc997-6649w 1/1 Running 0 21m quayregistry-quay-database-f69444dd4-k2lhr 1/1 Running 0 6h47m quayregistry-quay-mirror-69b75797c5-nm2vm 1/1 Running 0 20m quayregistry-quay-postgres-init-dkhqf 0/1 Completed 0 6h47m quayregistry-quay-redis-5f96d7dc4-k4f9x 1/1 Running 0 6h28m oc get pod quayregistry-quay-app-6dfc49d585-hnjc6 -o json | jq '.spec.containers[0].image' "registry.redhat.io/quay/quay-rhel8@sha256:0444c7b452a14e0c87ee56f9aa72c54484333c38b0a95de9a4f11f6177273f26"
Steps:
- Deploy Quay 3.5.0 Operator to all OCP namespace
- Deploy quay with quay 3.5 Operator with using AWS S3 as backend registry storage
- Open Quay config editor, and choose LDAP as internal authentication, input valid LDAP configurations
- Click add new OIDC Provider
- Upload the SSL Cert of OIDC provider
- Input correct configurations of OIDC provider
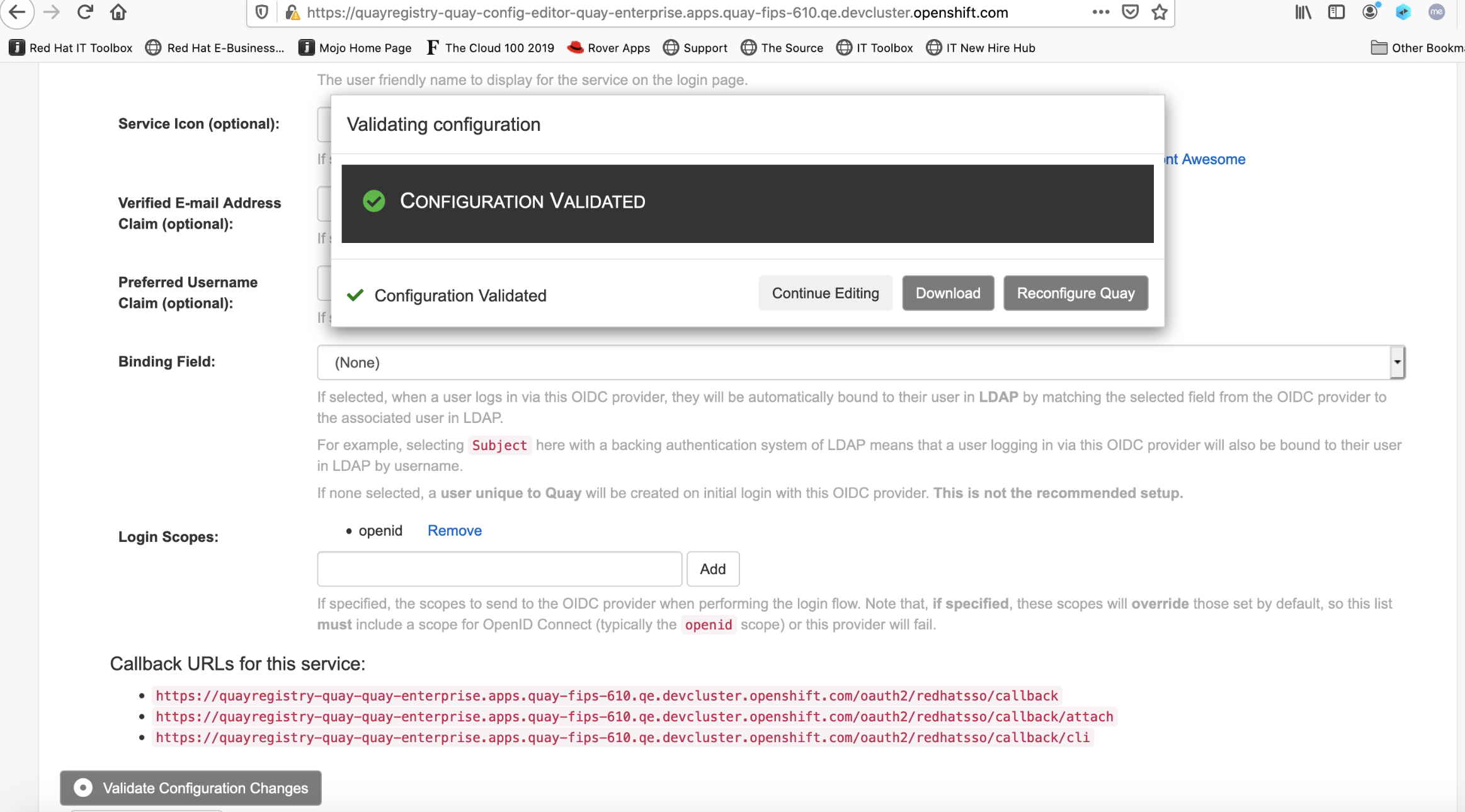
- In the OIDC Provider "Binding Field:", Choose 'None'
- Click Validate configurations
- After validations is passed, Click reconfigure quay
- Login quay with OIDC SSO user
Expected Results:
Login quay complete successfully
Actual Results:
Login quay was failed with error message 'Configuration error in this provider'