-
Bug
-
Resolution: Done
-
Critical
-
1.1.0.GA, 1.2.0.GA
-
OCP 4.0-0.8 installed on AWS here: https://console-openshift-console.apps.crw.codereadyqe.com/
CRW 1.1.0.GA RC1/2
Command to install:
```
wget https://codeready-workspaces-jenkins.rhev-ci-vms.eng.rdu2.redhat.com/view/CRW_CI/view/Pipelines/job/crw-operator-installer-and-ls-deps_stable-branch/34/artifact/codeready-workspaces-deprecated/operator-installer/target/codeready-workspaces-operator-installer.tar.gz
tar -xvf codeready-workspaces-operator-installer.tar.gzcodeready-workspaces-operator-installer/deploy.sh -d \
--server-image=quay.io/crw/server-container \
--version=1.1-52 \
--operator-image=quay.io/crw/operator-container:1.1-18 \
--oauth
```OCP 4.0-0.8 installed on AWS here: https://console-openshift-console.apps.crw.codereadyqe.com/ CRW 1.1.0.GA RC1/2 Command to install: ``` wget https://codeready-workspaces-jenkins.rhev-ci-vms.eng.rdu2.redhat.com/view/CRW_CI/view/Pipelines/job/crw-operator-installer-and-ls-deps_stable-branch/34/artifact/codeready-workspaces-deprecated/operator-installer/target/codeready-workspaces-operator-installer.tar.gz tar -xvf codeready-workspaces-operator-installer.tar.gz codeready-workspaces-operator-installer/deploy.sh -d \ --server-image=quay.io/crw/server-container \ --version=1.1-52 \ --operator-image=quay.io/crw/operator-container:1.1-18 \ --oauth ```
Test case:
1. Go to CRW login page.
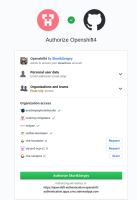
2. Click on OpenShift v3 button.
3. Log into OCP as a regular user with basic-user role with httpasswd identity.
4. Click on "Allow" button in OpenShift oAuth application page.
Expected result:
- form to enter CRW profile info is opened
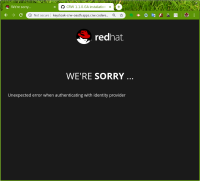
Actual wrong result:
- page with error message
WE'RE SORRY ... Unexpected error when authenticating with identity provider
and url "http://keycloak-crw-oauth.apps.crw.codereadyqe.com/auth/realms/codeready/broker/openshift-v3/endpoint?code=4Sek5sNS6uBO-SWAqlh5fIbDSWQas-g9e_QdpzTqOPs&state=9vm-melw4ZB9hNDwh23e9dD8mJQtLS6MRUWnPQyPsTo.8SsDsLZzkCw.codeready-public"
There was next error message in keycloak console:
�[0m�[31m18:00:47,663 ERROR [org.keycloak.broker.oidc.AbstractOAuth2IdentityProvider] (default task-5) Failed to make identity provider oauth callback: org.keycloak.broker.provider.IdentityBrokerException: Could not obtain user profile from Openshift.
at org.keycloak.social.openshift.OpenshiftV3IdentityProvider.doGetFederatedIdentity(OpenshiftV3IdentityProvider.java:54)
at org.keycloak.broker.oidc.AbstractOAuth2IdentityProvider.getFederatedIdentity(AbstractOAuth2IdentityProvider.java:282)
...
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624)
at java.lang.Thread.run(Thread.java:748)
Caused by: java.lang.NullPointerException
at org.keycloak.broker.oidc.AbstractOAuth2IdentityProvider.getJsonProperty(AbstractOAuth2IdentityProvider.java:333)
at org.keycloak.social.openshift.OpenshiftV3IdentityProvider.extractUserContext(OpenshiftV3IdentityProvider.java:59)
at org.keycloak.social.openshift.OpenshiftV3IdentityProvider.doGetFederatedIdentity(OpenshiftV3IdentityProvider.java:50)
... 63 more
Possible root cause: https://github.com/keycloak/keycloak/blob/master/services/src/main/java/org/keycloak/social/openshift/OpenshiftV3IdentityProvider.java#L54
Screencast: simplescreenrecorder-2019-03-28_00.21.16.mp4![]()
Update: the same error was encountered when was tried to log into CRW:
- with OpenShift oAuth linked to GitHub oAuth in OCP 4.0;
- with OpenShift oAuth linked to LDAP.
Login through OpenShift OAuth shouldn't work with temporary default cluster admin "kubeadmin", because it doesn't have identity provider (identities = null):
curl --insecure -H "Authorization: Bearer .........." "https://api.crw.codereadyqe.com:6443/apis/user.openshift.io/v1/users/~" { "kind": "User", "apiVersion": "user.openshift.io/v1", "metadata": { "name": "kube:admin", "selfLink": "/apis/user.openshift.io/v1/users/kube%3Aadmin", "creationTimestamp": null }, "identities": null, "groups": [ "system:authenticated", "system:cluster-admins" ] }
https://github.com/eclipse/che/issues/13659#issuecomment-508040264
- clones
-
CRW-202 Cannot log into CRW with OpenShift 4.0 or 4.1 oAuth
-
- Closed
-
- links to