-
Story
-
Resolution: Won't Do
-
Undefined
-
None
-
None
The operator pod and the broker pods can run with a safer and restricted security context without issues. Restricting the security context of the pods by default allows to deploy a cluster of brokers also in Kubernetes namespaces with the restricted policy.
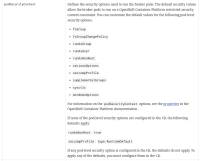
The minimal changes to run the pods in Kubernetes namespaces with the restricted policy:
- spec.containers[*].securityContext.allowPrivilegeEscalation: false
- spec.initContainers[*].securityContext.allowPrivilegeEscalation: false
- spec.ephemeralContainers[*].securityContext.allowPrivilegeEscalation: false
- spec.securityContext.runAsNonRoot: true
- spec.containers[*].securityContext.runAsNonRoot: true
- spec.initContainers[*].securityContext.runAsNonRoot: true
- spec.ephemeralContainers[*].securityContext.runAsNonRoot: true
- spec.securityContext.seccompProfile.type: RuntimeDefault
- spec.containers[*].securityContext.seccompProfile.type: RuntimeDefault
- spec.initContainers[*].securityContext.seccompProfile.type: RuntimeDefault
- spec.ephemeralContainers[*].securityContext.seccompProfile.type: RuntimeDefault
- spec.containers[*].securityContext.capabilities.drop: ["ALL"]
- spec.initContainers[*].securityContext.capabilities.drop: ["ALL"]
- spec.ephemeralContainers[*].securityContext.capabilities.drop: ["ALL"]
- is cloned by
-
ENTMQBR-8896 [Docs] Restrict security context of pods by default
-
- Closed
-