-
Story
-
Resolution: Done
-
Undefined
-
None
-
None
-
None
-
None
-
Product / Portfolio Work
-
False
-
-
False
-
3
-
None
-
None
-
OCP Node Sprint 274 (green)
Environment: 4.20,openshift/api#2384,[openshift/cluster-update-keys#74|https://github.com/openshift/cluster-update-keys/pull/74],[openshift/machine-config-operator#5143|https://github.com/openshift/machine-config-operator/pull/5143]
Enable FeatureGate:
oc edit featuregate
Edit spec:
spec: featureSet: TechPreviewNoUpgrade
Test Execution - ClusterImagePolicy:
Following steps from: https://polarion.engineering.redhat.com/polarion/#/project/OSE/workitem?id=OCP-83485
Scenario1: PASSED
❯ oc get crd clusterimagepolicies.config.openshift.io -o json | jq -r '.status.storedVersions[]'
v1
❯ oc get crd clusterimagepolicies.config.openshift.io -o json | jq -r '.spec.versions[].name'
v1
❯ sh-5.1# cat etc/containers/policy.json
.... "quay.io/rh-ee-anahas/testsignedimage": [ { "type": "sigstoreSigned", "keyData": "LS0tLS1CRUd...S0t", "signedIdentity": { "type": "matchRepository" } }
❯ sh-5.1# cat etc/containers/registries.d/sigstore-registries.yaml
docker: quay.io/openshift-release-dev/ocp-release: use-sigstore-attachments: true quay.io/rh-ee-anahas/testsignedimage: use-sigstore-attachments: true
Scenario2: PASSED
sh-5.1# journalctl -u crio --since="2 minutes ago
- "IsRunningImageAllowed for image docker:quay.io/rh-ee-anahas/testsignedimage:latest" file="signature/policy_eval.go:274"
- " Using transport \"docker\" specific policy section \"quay.io/rh-ee-anahas/testsignedimage\"" file="signature/policy_eval.go:150
- "Pulled image: quay.io/rh-ee-anahas/testsignedimage@sha256:26133c5dc88782aa8f492..78" file="server/image_pull.go:12
Scenario3: expect to fail. PASSED W/COMMENTS*
UI errors:
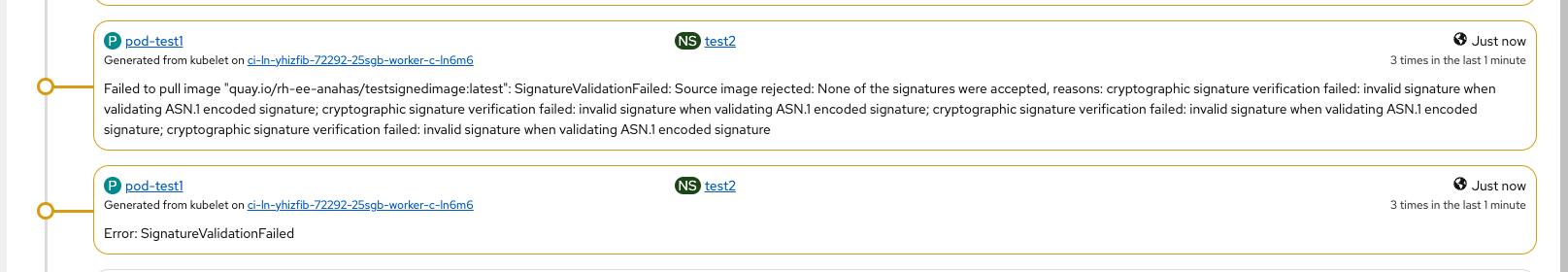
Log errors:
- "IsRunningImageAllowed for image docker:quay.io/rh-ee-anahas/testsignedimage:latest" file="signature/policy_eval.go:274"
- Running is allowed.
- " Using transport \"docker\" specific policy section \"quay.io/rh-ee-anahas/testsignedimage\"" file="signature/policy_eval.go:150"
- We're using the policy.
- "Error pulling image quay.io/rh-ee-anahas/testsignedimage:latest: Source image rejected: None of the signatures were accepted, reasons: cryptographic signature verification failed: invalid>
- "Response error: SignatureValidationFailed: Source image rejected: None of the signatures were accepted, reasons: cryptographic signature verification failed: invalid signature when validati>
- Signature was not accepted.
Scenario4: PASSED
UI and log check:
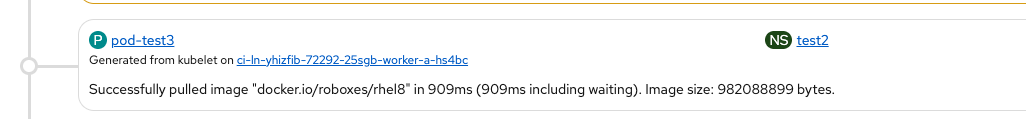
Log check:
"IsRunningImageAllowed for image docker:docker.io/roboxes/rhel8:latest" file="signature/policy_eval.go:274"
" Using default policy section" file="signature/policy_eval.go:162"
- Using default policy (not the one we created, as expected)
"Pulled image: docker.io/roboxes/rhel8@sha256:0d17edce2499498eb8a8df68ce4a454319e9...91ef" file="server/image_pull.go:122"
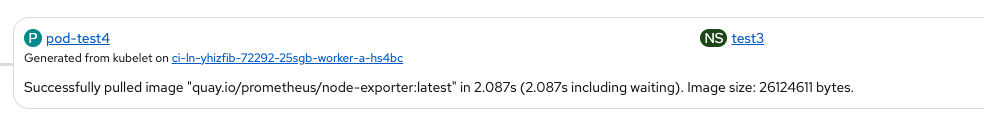
Log check:
"IsRunningImageAllowed for image docker:quay.io/prometheus/node-exporter:latest" file="signature/policy_eval.go:274"
" Using default policy section" file="signature/policy_eval.go:162"
- Using default policy (not the one we created, as expected)
"Pulled image: quay.io/prometheus/node-exporter@sha256:863b62ff9f392b6f472e....e" file="server/image_pull.go:122"
Scenario5: PASSED W/COMMENTS
Before deleting cluster policy....
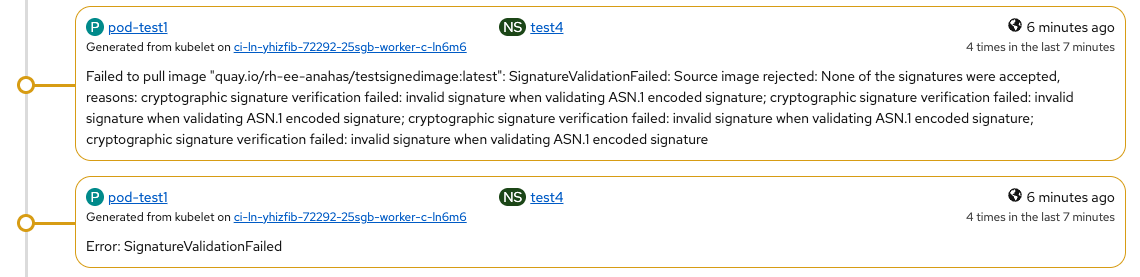
After deleting cluster policy...
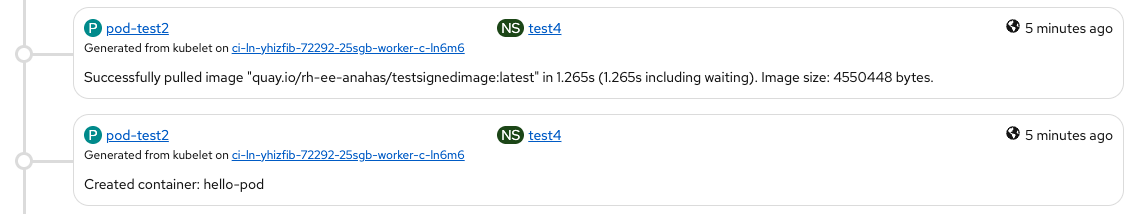
Test Execution - ImagePolicy:
Scenario1: PASSED
❯ oc get crd imagepolicies.config.openshift.io -o json | jq -r '.spec.versions[].name'
v1
❯ oc get crd imagepolicies.config.openshift.io -o json | jq -r '.status.storedVersions[]'
v1
❯ sh-5.1# cat etc/containers/registries.d/sigstore-registries.yaml
docker: quay.io/openshift-release-dev/ocp-release: use-sigstore-attachments: true quay.io/rh-ee-anahas/imagedigest@sha256:91a7f683619ea3c57e9b10b7dcd7143d4381d0a41a3e21bcc5be5ae4ef3c0419: use-sigstore-attachments: true
❯ sh-5.1# cat etc/crio/policies/test1.json
"quay.io/rh-ee-anahas/imagedigest@sha256:91a7f683619ea3c57e9...0419": [ { "type": "sigstoreSigned", "keyData": "LS0tLS1CRUdJTiBQVUJMSUMgS0VZLS0tLS0KTUZrd0V3WU..S0t", "signedIdentity": { "type": "matchRepoDigestOrExact" }
Scenario2: PASSED
- "IsRunningImageAllowed for image docker:quay.io/rh-ee-anahas/imagedigest@sha256:531eaae43197a403f9ae14b900480ba8d7a4b4893153072beee79e8572fa1af0" file="signature/policy_eval.go:274"
- " Using transport \"docker\" policy section \"quay.io/rh-ee-anahas/imagedigest@sha256:531eaae43197a403f9ae14b900480ba8d7a4b4893153072beee79e8572fa1af0\"" file="signature/policy_eval.go:143"
- "Pulled image: quay.io/rh-ee-anahas/imagedigest@sha256:531eaae43197a403f9ae14b900480ba8d7a4b4893153072beee79e8572fa1af0" file="server/image_pull.go:122" id=72a1366b-6a2c-4ac5-b4d5-83b48
Scenario3: PASSED W/COMMENTS
sh-5.1# cat etc/containers/registries.d/sigstore-registries.yaml
docker: quay.io/openshift-release-dev/ocp-release: use-sigstore-attachments: true quay.io/rh-ee-anahas/imagedigest@sha256:531eaae43197a403f9ae14b900480ba8d7a4b4893153072beee79e8572fa1af0: use-sigstore-attachments: true
sh-5.1# cat etc/crio/policies/test2.json
"quay.io/rh-ee-anahas/imagedigest@sha256:531eaae43197a403f9ae14b900480ba8d7a4b4893153072beee79e8572fa1af0": [ { "type": "sigstoreSigned", "keyData": "LS0tLS1CRUdJTiBQVUJMSUMgS0VZLS0tLS0KTUZrd0V3WUhLb1pJemowQ0FRWUlLb1pJemowREFRY0RRZ0FFVFJPZU9jUWk2RHJJa1J0NVdYdzRYMnd4VExFSQpIL3RwejgwMmE5REhuYStzTThVdGFkdUlSbHZSVDI3a3Fudkc3TDJJNTU5UGN1L1VvTzcwUVQzR1V3PT0KLS0tLS1FTkQgUFVCTElDIEtFWS0tLS0t", "signedIdentity": { "type": "matchRepoDigestOrExact" }
After trying to pull the image from quay.io (with a wrong keyData, generated from another cosign.pub):
Logs:
- "IsRunningImageAllowed for image docker:quay.io/rh-ee-anahas/imagedigest@sha256:531eaae431...a1af0" file="signature/policy_eval.go:274"
" Using transport \"docker\" policy section \"quay.io/rh-ee-anahas/imagedigest@sha256:531eaae431...a1af0\"" file="signature/policy_eval.go:143" - "Response error: checking signature of \"quay.io/rh-ee-anahas/imagedigest@sha256:531eaae431...a1af0\": verifying signatures: SignatureValidationFailed: None of the signatures were accepted,
- "Response error: checking signature of \"quay.io/rh-ee-anahas/imagedigest@sha256:531eaae431...a1af0\": verifying signatures: SignatureValidationFailed: None of the signatures were accepted....
UI:
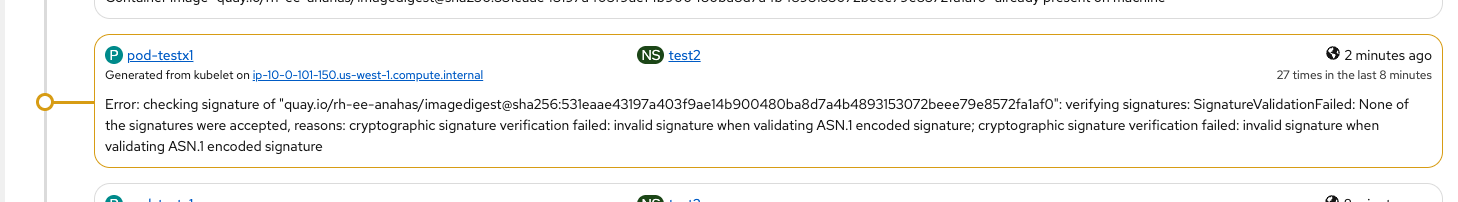
After trying to pull an image from quay.io (keyData was tampered so, it's not valid)
Logs:
- "IsRunningImageAllowed for image docker:quay.io/rh-ee-anahas/imagedigest@sha256:531eaae43197a403f9ae14b900480ba8d7a4b4893153072beee79e8572fa1af0" file="signature/policy_eval.go:274"
- " Using transport \"docker\" policy section \"quay.io/rh-ee-anahas/imagedigest@sha256:531eaae43197a403f9ae14b900480ba8d7a4b4893153072beee79e8572fa1af0\"" file="signature/policy_eval.go:143"
- "Error pulling image quay.io/rh-ee-anahas/imagedigest@sha256:531eaae43197a403f9ae14b900480ba8d7a4b4893153072beee79e8572fa1af0: Source image rejected: None of the signatures were accepted, reasons: parsing public key 1: asn1: structure error: ta>
- "Response error: SignatureValidationFailed: Source image rejected: None of the signatures were accepted, reasons: parsing public key 1: asn1: structure error: tags don't match (3 vs {class:0 tag:19 length:66 isCompound:false}) {opti
UI:
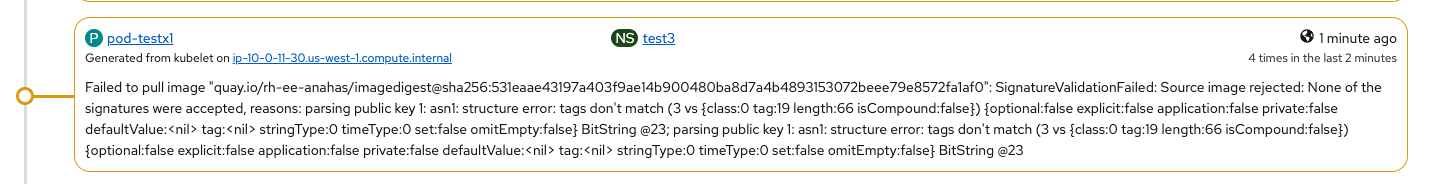
Scenario4: PASSED
Logs:
- "IsRunningImageAllowed for image docker:docker.io/roboxes/rhel8:latest" file="signature/policy_eval.go:274"
- " Using default policy section" file="signature/policy_eval.go:162"
- "Pulled image: docker.io/roboxes/rhel8@sha256:0d17edce24994...391ef" file="server/image_pull.go:122" id=e6a46e6e-3be4-4ca1-9873-aa1df7323d0d name=/runtime.v1.ImageService/PullImage
UI:
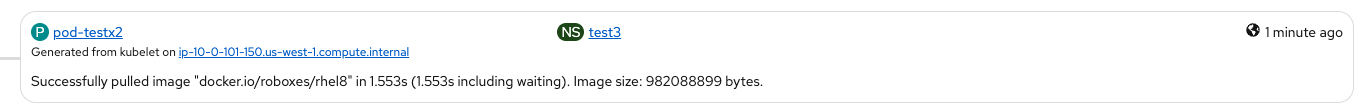
Scenario5:
Log:
- " Using transport \"docker\" specific policy section \"quay.io/openshift-release-dev/ocp-release\"" file="signature/policy_eval.go:150"
- "Response error: SignatureValidationFailed: Source image rejected: None of the signatures were accepted, reasons: Signature for identity \"quay.io/openshift-release-dev/ocp-release@sha256:d8988b7ff4ba0281fee6c6c1dbbdfa922b6cb862d9
UI:
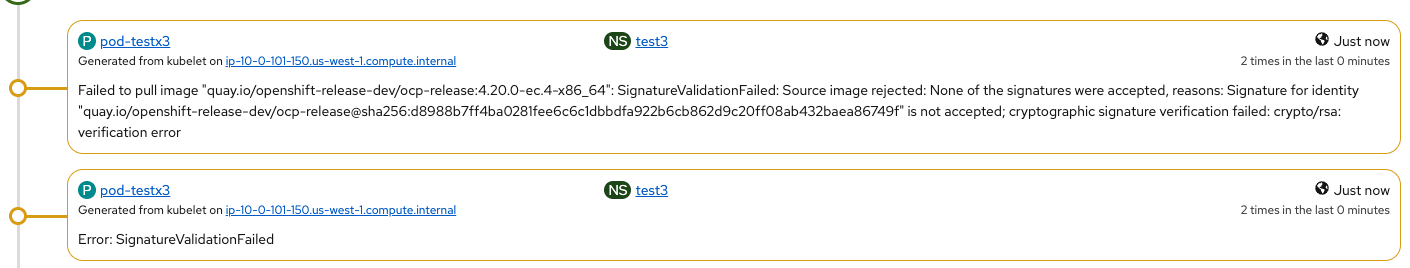
Scenario6: PASSED
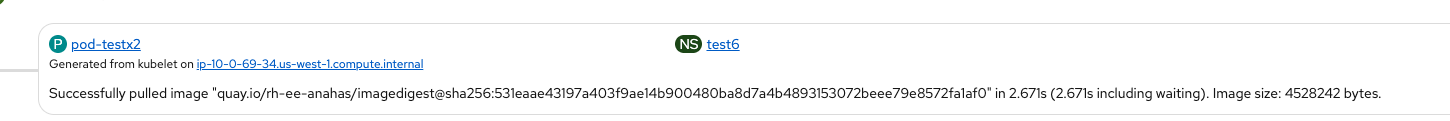
- is cloned by
-
OCPNODE-3503 pre-merge testing: Move ClusterImagePolicy, ImagePolicy to v1 - DevPreviewNoUpgrade
-
- Closed
-
- links to