-
Bug
-
Resolution: Done
-
Critical
-
openshift-4.6
-
False
-
False
-
Undefined
-
Not Supported
-
ODC Sprint 195
-
Moderate
Description of problem:
Assumpitons:
1. pipelines operator should be installed
2. Create a new namespace/project
Via +Add-flow when user selects pipelines, while starting pipeline from UI, try changing image location to private image registry eg: `quay.io/<usrname>/<image-name>`
Select Advanced options -> Add secrets -> (provide necessary details ) by selecting authentication type as image credentials once you add secrets by default it gets attached to service account pipeline.
Seems when user tries to add secrets to service account, it's getting attached to sa to `pull` by default
eg: here is oc command how add our secrets to service account explicitly at run time
oc secrets link serviceaccount/<sa> secrets/<pull_secret_name> --for=pull,mount
Note: with existing build user can pull image from private registry but won't be able to push to it.
Actual results:
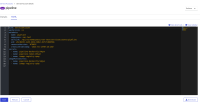
secrets: - name: pipeline-token-88mw6 - name: pipeline-dockercfg-pv68m - name: quay-sec imagePullSecrets: - name: pipeline-dockercfg-pv68m
Expected results:
secrets: - name: pipeline-token-88mw6 - name: pipeline-dockercfg-pv68m - name: quay-sec imagePullSecrets: - name: pipeline-dockercfg-pv68m - name: quay-sec