-
Bug
-
Resolution: Done
-
Normal
-
None
-
None
-
Quality / Stability / Reliability
-
2
-
False
-
-
False
-
-
-
CMP Sprint 105, CMP Sprint 106, CMP Sprint 107
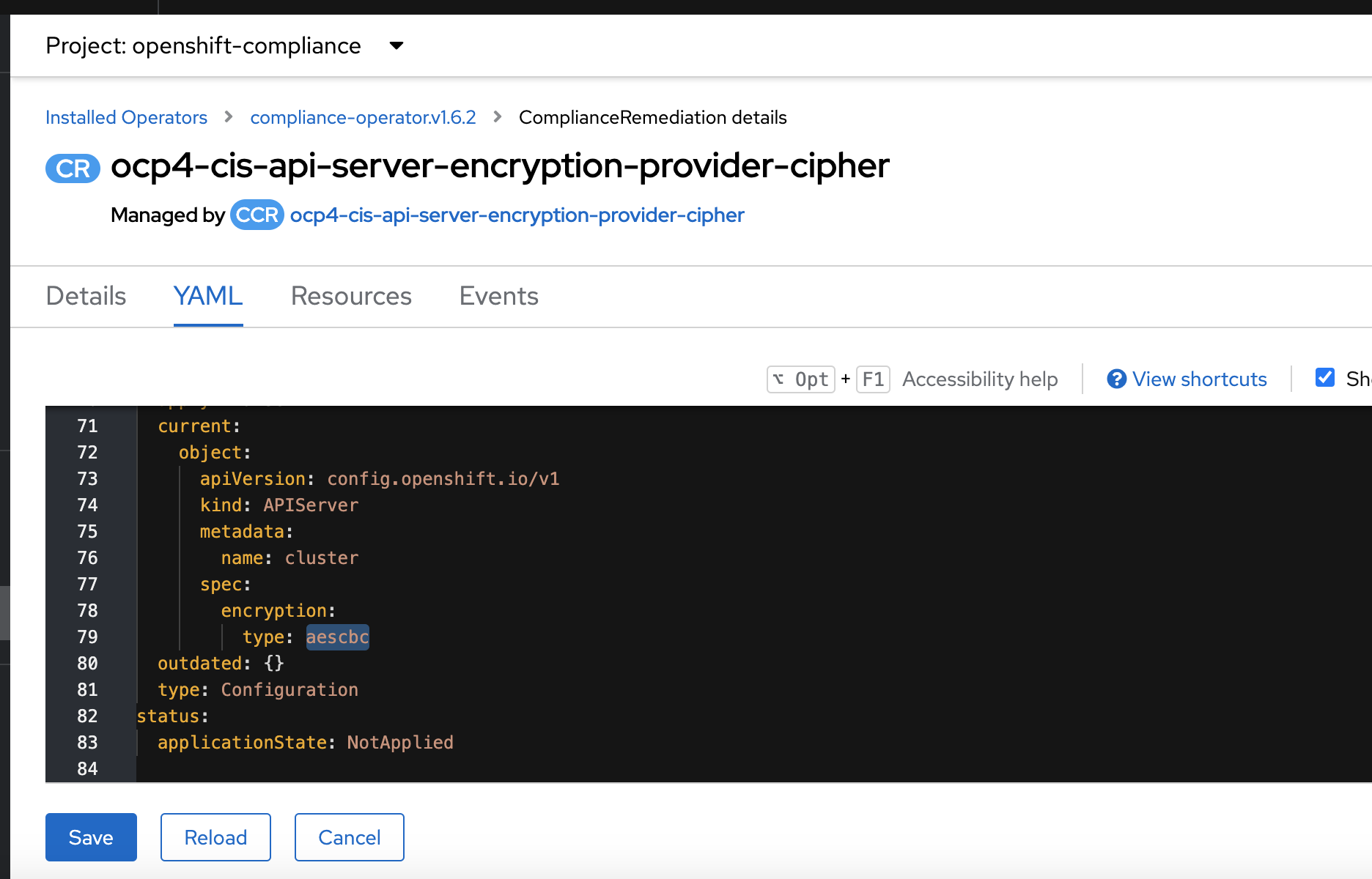
Current ComplianceRemediation object: ocp4-cis-api-server-encryption-provider-cipher
enforces aescbc encryption.
However, for several releases already, API server supports also AES-GCM, which is stronger and it is the default in vanilla kubernetes as well.
While the text of rule description is updated
the part below it's notWhen you enable etcd encryption, encryption keys are created. These keys are rotated on a weekly basis. You must have these keys in order to restore from an etcd backup.
To ensure the correct cipher, set the encryption type to aescbc or aesgcm in the apiserver object which configures the API server itself.
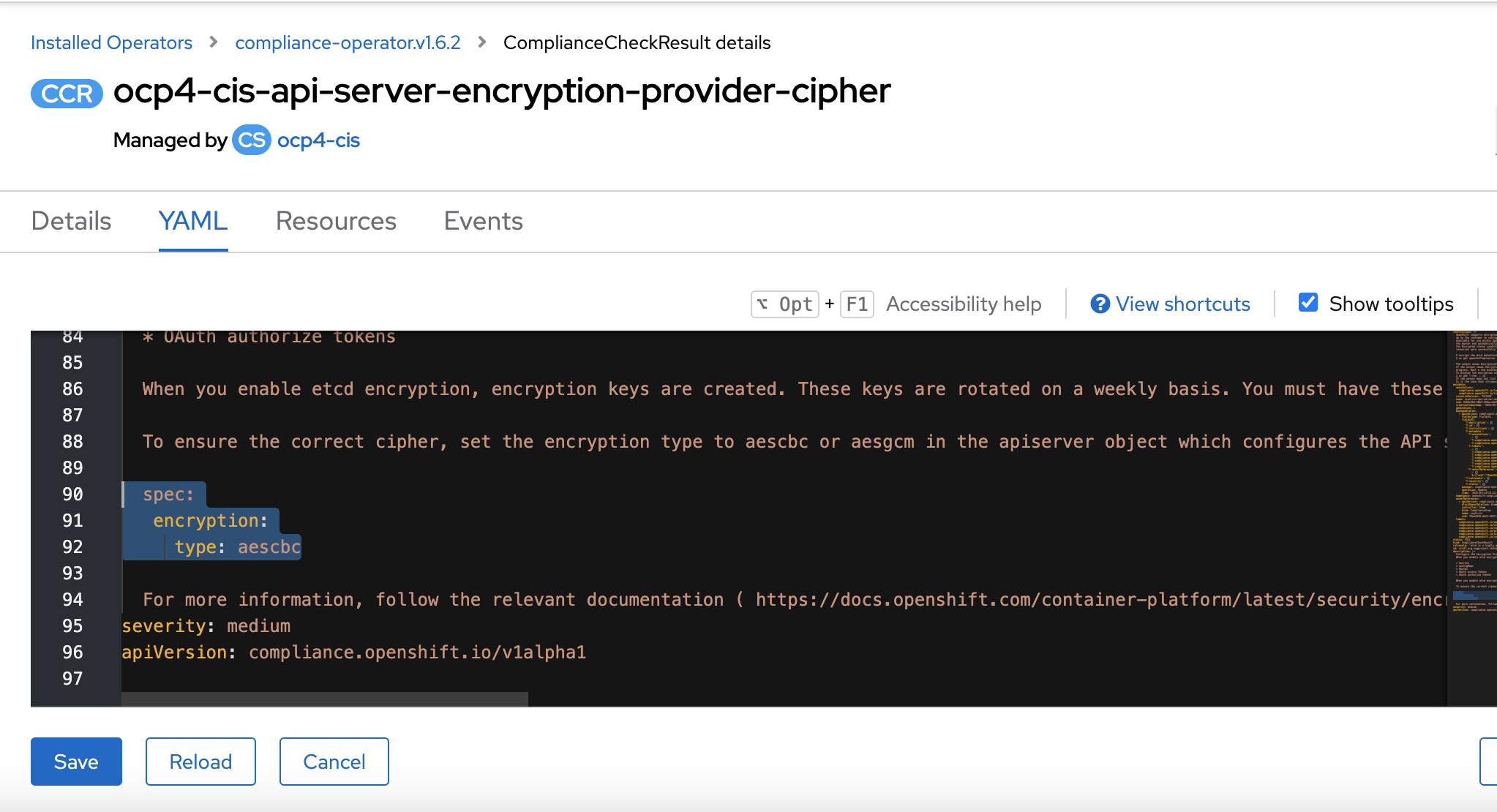
In addition, the remediation also needs to be changed to enforce by default AES-GCM instead of AES-CBC