-
Feature
-
Resolution: Done
-
Normal
-
None
-
Product / Portfolio Work
-
-
0% To Do, 0% In Progress, 100% Done
-
False
-
None
-
False
-
None
-
None
-
None
-
None
-
None
-
None
-
None
-
None
-
None
-
None
-
Undefined
Feature Overview
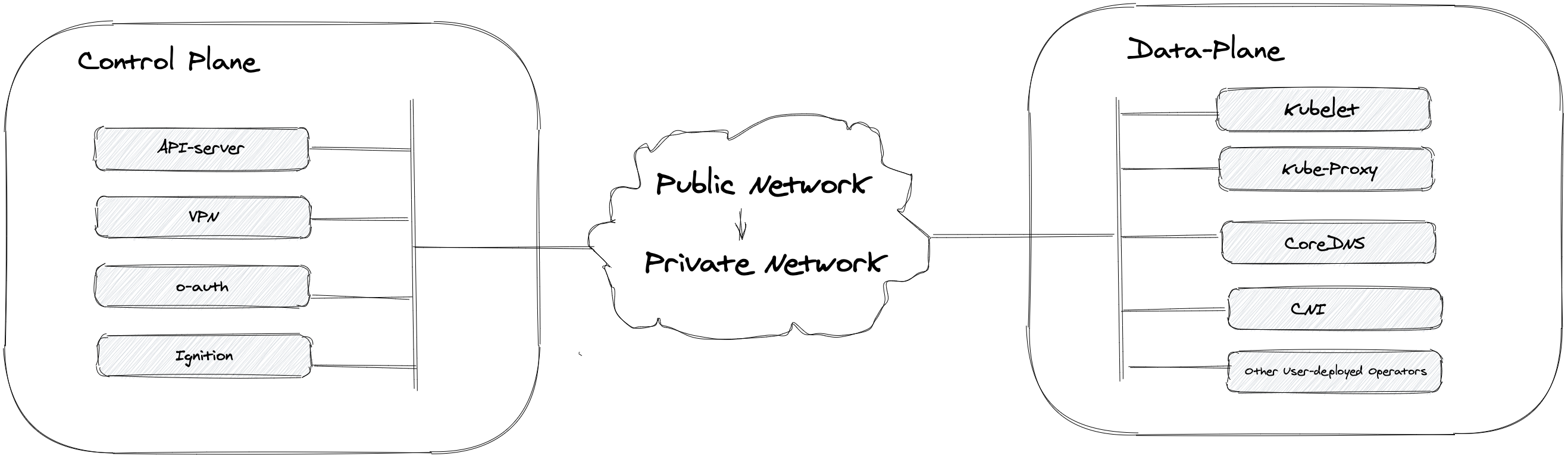
Private cluster adds an extra level of isolation usually achieved through tighter network policies. This might be needed for security/privacy reasons.
Private clusters affect different components in HyperShift's architecture. For example, how the control-plane communicates with the data-plane and vice-versa. In normal cases, it is assumed that control-plane endpoints (e.g., API-server, tunnel, OAuth, ...) are accessible via a public end-point, with private cluster deployments, this is no longer the case. Furthermore, depending on the infrastructure management models [1], the nodes might be configured to egress through public IPs or via a Gateway.
Goal(s)
- Determine whether private clusters are desirable for HyperShift, if so expose this as an option for HyperShift cluster (e.g., in the API).
- Consider the different options to achieve private networking:
- VPC peering - Relies on provider-specific features and might break the homogeneity
- Tunneling - Stateful reverse proxies that keep track of initiated connections.
Note: this feature might require sync with the OSD and SD teams as they already have a model to address private cluster deployments for standalone OpenShift.
- links to