-
Bug
-
Resolution: Unresolved
-
Major
-
2.11.0
-
Quality / Stability / Reliability
-
False
-
-
True
-
-
Known Issue
-
Done
-
-
Description of problem:
Create a migration plan to migrate VM to OCP cluster with FC and plan setting: transfer network: openshift-mtv/br-eno8403 to target ns: mtv-test. The migration is hang, as the inspection pod in mtv-test namespace, it fails to add the transfer network: openshift-mtv/br-eno8403. We need to block the migration when the target namespace don't have permission to the transfer network.
Version-Release number of selected component (if applicable):
MTV 2.11.0-39 with CNV 4.20.5
How reproducible:
Always
Steps to Reproduce:
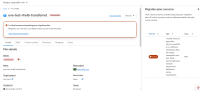
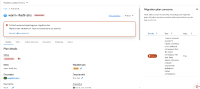
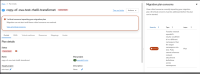
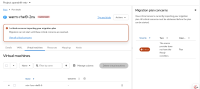
1) Create a migration plan: warm-rhel-transfer-2ns to migrate VM: mtv-func-rhel9-6 to OCP cluster with FC and plan transfer network: openshift-mtv/br-eno8403, target ns: mtv-test
2) The plan is Ready, start the plan
3) The plan is hang, as the inspection pod in mtv-test namespace, it fails to add the transfer network: openshift-mtv/br-eno8403. We need to block the migration when the target namespace don't have permission to the transfer network.
More details in attached files: warm-rhel-transfer-2ns-vm-1009-inspection-74j4s-describe, warm-rhel-transfer-2ns-vm-1009-inspection-74j4s-yam
# oc describe pod warm-rhel-transfer-2ns-vm-1009-inspection-74j4s|grep Events -A 10 Events: Type Reason Age From Message ---- ------ ---- ---- ------- Warning FailedCreatePodSandBox 88s (x6362 over 23h) kubelet (combined from similar events): Failed to create pod sandbox: rpc error: code = Unknown desc = failed to create pod network sandbox k8s_warm-rhel-transfer-2ns-vm-1009-inspection-74j4s_mtv-test_dce26c36-83ff-42e4-9526-b3c65ce7430e_0(3fcf9201c6a685803a4978e21d7597f38ee1174203d157e85c3052697b5ae4a5): error adding pod mtv-test_warm-rhel-transfer-2ns-vm-1009-inspection-74j4s to CNI network "multus-cni-network": plugin type="multus-shim" name="multus-cni-network" failed .... Path:"" ERRORED: error configuring pod [mtv-test/warm-rhel-transfer-2ns-vm-1009-inspection-74j4s] networking: Multus: [mtv-test/warm-rhel-transfer-2ns-vm-1009-inspection-74j4s/dce26c36-83ff-42e4-9526-b3c65ce7430e]: error loading k8s delegates k8s args: TryLoadPodDelegates: error in getting k8s network for pod: GetNetworkDelegates: namespace isolation enabled, annotation violates permission, pod is in namespace mtv-test but refers to target namespace openshift-mtv
Actual results:
In step2,3: The plan is hang
Expected results:
In step2,3: The plan is blocked with error message
Additional info: