-
Feature
-
Resolution: Unresolved
-
Medium
-
None
-
None
-
None
-
Product / Portfolio Work
-
False
-
-
False
-
Not Selected
-
0
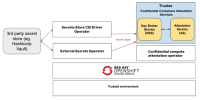
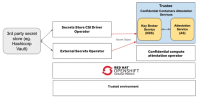
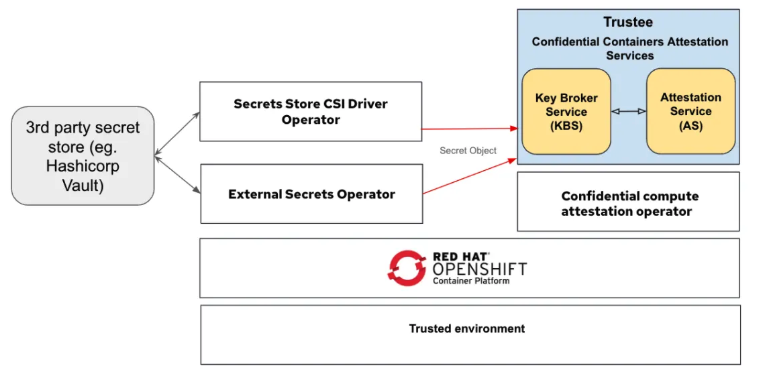
The Trustee Operator simplifies how Trusted Execution Environments (TEEs) are granted access to secrets in OpenShift. You can store TEE-specific secrets (keys, certificates, etc.) as OpenShift Secret objects or pull them from external managers (e.g., HashiCorp Vault) using the Secrets Store CSI Driver. The Trustee Operator then uses attestation to verify the integrity of the TEE before securely delivering these secrets.
- Acceptanc criteria
- Documentation & Blog Post
- Provide official documentation and a blog article that describes end-to-end steps for using the Trustee Operator and the Secrets Store CSI Driver operator together.
- as a how-to, include or link to details on how to configure a supported key vault (for example, HashiCorp Vault or AWS Secrets Manager) and integrate it with the Secrets Store CSI Driver.
- Documentation & Blog Post
-
- Configuration Instructions
- Clearly document each required component (Trustee Operator, Secrets Store CSI Driver, key vault provider).
- Provide example YAML manifests and step-by-step procedures so users can easily replicate the setup to fetch secrets from the external key vault.
s
- Automated Test Case
- Configuration Instructions
-
-
- Develop an end-to-end test suite that covers:
- Version compatibility: Validate on supported OCP versions (or cluster setups).
- Configuration validation: Confirm that when properly configured, secrets are successfully pulled from the external key vault.
- Attestation enforcement: Ensure secrets are only accessible in the target TEE after Trustee attestation succeeds.
- Document how to run the tests and interpret results.
- Develop an end-to-end test suite that covers:
-
https://docs.google.com/document/d/12TjoXTR_66HfGOclAGQGwj4QwzBpKVShv7loWd7fsdQ/edit?tab=t.0