-
Story
-
Resolution: Obsolete
-
Undefined
-
None
-
None
-
None
-
True
-
-
False
-
Seems like the ticket is irrelevant. Needs clarification from PM on how to proceed with the effort of supporting SSO login.
-
-
-
OCMUI Core Sprint 262
Tyler Creller Tuesday at 8:25 AM
Abhishek requested that we point to service accounts for long-lived authentication needs in the deprecation message. Something to the effect of:
“Still need long-lived API access for automation? Check out service accounts” with a link to the ConsoleDot page.
Abhishek also requested that we mention {}use-device-code{-} in the new token page experience in addition to the -use-auth-code box. Something to the effect of:
“Don’t have access to a browser? Want to use ocm|rosa in a headless environment? try --use-device-code instead”
Acceptance Criteria
- Add the blue InfoAlert to Downloads -> OpenShift Cluster Manager API Token, under the 'Offline token deprecated' Warning alert.
- external doc link for 'service accounts' being tracked via https://issues.redhat.com/browse/OCM-4970
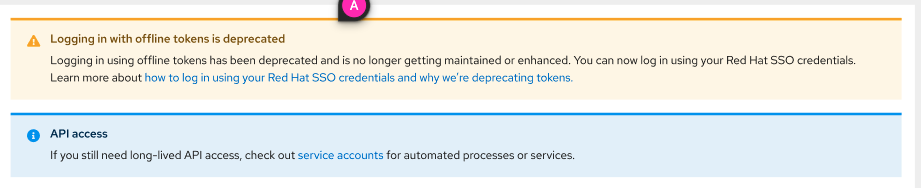
- external doc link for 'service accounts' being tracked via https://issues.redhat.com/browse/OCM-4970
- Update Step 2 of the 'SSO Login' instructions, add 2 Options. One for the existing browser option, and a new option for the 'headless|--use-device-code' instructions (See " How to display the 'SSO Login'" below).
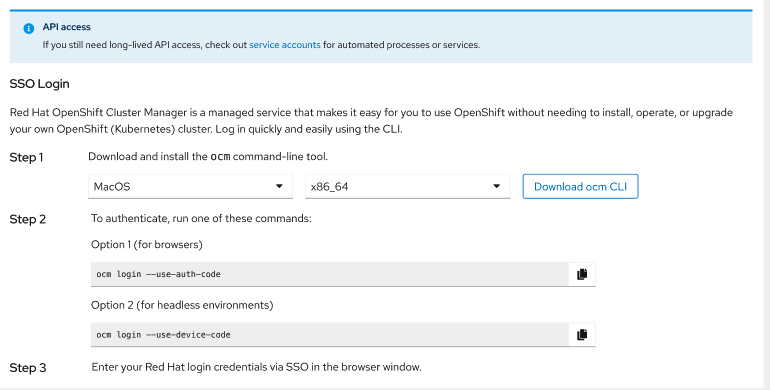
How to display the 'SSO Login'
To see SSO login you should add an org level capability to your org. But since you should probably don't want to affect all users in your org the way to test is by fake data/ changing the code locally:
- In src/components/CLILoginPage/CLILoginPage.tsx L79, add `restrictTokens = true;`
- Check /token and token/rosa pages, you should see the SSO login instructions (and ui shouldn't fetch the offline token).
- Remove the line you added. You should see the old offline tokens page.
- is related to
-
OCMUI-2995 Offlne tokens / SSO login: Align to new UX design
-
- Closed
-