-
Bug
-
Resolution: Done
-
Major
-
quay-v3.4.0
Description:
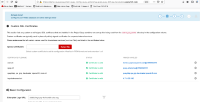
This is an issue found when set OIDC with Quay Config app, now for the tartget OIDC Server(KeyCloak) server it was using self singed cert, it will not be trusted by client side; On Quay config app upload the TLS cert of the OIDC server, the results is that it was failed to save configurations, get the following error message:
OIDC Login(s)
TTPSConnectionPool(host='quayldap.qe.gcp.devcluster.openshift.com', port=8443): Max retries exceeded with url: /auth/realms/quay/.well-known/openid-configuration (Caused by SSLError(SSLError("bad handshake: Error([('SSL routines', 'tls_process_server_certificate', 'certificate verify failed')],)",),))
Refer to the screenshots of the Quay config-app.
Before start, configure the following callback URLs on OIDC server's target Client.
Callback URLs for this service:
- https://demo-quayecosystem-quay-quay-enterprise.apps.quay-325.qe.devcluster.openshift.com/oauth2/redhat/callback
- https://demo-quayecosystem-quay-quay-enterprise.apps.quay-325.qe.devcluster.openshift.com/oauth2/redhat/callback/attach
- https://demo-quayecosystem-quay-quay-enterprise.apps.quay-325.qe.devcluster.openshift.com/oauth2/redhat/callback/cli
Steps:
1. Open Quay config app
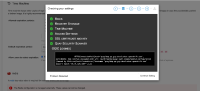
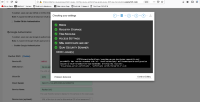
2. Go to "External Authorization (OAuth) " section, add new OIDC server
3. In the "OIDC: ", give "https://quayldap.qe.gcp.devcluster.openshift.com:8443/auth/realms/quay/"
4. and input valid client ID and secret
5. At the section "Custom TLS Certificate", upload the self signed cert of target OIDC server
6. Click "Save Configurations"
Expected Results:
Quay config app can save the configurations successfully.
Acutal Results:
Quay config app can't save configurations.