-
Story
-
Resolution: Done
-
Blocker
-
None
-
AMQ 7.10.0.OPR.1.GA
-
None
-
False
-
-
False
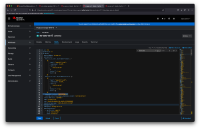
Pod security change is coming in OCP 4.11 and 4.12 and Kube 1.25
Enabling pod security admission (https://kubernetes.io/docs/concepts/security/pod-security-admission/) using the “restricted” profile by default (https://kubernetes.io/docs/concepts/security/pod-security-standards/) for OpenShift 4.11.
Note that this will be a WARN in OCP 4.11 and set to ENFORCING in OCP 4.12
It will do this via changes to the SCCs in use:
Prior to 4.11 - no platform SCCs met the “restricted” PSa profile
Added three new SCCs:
restricted-v2, hostnetwork-v2, nonroot-v2
These:
Drop ALL container capabilities
Default seccomp profile to “runtime/default”
Don’t allow running binaries with SUID bits in containers
Likely need to see about moving to the restricted-v2 profile and ensuring everything still works.
Also need to update the bundle com.redhat.openshift.versions to ensure we extend the range to include 4.12
- is cloned by
-
ENTMQIC-3327 Add support for "Pod Security Admission"
-
- New
-
- is related to
-
ENTMQBR-7921 AMQ 7.10 and 7.11 installation fails on Microshift 4.12.10 but works on 4.12.6
-
- Closed
-
-
AUTH-312 Review telemetry data to determine if restricted enforcement will break customers
-
- Closed
-
-
OTA-784 Check PodSecurityViolation behavior on 4.11 to 4.12 updates
-
- Closed
-
- relates to
-
ENTMQBR-4679 Adding support to define PodSecurityContext
-
- Closed
-
-
ENTMQBR-8558 Make sure the operator is aligned with latest PSA requirement
-
- Closed
-
-
ENTMQBR-7386 Document AMQ Broker Operator behavior wih regard to Pod Security Admission
-
- Closed
-
-
ENTMQBR-7462 [QE] RE-test Pod Security Admissions feature when this feature is enabled by OCP and enforced
-
- Closed
-