-
Bug
-
Resolution: Obsolete
-
Major
-
None
-
7.1.0.CR3
-
None
-
Release Notes
-
-
-
-
-
-
Workaround Exists
-
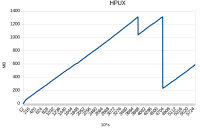
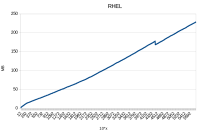
Memory leak in XNIO on Server is ssl is used. This issue is valid only on HPUX platform.
This issue was find during JBEAP-11888 verification. This issue occurs only if workaround for JBEAP-11859, JBEAP-13545 and JBEAP-13547 is used. JBEAP-11859 issue is present in EAP since EAP 7.1.0.ER1.
Steps to reproduce
- configure https (one-way or two-way ssl)
- ignore errors related with
JBEAP-11859,JBEAP-13545andJBEAP-13547 - do this in loop:
ModelControllerClientConfiguration config = new ModelControllerClientConfiguration.Builder() .setProtocol(server.getManagementProtocol()) .setHostName("127.0.0.1") .setPort(server.getManagementPort()) .setConnectionTimeout(timeout) .build(); ModelControllerClient c = ModelControllerClient.Factory.create(config); DefaultOperationRequestBuilder builder = new DefaultOperationRequestBuilder(); builder.setOperationName(org.jboss.as.cli.Util.READ_ATTRIBUTE); builder.addProperty(org.jboss.as.cli.Util.NAME, "server-state"); ModelNode result = c.execute(builder.buildRequest());
Exception on server:
2017-10-30 03:54:59,468 ERROR [org.xnio.listener] (management I/O-1) XNIO001007: A channel event listener threw an exception: java.lang.OutOfMemoryError
at sun.misc.Unsafe.allocateMemory(Native Method)
at java.nio.DirectByteBuffer.<init>(DirectByteBuffer.java:127)
at java.nio.ByteBuffer.allocateDirect(ByteBuffer.java:311)
at org.xnio.ByteBufferPool$1.createBuffer(ByteBufferPool.java:510)
at org.xnio.ByteBufferPool.allocateMaster(ByteBufferPool.java:499)
at org.xnio.ByteBufferPool.access$000(ByteBufferPool.java:41)
at org.xnio.ByteBufferPool$DefaultCache.allocate(ByteBufferPool.java:776)
at org.xnio.ByteBufferPool.allocate(ByteBufferPool.java:160)
at org.xnio.ByteBufferPool$2.createBuffer(ByteBufferPool.java:531)
at org.xnio.ByteBufferPool.allocateMaster(ByteBufferPool.java:499)
at org.xnio.ByteBufferPool.access$000(ByteBufferPool.java:41)
at org.xnio.ByteBufferPool$DefaultCache.allocate(ByteBufferPool.java:776)
at org.xnio.ByteBufferPool.allocate(ByteBufferPool.java:160)
at org.xnio.ByteBufferPool.allocate(ByteBufferPool.java:184)
at org.xnio.ByteBufferPool.allocate(ByteBufferPool.java:170)
at org.jboss.remoting3.remote.MessageReader.getMessage(MessageReader.java:123)
at org.jboss.remoting3.remote.RemoteReadListener.handleEvent(RemoteReadListener.java:73)
at org.jboss.remoting3.remote.RemoteReadListener.handleEvent(RemoteReadListener.java:46)
at org.xnio.ChannelListeners.invokeChannelListener(ChannelListeners.java:92)
at org.xnio.conduits.ReadReadyHandler$ChannelListenerHandler.readReady(ReadReadyHandler.java:66)
at io.undertow.protocols.ssl.SslConduit$SslReadReadyHandler.readReady(SslConduit.java:1131)
at org.xnio.nio.NioSocketConduit.handleReady(NioSocketConduit.java:89)
at org.xnio.nio.WorkerThread.run(WorkerThread.java:571)
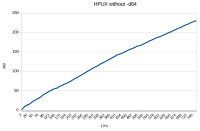
GC log from RHEL (this issue doesn't occur): rhel.gc.log![]()
GC log from HPUX (this issue occurs): hpux.cr3.two-way-ssl.gc.log![]()
HeapDump: TBD
- relates to
-
JBEAP-9474 OOM unable to create new native thread from basic module on HP-UX boxes
-
- Closed
-
-
JBEAP-11888 (7.1.0) Connection timeout CLI issue on HTTPS, if more cli clients are used in a loop.
-
- Closed
-
-
JBEAP-11859 "WFLYPRT0060: Channel open request timed out" exception on CLI class
-
- Closed
-