-
Bug
-
Resolution: Duplicate
-
Normal
-
None
-
Logging 6.3.0
-
Incidents & Support
-
False
-
-
False
-
NEW
-
NEW
-
Bug Fix
-
-
-
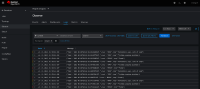
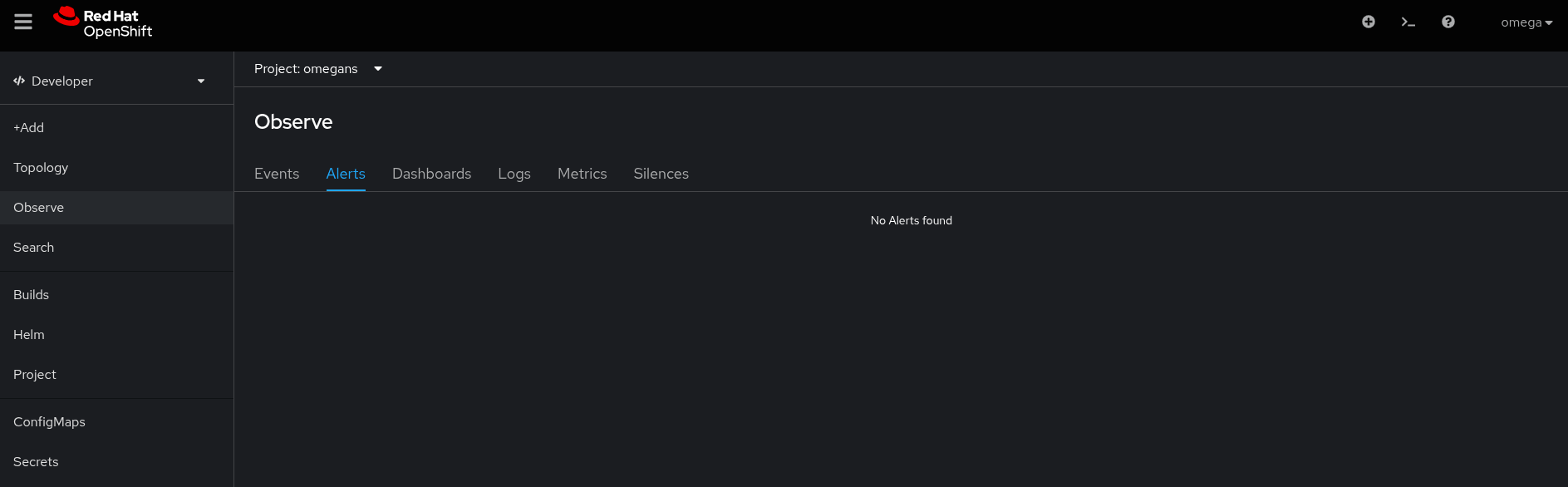
- Non-admin users are unable to see their own namespace alerts in the Observe> Alerts section under the Developer web console.
- Getting `No alerts found` error.
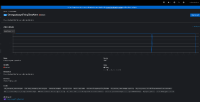
- Non-admin user can see logs in => Observe > Logs section under the Developer web console.
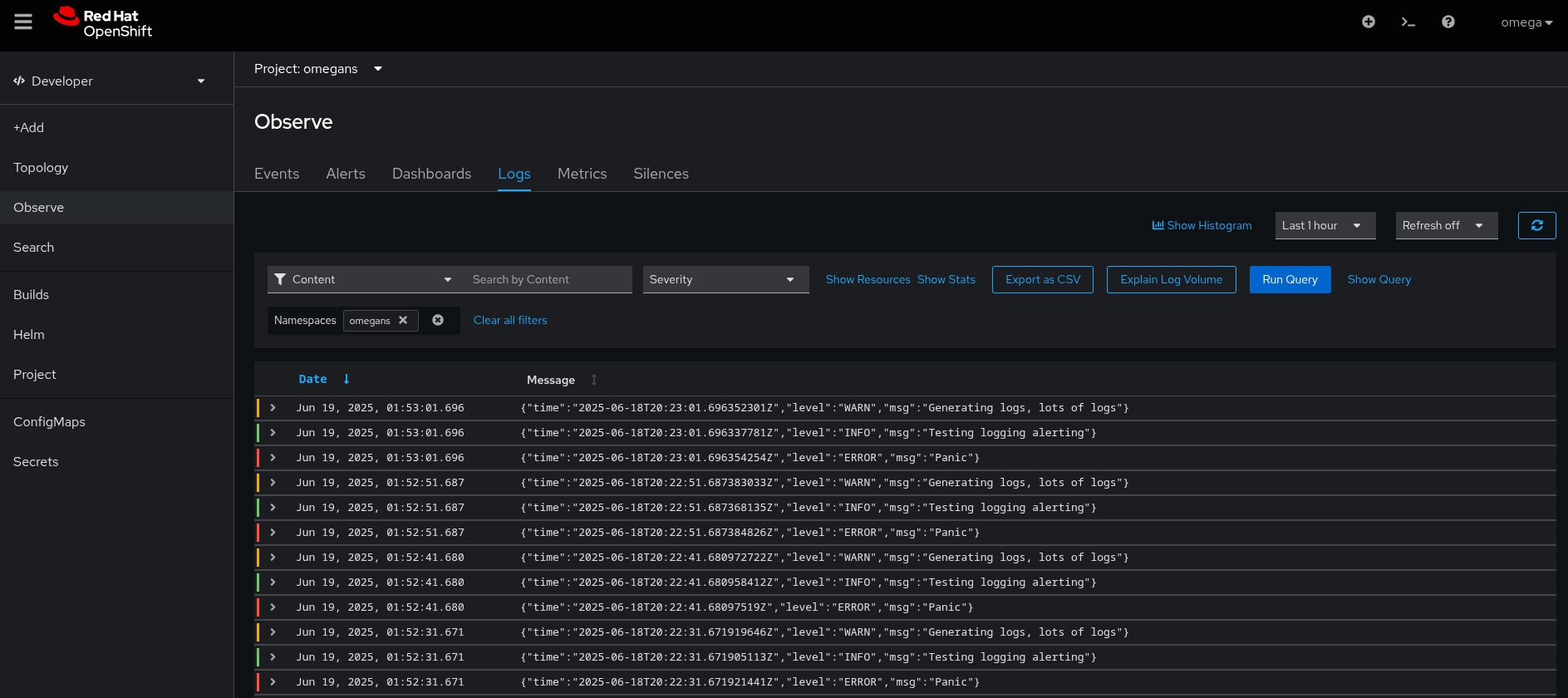
- In the above screenshots, the username is `omega`, which is a non-admin user.
- `omega` user having access of `omegans` namespace.
- Below alert is firing in the `omegans` namespace:
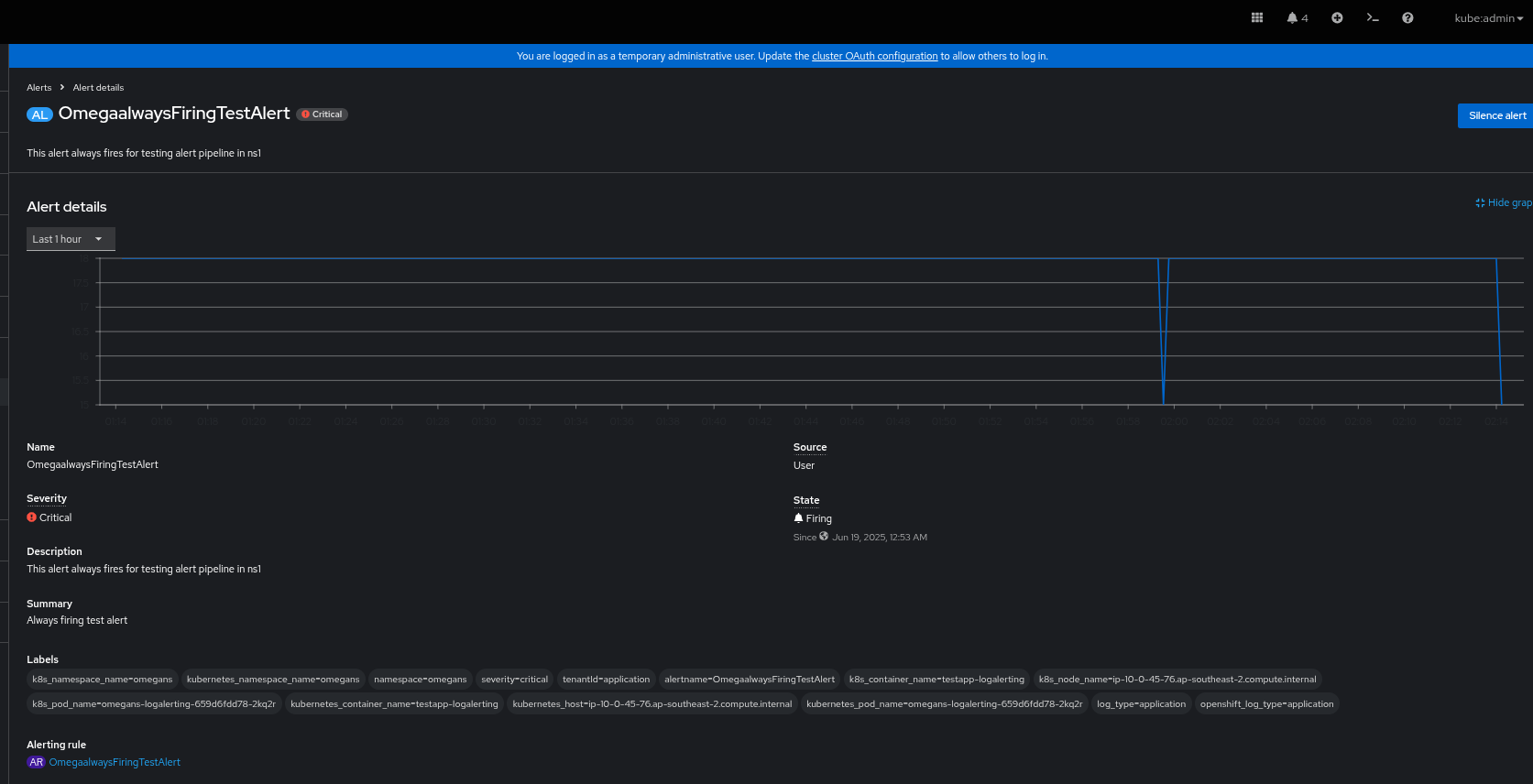
- But `omega` user can not see this alert in the Developer > Observe > Alerts section.
- Here is the operator version:
$ oc get csv -n openshift-loggingNAME DISPLAY VERSION REPLACES PHASE cluster-logging.v6.3.0 Red Hat OpenShift Logging 6.3.0 cluster-logging.v6.2.3 Succeeded cluster-observability-operator.v1.2.0 Cluster Observability Operator 1.2.0 cluster-observability-operator.v1.1.1 Succeeded loki-operator.v6.3.0 Loki Operator 6.3.0 loki-operator.v6.2.3 Succeeded
- Additional information:
$ oc get rolebindings -A -o json | jq '.items[] | select(.subjects[0].name=="omega")' | jq '[.roleRef.name,.metadata.namespace]' [ "admin", "omegans" ] [ "monitoring-rules-view", "omegans" ] [ "cluster-logging-application-view", "omegans" ] [ "user-settings-09f8d780-2880-4265-8aa7-c6159a4c317b-role", "openshift-console-user-settings" ]
- The same scenario is working fine in previous logging/lokistack versions.
Current Results:
- `omega` user not able to see own namespace alerts in the Observe> Alerts section under the Developer web console.
Expected Results:
- `omega` user should be able to see their own namespace alerts in the Observe> Alerts section under the Developer web console.
- relates to
-
LOG-7289 Unauthorized access error when non-admin users query for rules and firing alerts
-
- Closed
-