-
Bug
-
Resolution: Done
-
Critical
-
None
-
None
-
False
-
False
-
None
-
HAC Infra OCM - Sprint 239, HAC Infra OCM - Sprint 240
Description of problem:
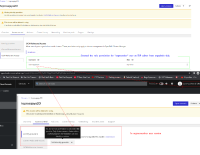
An org member user has granted with role permission "Identity provider editor" for a cluster. But in org member login session, the UI options to add or configure a new identity provider for the cluster is disabled. It looks like a wrong behavior.
 CLI Role binding definition after granting role as below
CLI Role binding definition after granting role as below
ocm get /api/accounts_mgmt/v1/subscriptions/2RSLSuDSL9WpjOCtnI3PeFDgK2x/role_bindings
{
"items": [
{
"account": {
"href": "/api/accounts_mgmt/v1/accounts/1TBa2A3mL0wcoYHlBgt0xTxfJNA",
"id": "1TBa2A3mL0wcoYHlBgt0xTxfJNA",
"kind": "Account"
},
"account_email": "",
"account_username": "",
"created_at": "2023-06-20T07:38:53.179865Z",
"href": "/api/accounts_mgmt/v1/subscriptions/2RSLSuDSL9WpjOCtnI3PeFDgK2x/role_bindings/2RSc4gfOiwpGwc6v2sR4aisXGiJ",
"id": "2RSc4gfOiwpGwc6v2sR4aisXGiJ",
"kind": "RoleBinding",
"role": {
"href": "/api/accounts_mgmt/v1/roles/IdpEditor",
"id": "IdpEditor",
"kind": "Role"
},
"subscription": {
"href": "/api/accounts_mgmt/v1/subscriptions/2RSLSuDSL9WpjOCtnI3PeFDgK2x",
"id": "2RSLSuDSL9WpjOCtnI3PeFDgK2x",
"kind": "Subscription"
},
"updated_at": "2023-06-20T07:38:53.179865Z"
}
],
"kind": "SubscriptionRoleBindingList",
"page": 1,
"size": 1,
"total": 1
}
How reproducible:
Always
Steps to reproduce:
- Launch OCM UI staging and login as org-admin user.
- Open a ROSA hypershift cluster.
- Go to access control tab > OCM roles and access , click "Grant" button.
- Input Redhat login with a valid user name (ex: use a org-member user)
- Select Role as Identity provider editor and Click on "Grant role".
- Login to OCM UI Staging with the user granted permission in step 4 .
- Select and Open the cluster(same as step 2).
- Go to "Access control" tab > "Identity provider "and try to add the new IDP.
- Go to "Access control" tab> "OCM Roles and access" and try to grant a role.
Actual results:
The Access control section restricted to the user from adding new IDP or granting roles etc although user has granted with the role "Identity provider editor".
Expected results:
The Access control section should not restrict the user from adding new IDP or granting roles etc when user granted with the role "Identity provider editor".
- relates to
-
HAC-4273 [ROSA Hypershift] "OIDC and operator roles" cluster installation step is waiting state when no operator roles created prior to installation.
-
- Closed
-
- mentioned on