-
Bug
-
Resolution: Unresolved
-
Normal
-
None
-
4.21
-
Quality / Stability / Reliability
-
False
-
-
False
-
None
-
-
Moderate
-
None
Description of problem:
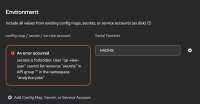
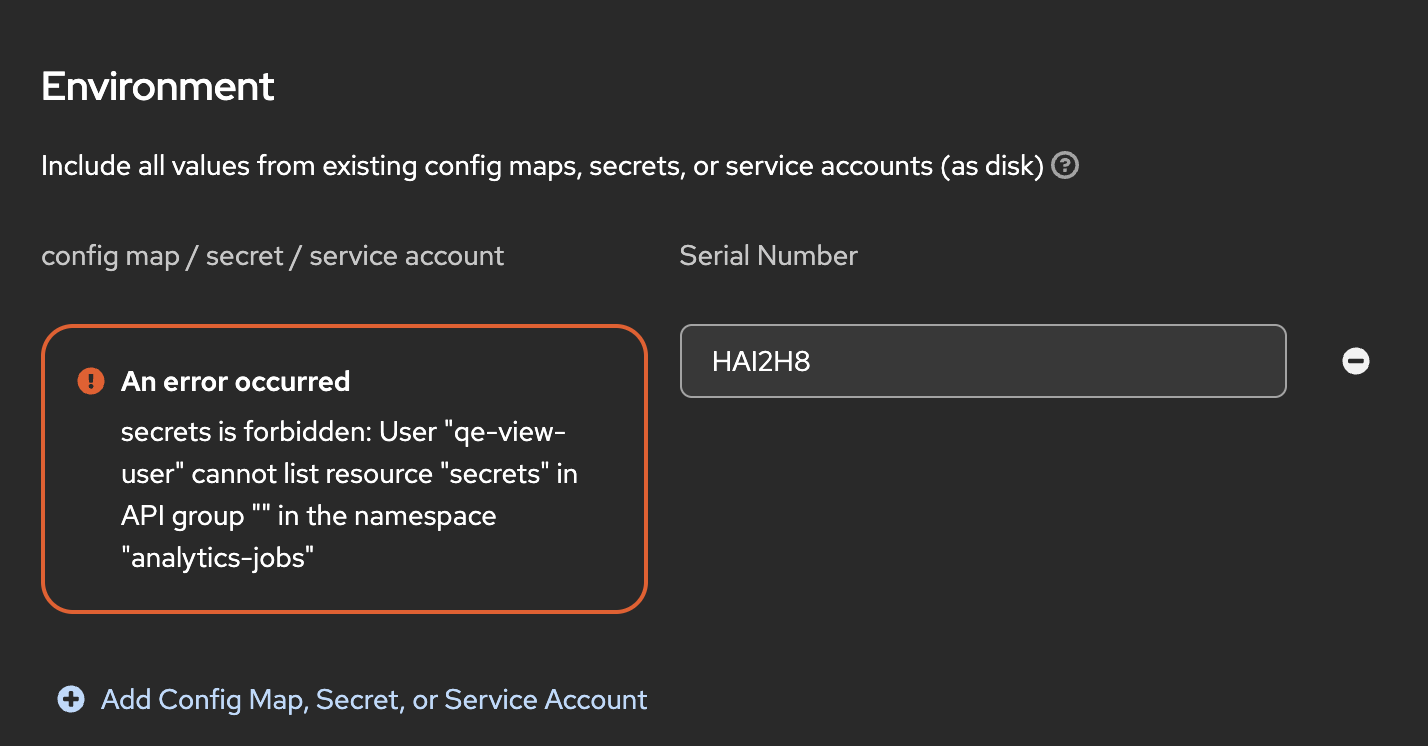
In the CNV Fleet Virtualization UI (tested with ACM 2.16 + CNV 4.21 nightly build), there is a section to mount existing configmap/secret/serviceaccount as a disk to a VM. We are testing this UI as RBAC users with least privileges, and we found that you need list permissions for all 3 resources. We would expect that if you have list permissions for configmaps but not secrets/serviceaccounts, that it should at least show configmaps. In ACM we have extra virt roles that we ship as part of ACM. One role as an example is called "acm-vm-extended:view". In this role, we give permissions for configmap and serviceaccount resources, but not secrets. We did not want to give secret permission in any of our roles due to security reasons (to avoid possibility of customer mis-using, granting secret permission for whole cluster, etc). So in this case when a user has acm-vm-extended:view role binding, the mounting of config map/secret/service account does not show the configmaps/serviceaccounts that the user does have rbac access too.
Example user permissions:
mjs@60f1a55cb144:/UbuntuSync$ for resource in secrets configmaps serviceaccounts; do echo $resource; kubectl auth can-i list $resource -n analytics-jobs --as=qe-view-user; echo; done secrets no configmaps yes serviceaccounts yes
Version-Release number of selected component (if applicable):
ACM 2.16 + CNV 4.21 nightly build
How reproducible:
always
Steps to Reproduce:
1. assign IDP VM permissions 2. assign IDP user read permissions for configmaps + serviceaccounts but not secrets 3. try to create environment disk in UI
Actual results:
User cannot create a disk from configmap or serviceaccount which they have access to read
Expected results:
User should be able to create disks from either configmapd, serviceaccounts, or secrets depending on their rbac permissions. They should not need permissions to all 3 for the list to populate.
Additional info:
- is related to
-
ACM-27287 kubevirt.io-acm-managed:admin role is missing 'get' for 'secret'
-
- In Progress
-