-
Bug
-
Resolution: Unresolved
-
Major
-
1.2.0, ROS-PLUGIN-1.2.1
-
False
-
-
False
-
-
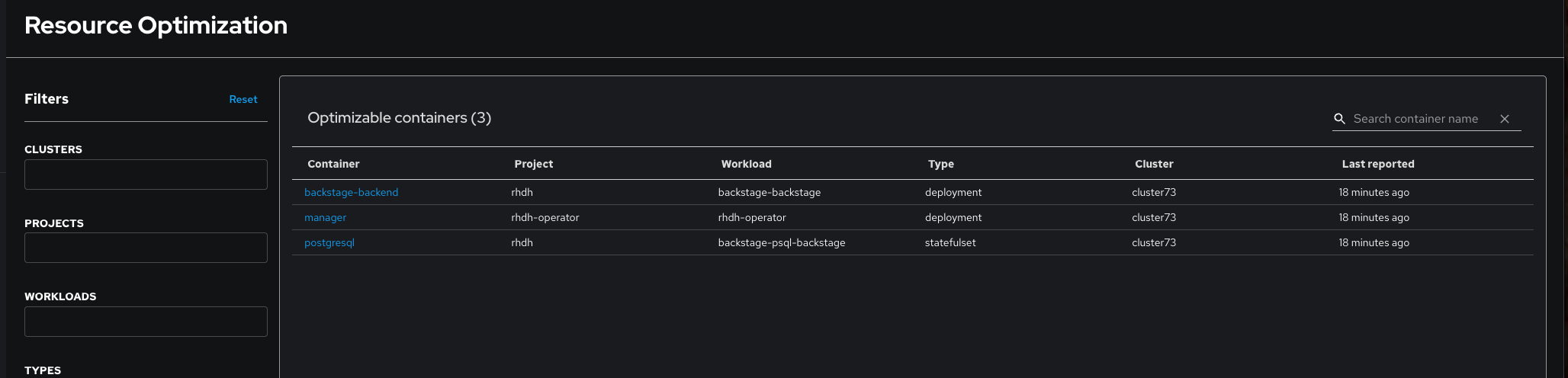
Description of the problem: When a user is assigned RBAC permissions scoped to a specific project, such as rhdh, the Resource Optimization UI is incorrectly displaying resources from other projects that share a similar prefix, like rhdh-operator. This indicates that the backend permission check for ros.${clusterId}.${projectId} is likely using a "starts-with" or "contains" string match instead of an exact match on the project name, leading to unintended access and a confusing user experience.
The current RBAC configuration is as follows:
p, role:default/ROClusterProject, ros.cluster73.rhdh, read, allow
g, user:default/rhdh-orchestrator-test-1, role:default/ROClusterProject
This configuration should restrict the rhdh-orchestrator-test-1 user to see resources only in the rhdh project on cluster73.
How reproducible: Always
Steps to reproduce:
- Configure a user (rhdh-orchestrator-test-1) with the specific ROClusterProject role, granting read access only to the rhdh project on cluster73.
- Log in to the UI as the rhdh-orchestrator-test-1 user.
- Navigate to the Resource Optimization page and view the list of optimizable containers.
Actual results: The UI displays containers from both the rhdh project and the rhdh-operator project. (See attached screenshot).
Expected results: The UI should only display containers belonging to the rhdh project. Containers from the rhdh-operator project or any other project should be filtered out and not be visible to the user, correctly enforcing the configured RBAC policy.
- is related to
-
FLPATH-2465 [qe] handle ros.${clusterId}.${projectId} Permission to apply RBAC filtering as per Cluster and Project name
-
- Closed
-