-
Spike
-
Resolution: Done
-
Critical
-
None
-
None
-
False
-
-
False
-
-
Summary:
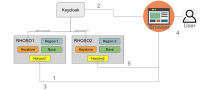
- We need to determine our level of support for a multi-region deployment of several clusters sharing the same federated IdP. The question to answer is whether or not a user is required to re-authenticate when moving from cloud A to cloud B while possessing a valid token from Keycloak (OIDC provider). This must be done with the Horizon dashboard and the re-entry of the username when traversing sites is acceptable.
Goal:
- We want to know if it's possible with two RHOSO 18 deployments (cloud A, cloud B) both configured with a single, shared, OIDC backend (keycloak) to have a user authenticate into cloud A and then seamlessly move to cloud B without re-authentication.
- User goes to dashboard URL for cloud A
- User is redirected to keycloak URL and authenticates and is then redirected back to cloud A dashboard URL
- User performs some actions on cloud A
- User uses the drop down in Horizon to select cloud B
- User is redirected to dashboard URL of cloud B
- Does the user need to re-authenticate here? The working theory is "No" because the browser has a cached, valid token from keycloak.
- Will keystone on cloud B use this token?
- Will the user need to enter their email again?
- Will the user just need to click the login button again?
TimeBox:
- 1 week
Deliverables/Outcomes:
- Answers to the questions outlined in the goal
- If this does not work as expected an analysis of what work would be needed in Keystone, Horizon, etc... to enable this functionality