-
Epic
-
Resolution: Unresolved
-
Undefined
-
None
-
None
-
None
-
netobserv-ip-categorization
-
To Do
-
None
-
25% To Do, 0% In Progress, 75% Done
-
False
-
-
False
-
Not Selected
-
None
-
None
-
None
It happens frequently that some captured source or destination IPs cannot be matched with any known kube object. These IPs can be internal to the cluster, or external.
To help users troubleshooting and understand what these IPs could be (or could not be), we can categorize them accordingly to the cluster network configuration. It will save time for the users trying to understand what they could be.
Here's an example of what we could show with this feature, identifying traffic here to Amazon S3: (this is from a PoC)
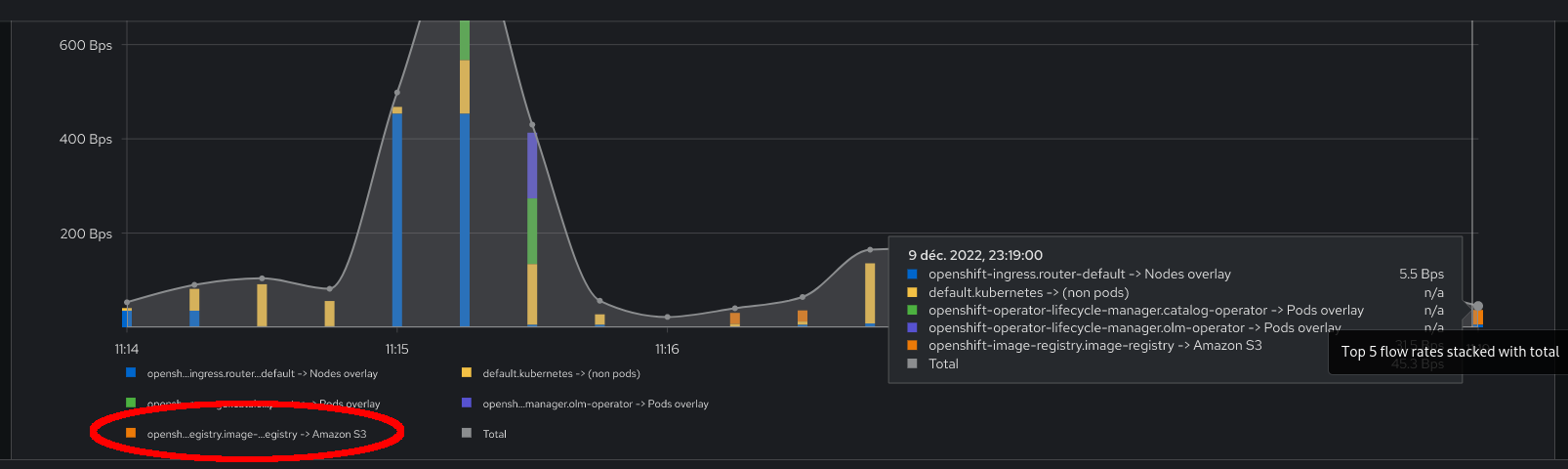
Also, in OpenShift, cluster networking is configured with "clusterNetwork", "machineNetwork" and "serviceNetwork" CIDR. IPs that we can't match with any kube object can then, as a fallback, be matched against these CIDRs, or other CIDRs configured by users. IPs not matching any of them should be assumed "external".
In the console plugin UI, this categorisation should be made visible (table, topology, ...)
- blocks
-
NETOBSERV-151 UI: Dashboard - Intranet/Internet traffic
-
- To Do
-

