-
Bug
-
Resolution: Duplicate
-
Normal
-
None
-
Logging 6.2.3
-
Incidents & Support
-
0
-
False
-
-
False
-
NEW
-
NEW
-
Release Note Not Required
-
-
-
-
Log Storage - Sprint 273
-
Important
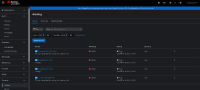
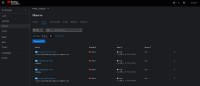
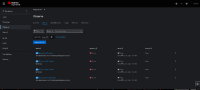
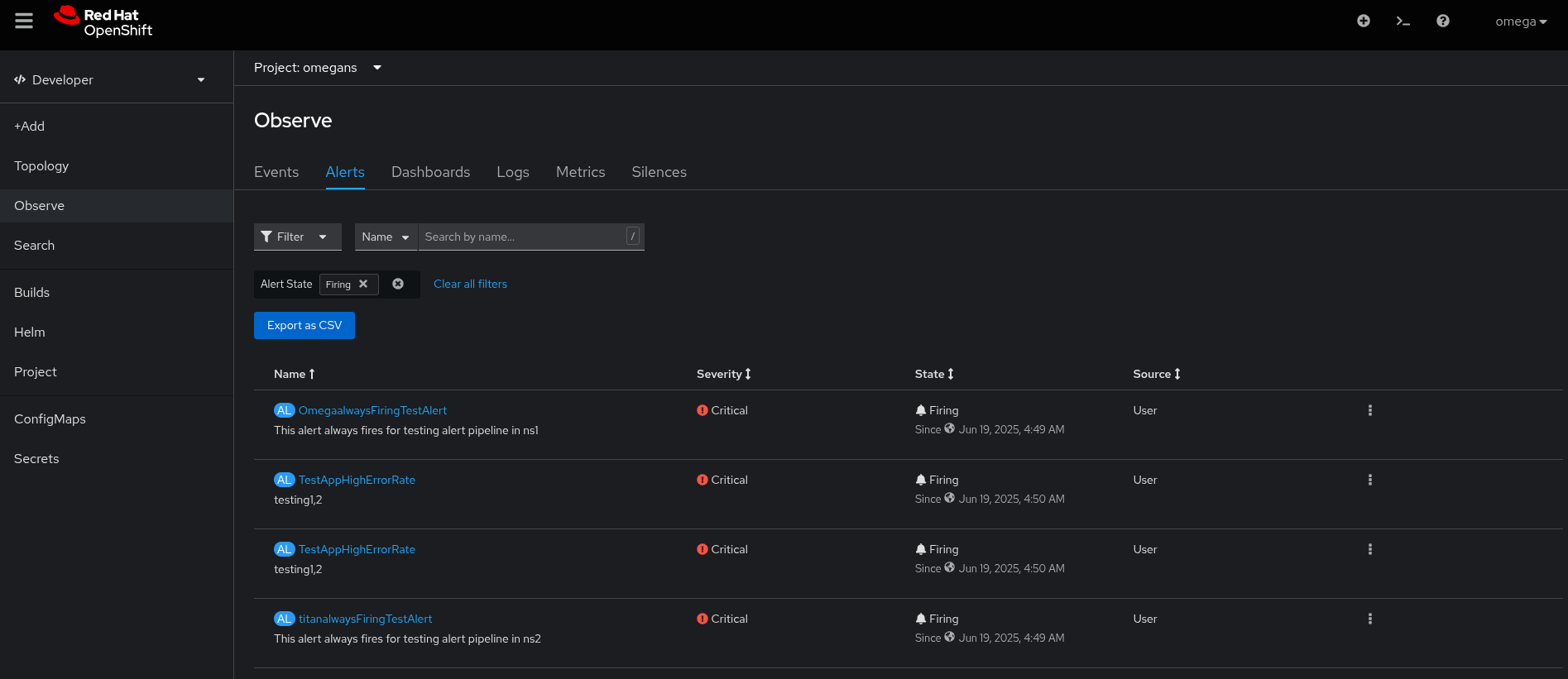
- Non-admin users can see Alerts from different namespaces in the Observe> Alerts section under the Developer web console.
Current Results:
- Non-admin users can see Alerts from different namespaces in the Observe> Alerts section under the Developer web console.
Expected Results:
- Non-admin users should only see Alerts from their own namespaces in the Observe> Alerts section under the Developer web console.
- Operator version:
$ oc get csv NAME DISPLAY VERSION REPLACES PHASE cluster-logging.v6.2.3 Red Hat OpenShift Logging 6.2.3 cluster-logging.v6.2.2 Succeeded cluster-observability-operator.v1.2.0 Cluster Observability Operator 1.2.0 cluster-observability-operator.v1.1.1 Succeeded loki-operator.v6.2.3 Loki Operator 6.2.3 loki-operator.v6.2.2 Succeeded
- Non-admin usernames: "titan" and "omega"
- Non-admin user "titan" is able to view alerts from other namespaces, including those to which he does not have access:
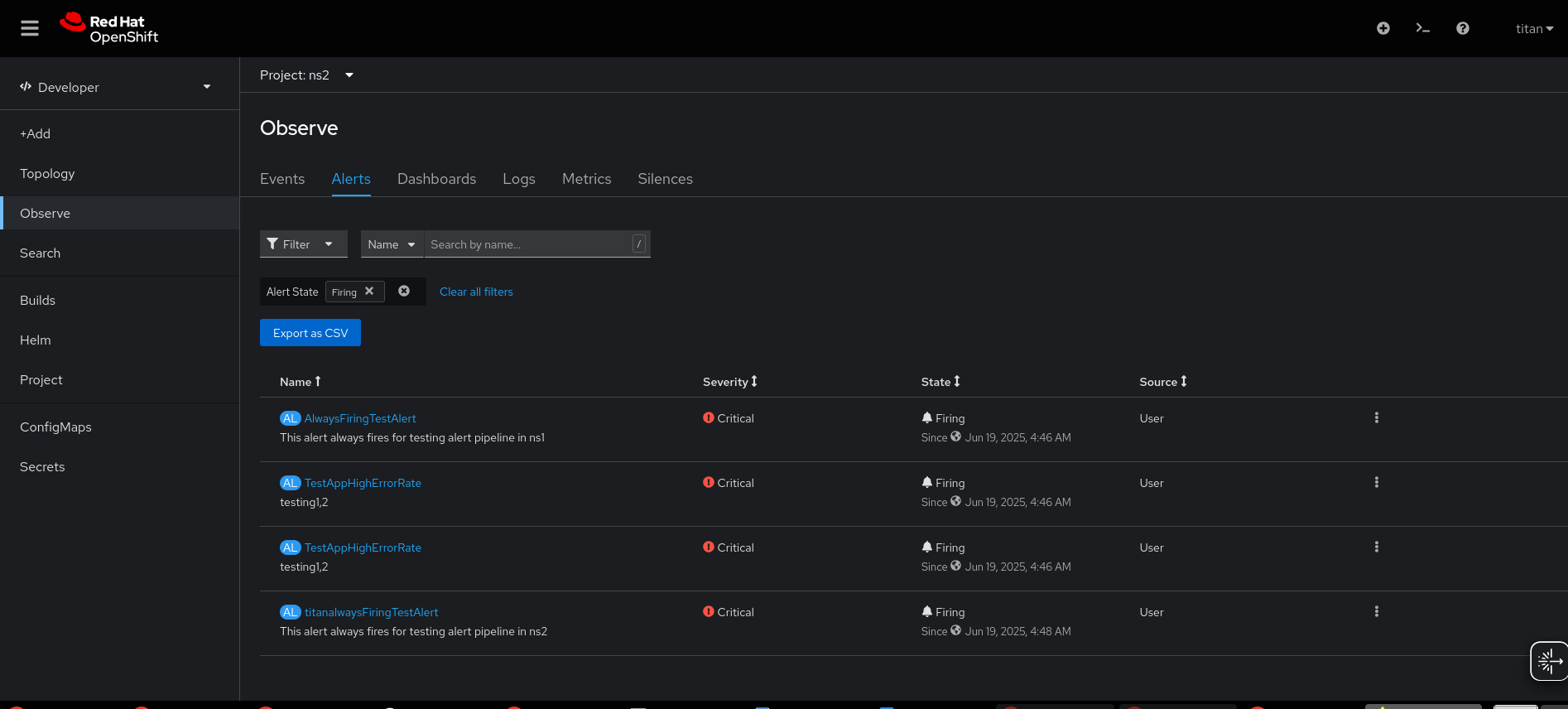
- Non-admin user "omega" is able to view alerts from other namespaces, including those to which he does not have access:
- Alertingrules:
$ oc get alertingrule -n omegans NAME AGE always-firing-alert 4h26m ------- $ oc get alertingrule -n ns2 NAME AGE titan-always-firing-alert 15m
- Additional Information:
$ oc get rolebindings -A -o json | jq '.items[] | select(.subjects[0].name=="omega")' | jq '[.roleRef.name,.metadata.namespace]' [ "admin", "omegans" ] [ "monitoring-rules-view", "omegans" ] [ "cluster-logging-application-view", "omegans" ] [ "user-settings-09f8d780-2880-4265-8aa7-c6159a4c317b-role", "openshift-console-user-settings" ] ======== $ oc get rolebindings -A -o json | jq '.items[] | select(.subjects[0].name=="titan")' | jq '[.roleRef.name,.metadata.namespace]' [ "admin", "ns2" ] [ "monitoring-rules-view", "ns2" ] [ "cluster-logging-application-view", "ns2" ] [ "user-settings-a4ff45d6-7975-4a03-9707-a98f0dba67a2-role", "openshift-console-user-settings" ]
- Screenshot of the firing alerts from Kube:Admin:
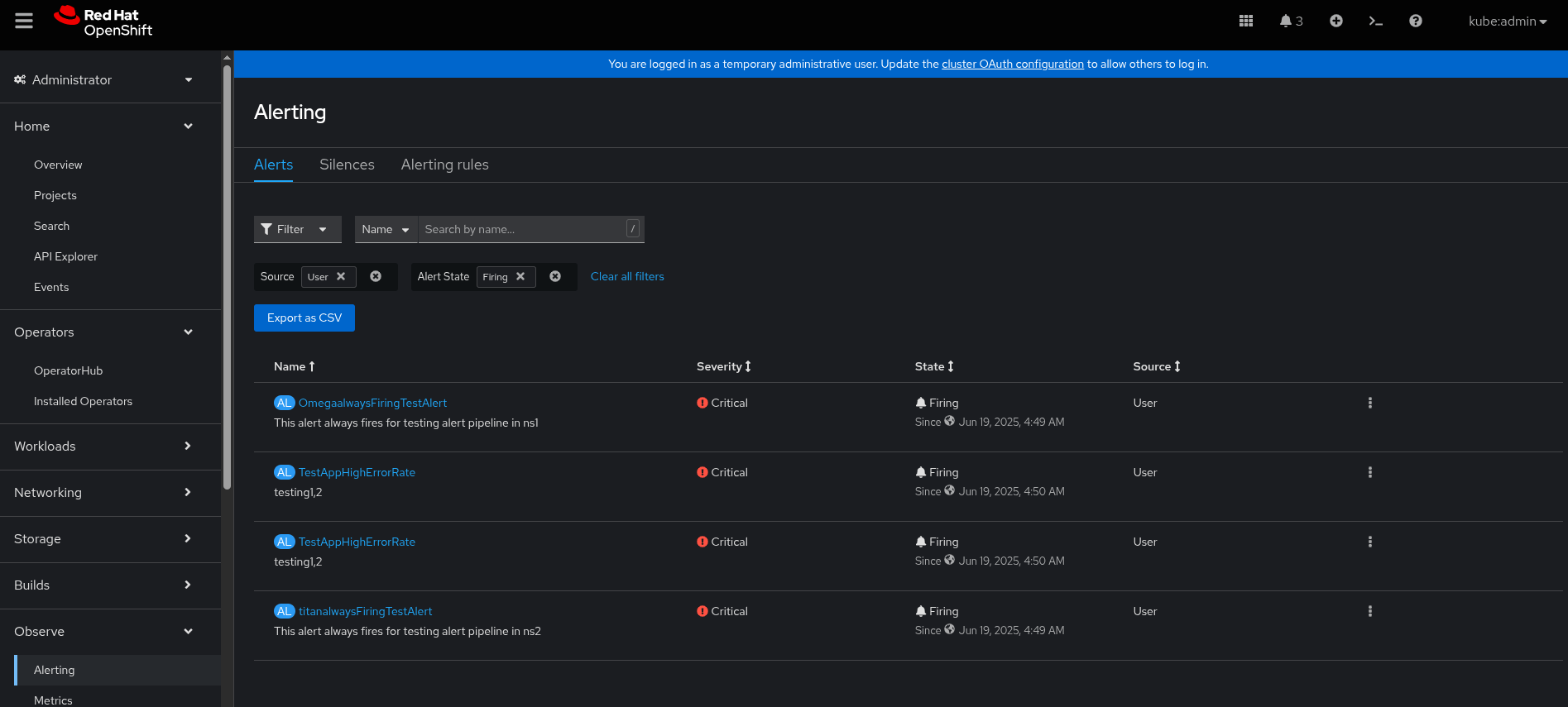
- Alert: OmegaalwaysFiringTestAlert ==> [namespace: omegans] [user: omega]
- Alert: titanalwaysFiringTestAlert ===> [namespace: ns2] [user: titan]
- Alert: TestAppHighErrorRate ===> [namespace: ns-testapp-logalert] [user: rolex]
- Alert: TestAppHighErrorRate ===> [namespace: ns1] [user: rolex]
- duplicates
-
LOG-6148 Loki log based alerts for application tenant are not filtered by namespace on dev-console
-
- Closed
-