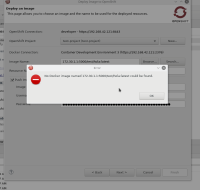
-
Bug
-
Resolution: Unresolved
-
Major
-
4.5.1.AM1
-
devex #169 July 2019, devex #172 Sep 2019, devex #171 Aug 2019, devex #173 Oct 2019, devex #174 Oct 2019, devex #175 Nov 2019, devex #176 Nov/Dec 2019
-
13
-
Exception in Error log:
Failed to inspect image: '172.30.1.1:5000/test/hola:latest' com.spotify.docker.client.exceptions.ImageNotFoundException: Image not found: 172.30.1.1:5000/test/hola:latest at com.spotify.docker.client.DefaultDockerClient.inspectImage(DefaultDockerClient.java:1330) at org.eclipse.linuxtools.internal.docker.core.DockerConnection.getImageInfo(DockerConnection.java:896) at org.jboss.tools.openshift.internal.ui.wizard.deployimage.DeployImageWizardModel.lookupImageMetadata(DeployImageWizardModel.java:655) at org.jboss.tools.openshift.internal.ui.wizard.deployimage.DeployImageWizardModel.initializeContainerInfo(DeployImageWizardModel.java:354) at org.jboss.tools.openshift.internal.ui.wizard.deployimage.DeployImagePage$1ImageValidatorJob.run(DeployImagePage.java:154) at org.eclipse.core.internal.jobs.Worker.run(Worker.java:56) Caused by: com.spotify.docker.client.exceptions.DockerRequestException: Request error: GET https://192.168.42.121:2376/images/172.30.1.1:5000/test/hola:latest/json: 404 at com.spotify.docker.client.DefaultDockerClient.propagate(DefaultDockerClient.java:2084) at com.spotify.docker.client.DefaultDockerClient.request(DefaultDockerClient.java:2023) at com.spotify.docker.client.DefaultDockerClient.inspectImage(DefaultDockerClient.java:1326) ... 5 more Caused by: javax.ws.rs.NotFoundException: HTTP 404 Not Found at org.glassfish.jersey.client.JerseyInvocation.convertToException(JerseyInvocation.java:1008) at org.glassfish.jersey.client.JerseyInvocation.translate(JerseyInvocation.java:816) at org.glassfish.jersey.client.JerseyInvocation.access$700(JerseyInvocation.java:92) at org.glassfish.jersey.client.JerseyInvocation$5.completed(JerseyInvocation.java:773) at org.glassfish.jersey.client.ClientRuntime.processResponse(ClientRuntime.java:198) at org.glassfish.jersey.client.ClientRuntime.access$300(ClientRuntime.java:79) at org.glassfish.jersey.client.ClientRuntime$2.run(ClientRuntime.java:180) at org.glassfish.jersey.internal.Errors$1.call(Errors.java:271) at org.glassfish.jersey.internal.Errors$1.call(Errors.java:267) at org.glassfish.jersey.internal.Errors.process(Errors.java:315) at org.glassfish.jersey.internal.Errors.process(Errors.java:297) at org.glassfish.jersey.internal.Errors.process(Errors.java:267) at org.glassfish.jersey.process.internal.RequestScope.runInScope(RequestScope.java:340) at org.glassfish.jersey.client.ClientRuntime$3.run(ClientRuntime.java:210) at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:511) at java.util.concurrent.FutureTask.run(FutureTask.java:266) at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) at java.lang.Thread.run(Thread.java:748) eclipse.buildId=11.1.0.AM1-v20170824-1835-B873 java.version=1.8.0_141 java.vendor=Oracle Corporation BootLoader constants: OS=linux, ARCH=x86_64, WS=gtk, NL=en_US Framework arguments: -product com.jboss.devstudio.core.product Command-line arguments: -os linux -ws gtk -arch x86_64 -product com.jboss.devstudio.core.product
- is related to
-
JBIDE-24498 Deploy Docker Image wizard: results dialog is not very informative
-
- Closed
-
- relates to
-
JBIDE-24501 Deploy Docker Image wizard: NPE when trying to deploy image previously pushed to docker registry
-
- Closed
-
-
JBIDE-26857 Deploy to OpenShift: when pushing to registry, registry url is not informed
-
- Open
-