-
Bug
-
Resolution: Done
-
Undefined
-
None
-
None
-
None
-
Quality / Stability / Reliability
-
False
-
None
-
None
-
None
-
None
-
None
-
NetObserv - Sprint 213, NetObserv - Sprint 214, NetObserv - Sprint 215
-
None
-
None
-
None
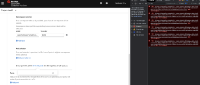
When user is logged as as developer/non-admin, they only have access to their own projects by default. When creating a network policy:
1. Add Ingress/Egress rule
2. Select "Allow traffic from pods inside the cluster"
3. When clicked on the "affected pods", the pop up shows empty and the console shows 403 (Forbidden), because user doesn't have privileges to see pods of projects that in rest of the cluster.
We should probably show some error or message on UI instead.