-
Story
-
Resolution: Done
-
Normal
-
None
-
None
-
None
-
None
-
Product / Portfolio Work
-
False
-
-
False
-
3
-
None
-
None
-
OCP Node Sprint 273 (Green), OCP Node Sprint 274 (green)
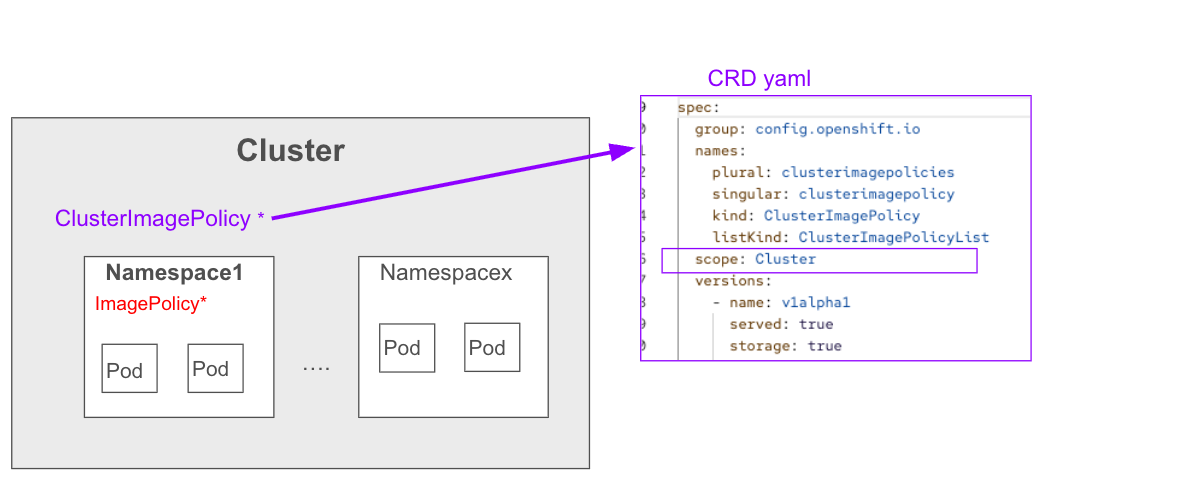
ClusterImagePolicy CRD
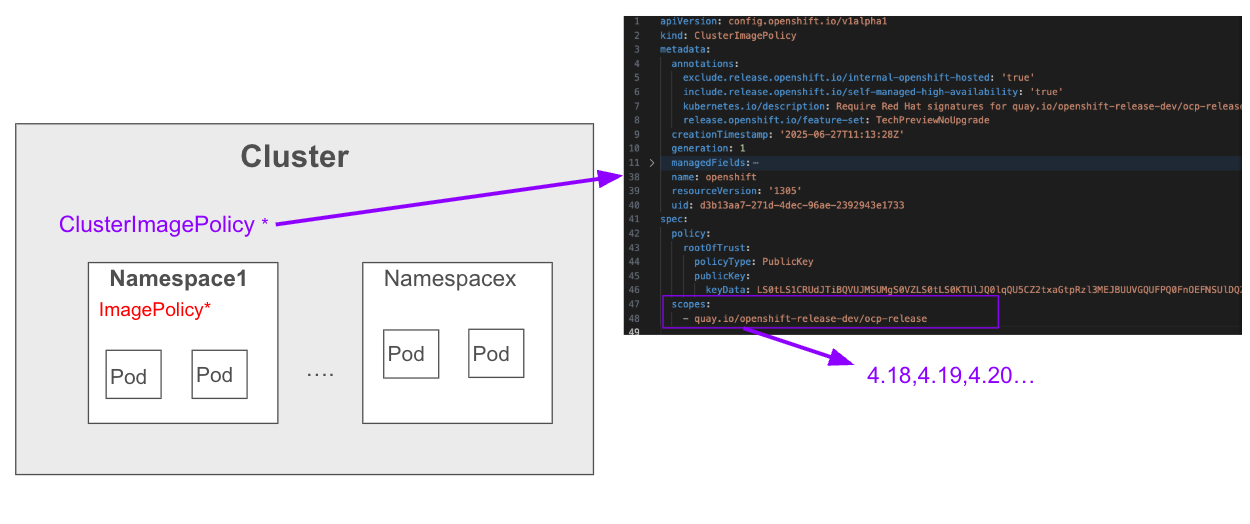
ClusterImagePolicy CR
Scenarios summary:
- Check API version (no techpreview image)
- Signatures match
- matchPolicy: MatchRepository
- Signatures do not match
- Pull an image from any repo not defined in the policy
- Delete policy
Pre-requirement: how to create images and sign them using Cosign.
- Install Cosign
- Ex: brew install cosign
- Follow the steps below to create an image on quay.io and sign it. At the end you should have a signed Cosign image on the repo:
- Build and push an image for signing
-
- podman login quay.io
- Create a Dockerfile
- echo "FROM scratch" >Dockerfile
- or, if you want to use an Image, below another example:
- FROM busybox:latest
CMD ["sh", "-c", "echo 'Hello from https://quay.io/repository/rh-ee-anahas/testsignedimage' && sleep infinity"]
- Build the image and push to quay io
- podman build --platform linux/amd64 -t quay.io/rh-ee-anahas/testsignedimage . (We should be in the same folder as Docker file)
- podman push quay.io/rh-ee-anahas/testsignedimage:latest
- Generate Cosign key pair
- $ cosign generate-key-pair
Enter password for private key:
Enter password for private key again:
Private key written to cosign.key
Public key written to cosign.pub
- $ cosign generate-key-pair
- Cosign sign the image using private key and push signature and image to the registr, need registry username and password
- cosign sign --key cosign.key --registry-username=yourUser --registry-password=yourPassword quay.io/rh-ee-anahas/testsignedimage:latest
-
- Build and push an image for signing
- Note that the "keyData" of the CRs should be enconded in base 64. To do that, do the following:
- Go to the local folder where cosign.key and cosign.pub are saved
- Open cosign.pub and copy everything (including the begin and the end of the public key)
- Go to any base 64 encode site, such as: https://www.base64encode.org/
- Paste the whole key > Encode
- Store this key, in the next tests it's going be called as "LS0tLS1CRUdJTiBQVUJMSU..............................JtLS0t"
Optional Cosign: to check if the .pub key matches with the signature in the repo, do the following :
cosign verify --key cosign.pub quay.io/rh-ee-anahas/testsignedimage:latest
Do not forget to change the repo address for the one it's being used.
If the signature matches, a message like this will be shown:
The following checks were performed on each of these signatures:
- The cosign claims were validated
- Existence of the claims in the transparency log was verified offline
- The signatures were verified against the specified public key[{"critical":{"identity".........
If the signature does not match, a message like this will be shown:
Error: no matching signatures: invalid signature when validating ASN.1 encoded signature error during command execution: no matching signatures: invalid signature when validating ASN.1 encoded signature
TESTING SCENARIOS (original): https://polarion.engineering.redhat.com/polarion/#/project/OSE/workitem?id=OCP-83517
Testing Scenarios (final version, please consider using the following links for testing purposes):
TestCase1: OCP-83533 - Check if API Version for ClusterImagePolicy is V1
TestCase2: OCP-83534 - ClusterImagePolicy CR pulls image successfully after Cosign validation
TestCase3: OCP-83537 - ClusterImagePolicy CR fails to pull image after Cosign validation
TestCase4: OCP-83538 - ClusterImagePolicy CR should allow to pull images not defined in the Scope