-
Bug
-
Resolution: Unresolved
-
Normal
-
None
-
None
-
None
Superset on OCP 4.6.17 and ODH 1.1.0 on a cluster where the firewall only allows HTTPS ingress traffic and specifically drops HTTP ingress traffic so it does not reach the cluster.
Superset creates an HTTP route by default - a manually created HTTPS route with edge termination can be used instead, with the hostname https://superset.example.com/
The problem is that requests to HTTP endpoints are firewalled in this cluster - ie. don't reach the cluster.
The initial experience is that the application does not work.
Some of the redirects in Superset redirect you to the http endpoint which would then, usually, be redirected by the `insecureEdgeTerminationPolicy: redirect` on the route back to https.
Here, however, because that traffic is dropped this results in a timeout.
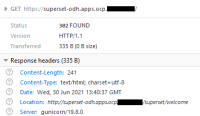
Specifically the following endpoint redirections have been observed from the application (See attachment):
https://superset.example.com/ -> http://superset.example.com/superset/welcome/
https://superset.example.com/superset/welcome/ -> http://superset.example.com/login/
https://superset.example.com/login/ -> http://superset.example.com/
https://superset.example.com/logout/ -> http://superset.example.com/
A user can manually navigate to /login to login, and after a cookie is received, they can manually navigate to /superset/welcome and from there on, the application seems to work over HTTPS.