-
Bug
-
Resolution: Done-Errata
-
None
-
Quality / Stability / Reliability
-
False
-
-
False
-
RELEASE_PENDING
-
-
-
No
Description of problem:
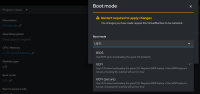
In Virtual Machine -> Details -> Boot Mode, there are these options:
1. BIOS
2. UEFI
3. UEFI (Secure)
Note [2] sets the VM as:
firmware:
bootloader:
efi: {}
But results in SecureBoot
/usr/libexec/qemu-kvm -name guest=openshift-cnv_fedora-y130ab1457eie7uw,debug-threads=on -S -object
{"qom-type":"secret","id":"masterKey0","format":"raw","file":"/var/run/kubevirt-private/libvirt/qemu/lib/domain-1-openshift-cnv_fedora/master-key.aes"}-blockdev
{"driver":"file","filename":"/usr/share/OVMF/OVMF_CODE.secboot.fd","node-name":"libvirt-pflash0-storage","auto-read-only":true,"discard":"unmap"}And [3] sets the VM as:
firmware:
bootloader:
efi:
secureBoot: true
Which is the same, also SecureBoot enabled:
/usr/libexec/qemu-kvm -name guest=openshift-cnv_fedora-y130ab1457eie7uw,debug-threads=on -S -object
{"qom-type":"secret","id":"masterKey0","format":"raw","file":"/var/run/kubevirt-private/libvirt/qemu/lib/domain-1-openshift-cnv_fedora/master-key.aes"}-blockdev
{"driver":"file","filename":"/usr/share/OVMF/OVMF_CODE.secboot.fd","node-name":"libvirt-pflash0-storage","auto-read-only":true,"discard":"unmap"}This means it is always enabling SecureBoot, even if the user sets is to option [2] in the UI.
According to https://kubevirt.io/user-guide/virtual_machines/virtual_hardware/#biosuefi
~~~
Enabling EFI automatically enables Secure Boot, unless the secureBoot field under efi is set to false.
~~~
Its a bit odd, as SecureBoot is usually opt-in and not opt-out, maybe the UI also expected that.
But because the default is enabled, the UI should:
For option [2]
firmware:
bootloader:
efi:
secureBoot: false
For option [3]
firmware:
bootloader:
efi:
secureBoot: true
OR
firmware:
bootloader:
efi: {}
Version-Release number of selected component (if applicable):
OCP 4.12.8
CNV 4.12.1
How reproducible:
Always
Steps to Reproduce:
1. Set VM to UEFI (not Secure)
2. Boot it
3. Check SecureBoot is enabled
- blocks
-
CNV-28538 [2193004] SecureBoot is always enabled for UEFI VMs
-
- Closed
-
- external trackers
- links to