-
Bug
-
Resolution: Not a Bug
-
Undefined
-
None
-
None
-
None
-
False
-
-
False
Ref: https://github.ibm.com/PrivateCloud-analytics/CPD-Quality/issues/44029
Problem Description:
There is non compliance found in cert-manager Operator for Red Hat OpenShift.
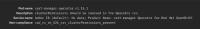
cpd_nc_sh_026_csv_clusterPermissions_present
CSV: cert-manager-operator.v1.15.1 - we are using this in CPD.
ClusterPermissions give operators cluster-wide access, which violates CPD’s requirement for namespace-scoped RBAC.
This poses a security risk by enabling potential privilege escalation for tenant admins through service account tokens. So, we need the clusterpermissions removed from CSV's.
CSV info:
apiVersion: operators.coreos.com/v1alpha1
kind: ClusterServiceVersion
metadata:
annotations:
alm-examples: |-
[
{
"apiVersion": "acme.cert-manager.io/v1",
"kind": "Challenge",
"metadata": {
"name": "tls-cert-sample",
"namespace": "default"
},
"spec": {
"authorizationURL": "https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/XXXXX",
"dnsName": "sample.dns.name",
"issuerRef": {
"kind": "Issuer",
"name": "letsencrypt-staging"
},
"key": "XXX",
"solver": {
"dns01": {
"route53": {
"accessKeyID": "XXX",
"hostedZoneID": "XXX",
"region": "us-east-1",
"secretAccessKeySecretRef": {
"key": "awsSecretAccessKey",
"name": "aws-secret"
}
}
},
"selector": {
"dnsNames": [
"sample.dns.name"
]
}
},
"token": "XXX",
"type": "DNS-01",
"url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/XXXXXX/XXXXX",
"wildcard": false
}
},
{
"apiVersion": "acme.cert-manager.io/v1",
"kind": "Order",
"metadata": {
"annotations": {
"cert-manager.io/certificate-name": "tls-cert",
"cert-manager.io/certificate-revision": "1",
"cert-manager.io/private-key-secret-name": "tls-cert-sample"
},
"name": "tls-cert-sample",
"namespace": "default"
},
"spec": {
"commonName": "sample.dns.name",
"dnsNames": [
"sample.dns.name"
],
"issuerRef": {
"kind": "Issuer",
"name": "letsencrypt-staging"
},
"request": "XXX"
}
},
{
"apiVersion": "cert-manager.io/v1",
"kind": "Certificate",
"metadata": {
"name": "selfsigned-ca",
"namespace": "default"
},
"spec": {
"commonName": "selfsigned-ca.dns.name",
"isCA": true,
"issuerRef": {
"group": "cert-manager.io",
"kind": "ClusterIssuer",
"name": "selfsigned-issuer"
},
"privateKey": {
"algorithm": "ECDSA",
"size": 256
},
"secretName": "ca-root-secret"
}
},
{
"apiVersion": "cert-manager.io/v1",
"kind": "Certificate",
"metadata": {
"name": "tls-cert",
"namespace": "default"
},
"spec": {
"commonName": "sample.dns.name",
"dnsNames": [
"sample.dns.name"
],
"isCA": false,
"issuerRef": {
"kind": "Issuer",
"name": "letsencrypt-staging"
},
"secretName": "tls-cert"
}
},
{
"apiVersion": "cert-manager.io/v1",
"kind": "CertificateRequest",
"metadata": {
"annotations": {
"cert-manager.io/certificate-name": "tls-cert",
"cert-manager.io/certificate-revision": "1",
"cert-manager.io/private-key-secret-name": "tls-cert-sample"
},
"name": "tls-cert-sample",
"namespace": "default"
},
"spec": {
"groups": [
"system:serviceaccounts",
"system:serviceaccounts:cert-manager",
"system:authenticated"
],
"issuerRef": {
"kind": "Issuer",
"name": "letsencrypt-staging"
},
"request": "XXX",
"username": "system:serviceaccount:cert-manager:cert-manager"
}
},
{
"apiVersion": "cert-manager.io/v1",
"kind": "ClusterIssuer",
"metadata": {
"name": "selfsigned-issuer"
},
"spec": {
"selfSigned": {}
}
},
{
"apiVersion": "cert-manager.io/v1",
"kind": "Issuer",
"metadata": {
"name": "ca-issuer",
"namespace": "default"
},
"spec": {
"ca": {
"secretName": "ca-root-secret"
}
}
},
{
"apiVersion": "cert-manager.io/v1",
"kind": "Issuer",
"metadata": {
"name": "letsencrypt-staging",
"namespace": "default"
},
"spec": {
"acme": {
"email": "aos-ci-cd@redhat.com",
"privateKeySecretRef": {
"name": "letsencrypt-staging"
},
"server": "https://acme-staging-v02.api.letsencrypt.org/directory",
"solvers": [
{
"dns01": {
"route53": {
"accessKeyID": "ACCESS_KEY_ID",
"hostedZoneID": "HOSTED_ZONE_ID",
"region": "AWS_REGION",
"secretAccessKeySecretRef": {
"key": "access-key",
"name": "sample-aws-secret"
}
}
},
"selector": {
"dnsNames": [
"sample.dns.name"
]
}
}
]
}
}
},
{
"apiVersion": "operator.openshift.io/v1alpha1",
"kind": "CertManager",
"metadata": {
"name": "cluster"
},
"spec": {
"logLevel": "Normal",
"managementState": "Managed"
}
},
{
"apiVersion": "operator.openshift.io/v1alpha1",
"kind": "IstioCSR",
"metadata": {
"annotations": {
"kubernetes.io/description": "Creating this resource requires the istio-csr tech-preview feature to be enabled, which otherwise has no effect. Please refer to the cert-manager documentation for more information on enabling the istio-csr feature. Technology Preview features are not supported with Red Hat production service level agreements (SLAs) and might not be functionally complete. Red Hat does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process"
},
"name": "default",
"namespace": "istio-csr"
},
"spec": {
"istioCSRConfig": {
"certManager": {
"issuerRef": {
"group": "cert-manager.io",
"kind": "Issuer",
"name": "istio-csr-issuer"
}
},
"istio": {
"namespace": "istio-system"
},
"istiodTLSConfig": {
"trustDomain": "cluster.local"
}
}
}
}
]
capabilities: Seamless Upgrades
categories: Security
console.openshift.io/disable-operand-delete: "true"
containerImage: registry.redhat.io/cert-manager/cert-manager-operator-rhel9@sha256:f328263e2d29e34ede65e4501f0447b2d9f84e9445a365c2fa2fbb253939e274
createdAt: 2025-03-13T18:26:37
features.operators.openshift.io/cnf: "false"
features.operators.openshift.io/cni: "false"
features.operators.openshift.io/csi: "false"
features.operators.openshift.io/disconnected: "false"
features.operators.openshift.io/fips-compliant: "true"
features.operators.openshift.io/proxy-aware: "true"
features.operators.openshift.io/tls-profiles: "false"
features.operators.openshift.io/token-auth-aws: "true"
features.operators.openshift.io/token-auth-azure: "true"
features.operators.openshift.io/token-auth-gcp: "true"
olm.operatorGroup: openshift-cert-manager-operator
olm.operatorNamespace: cert-manager-operator
olm.skipRange: '>=1.15.0 <1.15.1'
operator.openshift.io/uninstall-message: The cert-manager Operator for Red Hat
OpenShift will be removed from cert-manager-operator namespace. If your Operator
configured any off-cluster resources, these will continue to run and require
manual cleanup. All operands created by the operator will need to be manually
cleaned up. Please refer to https://docs.openshift.com/container-platform/latest/security/cert_manager_operator/cert-manager-operator-uninstall.html
for additional steps.
operatorframework.io/cluster-monitoring: "true"
operatorframework.io/properties: '{"properties":[{"type":"olm.gvk","value":{"group":"acme.cert-manager.io","kind":"Challenge","version":"v1"}},{"type":"olm.gvk","value":{"group":"acme.cert-manager.io","kind":"Order","version":"v1"}},{"type":"olm.gvk","value":{"group":"cert-manager.io","kind":"Certificate","version":"v1"}},{"type":"olm.gvk","value":{"group":"cert-manager.io","kind":"CertificateRequest","version":"v1"}},{"type":"olm.gvk","value":{"group":"cert-manager.io","kind":"ClusterIssuer","version":"v1"}},{"type":"olm.gvk","value":{"group":"cert-manager.io","kind":"Issuer","version":"v1"}},{"type":"olm.gvk","value":{"group":"operator.openshift.io","kind":"CertManager","version":"v1alpha1"}},{"type":"olm.gvk","value":{"group":"operator.openshift.io","kind":"IstioCSR","version":"v1alpha1"}},{"type":"olm.package","value":{"packageName":"openshift-cert-manager-operator","version":"1.15.1"}}]}'
operatorframework.io/suggested-namespace: cert-manager-operator
operators.openshift.io/infrastructure-features: '["proxy-aware"]'
operators.openshift.io/valid-subscription: '["OpenShift Kubernetes Engine", "OpenShift
Container Platform", "OpenShift Platform Plus"]'
operators.operatorframework.io/builder: operator-sdk-v1.25.1
operators.operatorframework.io/project_layout: go.kubebuilder.io/v3
repository: https://github.com/openshift/cert-manager-operator
support: Red Hat, Inc.
creationTimestamp: "2025-04-06T22:10:47Z"
generation: 1
labels:
olm.copiedFrom: cert-manager-operator
olm.managed: "true"
operatorframework.io/arch.amd64: supported
operatorframework.io/arch.arm64: supported
operatorframework.io/arch.ppc64le: supported
operatorframework.io/arch.s390x: supported
operatorframework.io/os.linux: supported
name: cert-manager-operator.v1.15.1
namespace: cpd-ops
resourceVersion: "86876"
uid: 8eba92b9-fad3-46b0-87e6-d80e8f0019d6
spec:
apiservicedefinitions: {}
cleanup:
enabled: false
customresourcedefinitions:
owned:
- kind: CertificateRequest
name: certificaterequests.cert-manager.io
version: v1
- kind: Certificate
name: certificates.cert-manager.io
version: v1
- description: CertManager is the Schema for the certmanagers API
displayName: CertManager
kind: CertManager
name: certmanagers.operator.openshift.io
version: v1alpha1
- kind: Challenge
name: challenges.acme.cert-manager.io
version: v1
- kind: ClusterIssuer
name: clusterissuers.cert-manager.io
version: v1
- kind: Issuer
name: issuers.cert-manager.io
version: v1
- kind: IstioCSR
name: istiocsrs.operator.openshift.io
version: v1alpha1
- kind: Order
name: orders.acme.cert-manager.io
version: v1
description: |
The cert-manager Operator for Red Hat OpenShift provides seamless support for [cert-manager v1.15.5](https://github.com/cert-manager/cert-manager/tree/v1.15.2), which automates certificate management.
For more information, see the [cert-manager Operator for Red Hat OpenShift documentation](https://docs.openshift.com/container-platform/latest/security/cert_manager_operator/index.html).
displayName: cert-manager Operator for Red Hat OpenShift
icon:
- base64data: iVBORw0KGgoAAAANSUhEUgAAAVQAAAC1CAYAAAAA/QcmAAARRElEQVR4nO3dTWgjaWLG8cfuj2n3eKbkpqGHkNmqueSwJJH6kLlkEtVcwkII1pLLHhYkJ7AJ5OC6DCQnqZlDAlmwOqfksLgMCSTsBMuBXSZLQGXYHLJM4nKyl82lS9tZyGZMS/J0tz1utyuHXgvbbX2/Ukny/weCGUuqel1tPXq/ay6O41gAgKHNJ10AAJgVBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgAoAhBCoAGEKgYqxehqFOoqiv13/huqrPzak+N6cvXFfPPU/HQTCyMgKDmovjOE66EJhtcaOhg1JJR76vuNmUJM1Zlm4WCrrleZp3nEvfdxqmp++5aM6ydCOX081cTjdyuVEVH+gZgYqR289k9HJ3t+3zN/N53fI8XctkWj/7slzWQanUNkwvmrdt3cjlOgY0MGoEKkbqoFTS4YMHPb123rY17zg6iSKd1GoDn/N6Nqs3CgXdLBQGPgYwCAIVI3MSRWq+915i55+37Va3wlwqlVg5cHUwKIWR+dL3Ez3/Sa2mwwcP1HScV90HjUai5cHso4aKkWk6zlBNd9PmLEtveJ4WSqWki4IZRaBiJF6Gofbv30+6GJeat20tVirnBsEAE2jyYyQOy+Wki9DWSa2m/fv3dZRwlwRmDzVUjEQjlep5ylOS3qpWdd11ky4GZgQ1VBj3olKZijCVpGdMrYJBBCqMO6pUki5Cz05qNb0Mw6SLgRlBoMK4F1MUqNJ0fQFgshGoMOrsev1pwUYrMIVAhVHTWNujyQ9TGOWHMXGjocbSUtLFGMjbOzvMS8XQqKHCmGnrOz2LZj9MIFBhzLPvfjfpIgzsmGY/DKDJDyOiKNLtr35VNw4Oki7KQOZtW1YfdxIALkMNFUb4vq+DmzeTLsbATmq1vm7NAlyGQIURvu/r46OjpIsxFEb7MSwCFQM7iSIdB4H+ZW1NtVpN3zk40E/u3k26WAN7wcAUhnQ96QJg8r0MQx0HgY5/ccfS4+3tc88fvvtu67+/trenf71zR7/05Mm4izk0RvoxLAalcKmXYajDcrmnjU4+WljQd84MRlnS1IbqEh8HDIEmP845iSJ94bqv9gvd2OhpGelPLozsNyX95pMnemxZIyrl6FBLxTAIVLS8qFS0n8m81qQfRFNSutnUD+7cGb5gY0Q/KoZBoELSq5rZ069/faCNTX67w3LTbzx5om/dvq2jW7eGKd7YPPv006SLgClGoELScBstf/PatY7Pf/L8ud4/PNSPpmAGwOd7e0kXAVOMQIWOfH+ou5O+s7enD7q85qd6NQPgW7dva3+C+1bv/OxnCpmPigERqDCy5d7fWpZ6iclPnj9XutnU31iWXiwsDH1e0/7v3j0F9KNiQAQqjKwQervZ1D/02KRvSvqzZlO/cnAwccH6b8+e6cff/77iRiPpomAKEagYqrl/1vt7e/r7Pkb1zwbrRwsLarz1lpFyDOr49m19vLene599pqbj6KBUIljRFyb2Q/W5OaPH+8GdO/rGgJP6P5Dk3bun39rfH/vOVacLFD6Q9E+/+NmcZel2uayb3B0VPSBQoS9c18jc07OGCdVTvyvpj999V7/x+ee6eXhopmCX2LcsfbPZ1A/P/Oxiya9ns3rT9zXvOCMrB6YfTX6M5NYfv/PkiX58546+MsQxvifp9x4/1juHh8pK+vbSkv7jnXeMzRL437t39dHCgpwLYSpJe/funfv/4+1t7WcyU31XAoweNVToZRhq//79kRz7xcKC/mRuTp88f2782B9I+oqkD2xbbx4f69clXbvefr+f2smJHs/P63u1mn6oV3247fynbeuX2/Qtv7m+ThcALkWgQtJomv1n/ejuXX1rb08/HdkZzOrWWUGo4jI0+SFJWiiVRnr89/f29Nnt2/rzHuerJqnbIgVJerayoiPfH3VRMGWooaLlaS6nF1tbIz/PvmXp46Ojc1v+TZJP797V+z0uQeX20ziLQEVL3GhoP5MxNi+1m6dLS/q7kxP9RbPZsT9znP5wYUF/2UfQc3M/nEWTHy1zqZQWKxXNjWmt/WK9rj9qNvXfCwv65N49/dpYztpev2EqvVoUcTDi7hJMD2qoeM2R7+vZykoi5366tKR/vnZNf7W3p/8a0zktSd++e1e/P+BOU3OWpRQrqiACFW0kGaqnni4taXdxUX/9+HHXaU6DsCT9qWXpD46Ohl6Vxag/JAIVHRz5vp573kCbTo/C06UlRYuL+vejI/3jz3+uptR3LfYDvdoQ+2uLi/rVx4+Nle1mPq83GfW/8ghUdPQyDPWF605MqLbzP7bd8fnU/r4W6/WRnf9aOq232Uf1yiNQ0dVJFOlpLqeXu7tJF2WiccdUMMqPruYdR28FgW7m80kXBZhoBCp6MpdK6U3f1+Lm5timVU0TrgkkAhV9upHLyYoi3VheTrooE4XVUpAIVAzgdAHA4uam5rsMBl0VBCokAhVDuJHL6e0w1K1i8co3eW+4btJFwARglB9GnESRDkolHW1sJF2UsWOlFE5RQ4UR846jN31f1qNHV242wBuel3QRMCGooWIkrkqNdd629XYYai6VSroomAAEKkbqJIr0pe/ry3J54ldbDYL9UHEWgYqxOfJ9HZbLM7Piig1RcBGBirE7iSIdlst6UamMbTNr0whTXIZARaJeVCo6qlT0olKZii6BedvWYqVCMx+XIlAxMV6Gob70fR0HwcR1C8xZlt7wvJHfzBDTjUDFRDqJIh0HgV4EgY6DILGugXnb1s1CQbc8j5F8dEWgYiqcRJFehqGOw/BVDTYMR9ZFcC2d1nXX1RuFAk179IVAxVQ7DoJXYRtFihsNvTyzyfPx9nbb911Lp1s1zuuuq/lUStcyGV1nCSmGQKACgCEsPQUAQwhUADCEQAUAQwhUADCEQAUAQwhUADCEQAUAQwhUADCEQAUAQwhUADDketIFAM4Kw/DcIwiCpIsE9IxAHSFTYeA4jhzHMXKsSRNFkXzfVxAECsNQzQF3kIqiSFEUtX1+kGsYhqEaHW4PnclklJrALf3CMJTjOBNZtpkXY2QkGXtYlhUvLy/Hm5ubSf9aRhWLxY6/t6njFIvFvsuWzWY7HrNarfZ9TNPq9Xq8ubkZF4vFOJvNxpZlTUzZriJqqFOi2Wxqa2tLW1tbSqfT8n1fGfbqvLLCMFQul1NtSu/JNasYlJpCu7u7un//vnzfT7ooSEij0SBMJxCBOsVWVlYIVWCCEKhTzvO8joMxAMaHQJ1yzWZTJe7ECUwEBqUSVCwW2z7XaDRaczG7TSXa2NhQuVxmmgyQMAI1Qb3ULBuNhgqFgra2tjq+rlKpqFAodDxOpVJpzffcPXPf+3Q6LcdxlMvllMvljATz2XNd5LqucrnczM9SOF2YEIahoii69Msxm80qk8m0rkk7F/9WunXznM7t7eVYMCjpeVuzTF3mlvaqXq/Htm0PNM+yXq/HxWKxNT+x28OyrLhYLMb1er3v37ffc9m23XWuZ68mZR7qzs5OnM/nu/57tbse6+vrl5al32OZuKboH1d3hEz+Ya+urvYdGDs7O3E6nR7oQ2fbdryzs9Nz+XZ2dgYKEVPXKOlArVarxn7/fD7/WlkI1OnAoNSU6LcZHoahXNc917TvR61Wk+u6lzbZL/J9X/fv37/y8yJN/f4bGxsdu28wuehDnRL9zDc9DdNB18WfajabrVBttw4+CAKtrKwMdZ5xiKKo770VOq3jv8h1XWWzWW1vb/dZssudhqrrukaOhzFJuoo8y2So6ZXP57se6+wa/0Gb+e0e2Wz20nLV6/We+0sHffSqW5N/FI+LfajVatXo8ZeXl3v+WxrFNUX/qKEmqNto62mtqltT0rKs1ghxqVTq2szP5/NyXVeO47R2e+pUs9re3lalUnltFNrzvJ5qwbZtnzvfxVkGs6JdLfV0JN9xHGUyGQVBoCiKtLGx0fF4Z2d2ZLPZc881Go2O1zCdTjONLglJJ/os05hqSmcHXDrVGC3LarsL0fr6esdzXKylPnr0qGu5bNtue75qtdp10KefP89JqKHGcRxvbm62rtf6+nrH2RI7Oztda/idrt8g78NoEagjNI4PtW3brQ/t6Ye53WNtba1jedfW1jq+/9GjRz2/Np1O9zT1qlv3RK8mJVDjOD53nbrp9kVGoE4XmvxTzLIsVSqVVtOuUql0fO1pc7OdTCYjy7LaNuODIGiNPnc6l/RqEK2XJucsNkv72ch6VjcOv6oI1Cll27Yqlcq51UadVs80m019+OGHQ53z7BSqTn2uy8vLM78KqpsoilSpVFqrpC7DCP7sIVCnjGVZ8jxPnue9VrvrZc7oMHo9/lUOijAM5XleT9OnTE2xwuQgUKdMs9lUoVC4tKk87LxTUyaxdprP5/ueLO95Xl+zEXzfn4o5uRgdAjVBcRy/9rNGoyHHcTqGY6lUunSif6f+z3E6XVgwSRzH6btM/fTvVioVwhTshzppUqmUPM/r+JqNjY1LB5cmpWZ4FW/93O3fDFcDgTqBPM+TZVkdX3PZooBugfro0SPFr6bKDfQ4G5QXJ5qftbW1NfL+3EkShmHHxRf5fF7ValX1el1xHGtnZ0fValVra2uybXuMJcWoEagTqJda6vb29ms1wW5N2lwu19P69F5eM85zTbpOXx7FYlG+78t13VYXwun+p57njWza1Cxc12lEoE6oXmqpFwdZcrlcxxrP7u6uXNdtO42n0Wi0PuTdapjdBnhqtZocx2m7qUsQBMpkMjOxBLXTdLWkumG4eWMyCNQJ1UsttVarvfbB6fae3d1dvffee8rlciqXywqCQOVyWYVCQY7j6OHDh61dpjp9KB3HUT6f73iuZrOplZUVpVKpVo0sl8vJcRx9+OGHMxGmUufJ+aVSqW1tMYqikd1gcWtrS47jyPM8lUoleZ4n13UnbrBw5ox9bdYVoi5LF3vRbdNiy7JeW+JpcrepdjvIx/F07TY1yg2md3Z2Or7Otu14dXU1LhaLcbFYjFdXV3v+N2q3hLRerw90PdvtHAYzqKFOuG47UjWbTZXL5XM/q1QqXbsLerWystK2eZ9KpWha6lWzPp1Ot32+Vqvp4cOHevDggR48eKCHDx8OXTtPpVIdBwaRDAJ1whUKha4jweVy+Vyz0nEcBUFgLFQrlUrbpmkul9P6+rqR80yzi19q48DN9iYPgToFeqmlXuw7zWQyiqJo6FpMNptVFEUd+wkLhYKq1aqxAJ9GruuO/YvFdV2trq6O9ZzojECdAr3UUjc2Nl6rRaZSKQVBoPX19b7nO6bTaVWrVQVB0NOKodPZA8VisedgXV1dnalAKBQK2tzc7PlaW5al5eXloc5ZLpe1trZ2pb/MJslcHF+y/hFGdKtZ9tNkC4Kg6wqkbqO4YRjK932FYfjaPeJt224tz8zlckNN92k0Gq2dli5Ovzp7jtPA7/R79XqNuh1nkBFu3/c7jsKfzoxo994gCF67O0E2mz13DRqNRsd+6E7nOKvTNZfUumOA67oTs6JuFhGoAGAITX4AMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBDCFQAMIRABQBD/h+fh1Gb7+ZNngAAAABJRU5ErkJggg==
mediatype: image/png
install:
spec:
clusterPermissions:
- rules:
- apiGroups:
- ""
resources:
- configmaps
- events
- namespaces
- serviceaccounts
- services
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- ""
resources:
- pods
- secrets
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- acme.cert-manager.io
resources:
- challenges
- challenges/finalizers
- challenges/status
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- acme.cert-manager.io
resources:
- challenges
- challenges/finalizers
- challenges/status
- orders
- orders/finalizers
- orders/status
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- admissionregistration.k8s.io
resources:
- mutatingwebhookconfigurations
- validatingwebhookconfigurations
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- apiextensions.k8s.io
resources:
- customresourcedefinitions
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- apiregistration.k8s.io
resources:
- apiservices
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- apps
resources:
- deployments
- replicasets
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- cert-manager.io
resources:
- certificaterequests
- certificaterequests/finalizers
- certificaterequests/status
- certificates
- certificates/finalizers
- certificates/status
- clusterissuers
- clusterissuers/status
- issuers
- issuers/status
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- cert-manager.io
resourceNames:
- clusterissuers.cert-manager.io/*
- issuers.cert-manager.io/*
resources:
- signers
verbs:
- approve
- apiGroups:
- certificates.k8s.io
resources:
- certificatesigningrequests
- certificatesigningrequests/status
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- certificates.k8s.io
resources:
- signers
verbs:
- create
- delete
- get
- list
- patch
- sign
- update
- watch
- apiGroups:
- config.openshift.io
resources:
- certmanagers
- clusteroperators
- clusteroperators/status
- infrastructures
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- gateway.networking.k8s.io
resources:
- gateways
- gateways/finalizers
- httproutes
- httproutes/finalizers
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
- ingresses/finalizers
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- operator.openshift.io
resources:
- certmanagers
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- operator.openshift.io
resources:
- certmanagers/finalizers
verbs:
- update
- apiGroups:
- operator.openshift.io
resources:
- certmanagers/status
verbs:
- get
- patch
- update
- apiGroups:
- operator.openshift.io
resources:
- istiocsrs
verbs:
- get
- list
- patch
- update
- watch
- apiGroups:
- operator.openshift.io
resources:
- istiocsrs/finalizers
verbs:
- update
- apiGroups:
- operator.openshift.io
resources:
- istiocsrs/status
verbs:
- get
- patch
- update
- apiGroups:
- rbac.authorization.k8s.io
resources:
- clusterrolebindings
- clusterroles
- rolebindings
- roles
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- route.openshift.io
resources:
- routes
- routes/custom-host
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- authentication.k8s.io
resources:
- tokenreviews
verbs:
- create
- apiGroups:
- authorization.k8s.io
resources:
- subjectaccessreviews
verbs:
- create
serviceAccountName: cert-manager-operator-controller-manager
deployments:
- label:
app.kubernetes.io/component: manager
app.kubernetes.io/created-by: cert-manager-operator
app.kubernetes.io/instance: controller-manager
app.kubernetes.io/managed-by: kustomize
app.kubernetes.io/name: deployment
app.kubernetes.io/part-of: cert-manager-operator
name: cert-manager-operator-controller-manager
spec:
replicas: 1
selector:
matchLabels:
name: cert-manager-operator
strategy: {}
template:
metadata:
annotations:
kubectl.kubernetes.io/default-container: cert-manager-operator
creationTimestamp: null
labels:
name: cert-manager-operator
spec:
affinity:
nodeAffinity:
requiredDuringSchedulingIgnoredDuringExecution:
nodeSelectorTerms:
- matchExpressions:
- key: kubernetes.io/arch
operator: In
values:
- amd64
- arm64
- ppc64le
- s390x
- key: kubernetes.io/os
operator: In
values:
- linux
containers:
- args:
- start
- --v=$(OPERATOR_LOG_LEVEL)
- --trusted-ca-configmap=$(TRUSTED_CA_CONFIGMAP_NAME)
- --cloud-credentials-secret=$(CLOUD_CREDENTIALS_SECRET_NAME)
- --unsupported-addon-features=$(UNSUPPORTED_ADDON_FEATURES)
command:
- /usr/bin/cert-manager-operator
env:
- name: WATCH_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.annotations['olm.targetNamespaces']
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: OPERATOR_NAME
value: cert-manager-operator
- name: RELATED_IMAGE_CERT_MANAGER_WEBHOOK
value: registry.redhat.io/cert-manager/jetstack-cert-manager-rhel9@sha256:6af3ee8b2a5a87042fb7158bda8d6cf2e6324d1e265974acf77214d4cd0ea0d3
- name: RELATED_IMAGE_CERT_MANAGER_CA_INJECTOR
value: registry.redhat.io/cert-manager/jetstack-cert-manager-rhel9@sha256:6af3ee8b2a5a87042fb7158bda8d6cf2e6324d1e265974acf77214d4cd0ea0d3
- name: RELATED_IMAGE_CERT_MANAGER_CONTROLLER
value: registry.redhat.io/cert-manager/jetstack-cert-manager-rhel9@sha256:6af3ee8b2a5a87042fb7158bda8d6cf2e6324d1e265974acf77214d4cd0ea0d3
- name: RELATED_IMAGE_CERT_MANAGER_ACMESOLVER
value: registry.redhat.io/cert-manager/jetstack-cert-manager-acmesolver-rhel9@sha256:20efff60a0caf5eafb38986fd21611697b5bc534c2e789da233983a9739938ed
- name: RELATED_IMAGE_CERT_MANAGER_ISTIOCSR
value: registry.redhat.io/cert-manager/cert-manager-istio-csr-rhel9@sha256:9573d74bd2b926ec94af76f813e6358f14c5b2f4e0eedab7c1ff1070b7279a5c
- name: OPERAND_IMAGE_VERSION
value: 1.15.5
- name: ISTIOCSR_OPERAND_IMAGE_VERSION
value: 0.14.0
- name: OPERATOR_IMAGE_VERSION
value: 1.15.1
- name: OPERATOR_LOG_LEVEL
value: "2"
- name: TRUSTED_CA_CONFIGMAP_NAME
- name: CLOUD_CREDENTIALS_SECRET_NAME
- name: UNSUPPORTED_ADDON_FEATURES
image: registry.redhat.io/cert-manager/cert-manager-operator-rhel9@sha256:f328263e2d29e34ede65e4501f0447b2d9f84e9445a365c2fa2fbb253939e274
imagePullPolicy: IfNotPresent
name: cert-manager-operator
ports:
- containerPort: 8443
name: https
protocol: TCP
resources:
requests:
cpu: 10m
memory: 32Mi
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop:
- ALL
privileged: false
runAsNonRoot: true
seccompProfile:
type: RuntimeDefault
securityContext:
runAsNonRoot: true
seccompProfile:
type: RuntimeDefault
serviceAccountName: cert-manager-operator-controller-manager
terminationGracePeriodSeconds: 10
permissions:
- rules:
- apiGroups:
- ""
resources:
- configmaps
verbs:
- get
- list
- watch
- create
- update
- patch
- delete
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- get
- list
- watch
- create
- update
- patch
- delete
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
serviceAccountName: cert-manager-operator-controller-manager
strategy: deployment
installModes:
- supported: true
type: OwnNamespace
- supported: true
type: SingleNamespace
- supported: false
type: MultiNamespace
- supported: true
type: AllNamespaces
keywords:
- cert-manager
- cert-manager-operator
- cert
- certificates
- security
- TLS
links:
- name: Documentation
url: https://github.com/openshift/cert-manager-operator/blob/master/README.md
maintainers:
- email: support@redhat.com
name: Red Hat Support
maturity: stable
minKubeVersion: 1.25.0
provider:
name: Red Hat
relatedImages:
- image: registry.redhat.io/cert-manager/jetstack-cert-manager-rhel9@sha256:6af3ee8b2a5a87042fb7158bda8d6cf2e6324d1e265974acf77214d4cd0ea0d3
name: cert-manager-webhook
- image: registry.redhat.io/cert-manager/jetstack-cert-manager-rhel9@sha256:6af3ee8b2a5a87042fb7158bda8d6cf2e6324d1e265974acf77214d4cd0ea0d3
name: cert-manager-ca-injector
- image: registry.redhat.io/cert-manager/jetstack-cert-manager-rhel9@sha256:6af3ee8b2a5a87042fb7158bda8d6cf2e6324d1e265974acf77214d4cd0ea0d3
name: cert-manager-controller
- image: registry.redhat.io/cert-manager/jetstack-cert-manager-acmesolver-rhel9@sha256:20efff60a0caf5eafb38986fd21611697b5bc534c2e789da233983a9739938ed
name: cert-manager-acmesolver
- image: registry.redhat.io/cert-manager/cert-manager-istio-csr-rhel9@sha256:9573d74bd2b926ec94af76f813e6358f14c5b2f4e0eedab7c1ff1070b7279a5c
name: cert-manager-istiocsr
replaces: cert-manager-operator.v1.15.0
version: 1.15.1
status:
cleanup: {}
conditions:
- lastTransitionTime: "2025-04-06T22:10:41Z"
lastUpdateTime: "2025-04-06T22:10:41Z"
message: requirements not yet checked
phase: Pending
reason: RequirementsUnknown
- lastTransitionTime: "2025-04-06T22:10:41Z"
lastUpdateTime: "2025-04-06T22:10:41Z"
message: one or more requirements couldn't be found
phase: Pending
reason: RequirementsNotMet
- lastTransitionTime: "2025-04-06T22:10:43Z"
lastUpdateTime: "2025-04-06T22:10:43Z"
message: all requirements found, attempting install
phase: InstallReady
reason: AllRequirementsMet
- lastTransitionTime: "2025-04-06T22:10:43Z"
lastUpdateTime: "2025-04-06T22:10:43Z"
message: waiting for install components to report healthy
phase: Installing
reason: InstallSucceeded
- lastTransitionTime: "2025-04-06T22:10:43Z"
lastUpdateTime: "2025-04-06T22:10:43Z"
message: 'installing: waiting for deployment cert-manager-operator-controller-manager
to become ready: deployment "cert-manager-operator-controller-manager" not available:
Deployment does not have minimum availability.'
phase: Installing
reason: InstallWaiting
- lastTransitionTime: "2025-04-06T22:10:55Z"
lastUpdateTime: "2025-04-06T22:10:55Z"
message: install strategy completed with no errors
phase: Succeeded
reason: InstallSucceeded
lastTransitionTime: "2025-04-06T22:10:55Z"
lastUpdateTime: "2025-04-06T22:10:55Z"
message: The operator is running in cert-manager-operator but is managing this namespace
phase: Succeeded
reason: Copied
requirementStatus:
- group: operators.coreos.com
kind: ClusterServiceVersion
message: CSV minKubeVersion (1.25.0) less than server version (v1.31.5)
name: cert-manager-operator.v1.15.1
status: Present
version: v1alpha1
- group: apiextensions.k8s.io
kind: CustomResourceDefinition
message: CRD is present and Established condition is true
name: certificaterequests.cert-manager.io
status: Present
uuid: e6c090e0-e789-40fb-a6bc-1a18af0102c3
version: v1
- group: apiextensions.k8s.io
kind: CustomResourceDefinition
message: CRD is present and Established condition is true
name: certificates.cert-manager.io
status: Present
uuid: 84cf9fbd-1b30-42a7-ba6b-a90c4910bfab
version: v1
- group: apiextensions.k8s.io
kind: CustomResourceDefinition
message: CRD is present and Established condition is true
name: certmanagers.operator.openshift.io
status: Present
uuid: 74d29fe2-17aa-4974-b2ab-7d3b58a5221f
version: v1
- group: apiextensions.k8s.io
kind: CustomResourceDefinition
message: CRD is present and Established condition is true
name: challenges.acme.cert-manager.io
status: Present
uuid: 5d76cd3c-e1e7-4499-b4e7-f18e5495dd79
version: v1
- group: apiextensions.k8s.io
kind: CustomResourceDefinition
message: CRD is present and Established condition is true
name: clusterissuers.cert-manager.io
status: Present
uuid: d98e3865-b83d-455e-808f-85c304325fc1
version: v1
- group: apiextensions.k8s.io
kind: CustomResourceDefinition
message: CRD is present and Established condition is true
name: issuers.cert-manager.io
status: Present
uuid: 44d8db10-759f-4dd4-9b8e-351ebfa83c9c
version: v1
- group: apiextensions.k8s.io
kind: CustomResourceDefinition
message: CRD is present and Established condition is true
name: istiocsrs.operator.openshift.io
status: Present
uuid: 5d8f062b-fc85-450a-af48-4b536877c434
version: v1
- group: apiextensions.k8s.io
kind: CustomResourceDefinition
message: CRD is present and Established condition is true
name: orders.acme.cert-manager.io
status: Present
uuid: c3939a3d-cce0-45d9-acdc-b3c899d0ff60
version: v1
- dependents:
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":[""],"resources":["configmaps","events","namespaces","serviceaccounts","services"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":[""],"resources":["pods","secrets"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["acme.cert-manager.io"],"resources":["challenges","challenges/finalizers","challenges/status"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","deletecollection","get","list","patch","update","watch"],"apiGroups":["acme.cert-manager.io"],"resources":["challenges","challenges/finalizers","challenges/status","orders","orders/finalizers","orders/status"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["admissionregistration.k8s.io"],"resources":["mutatingwebhookconfigurations","validatingwebhookconfigurations"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["apiextensions.k8s.io"],"resources":["customresourcedefinitions"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["apiregistration.k8s.io"],"resources":["apiservices"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["apps"],"resources":["deployments","replicasets"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","deletecollection","get","list","patch","update","watch"],"apiGroups":["cert-manager.io"],"resources":["certificaterequests","certificaterequests/finalizers","certificaterequests/status","certificates","certificates/finalizers","certificates/status","clusterissuers","clusterissuers/status","issuers","issuers/status"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["approve"],"apiGroups":["cert-manager.io"],"resources":["signers"],"resourceNames":["clusterissuers.cert-manager.io/*","issuers.cert-manager.io/*"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["certificates.k8s.io"],"resources":["certificatesigningrequests","certificatesigningrequests/status"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","sign","update","watch"],"apiGroups":["certificates.k8s.io"],"resources":["signers"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["config.openshift.io"],"resources":["certmanagers","clusteroperators","clusteroperators/status","infrastructures"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["coordination.k8s.io"],"resources":["leases"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["gateway.networking.k8s.io"],"resources":["gateways","gateways/finalizers","httproutes","httproutes/finalizers"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["networking.k8s.io"],"resources":["ingresses","ingresses/finalizers"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["operator.openshift.io"],"resources":["certmanagers"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["update"],"apiGroups":["operator.openshift.io"],"resources":["certmanagers/finalizers"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["get","patch","update"],"apiGroups":["operator.openshift.io"],"resources":["certmanagers/status"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["get","list","patch","update","watch"],"apiGroups":["operator.openshift.io"],"resources":["istiocsrs"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["update"],"apiGroups":["operator.openshift.io"],"resources":["istiocsrs/finalizers"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["get","patch","update"],"apiGroups":["operator.openshift.io"],"resources":["istiocsrs/status"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["rbac.authorization.k8s.io"],"resources":["clusterrolebindings","clusterroles","rolebindings","roles"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create","delete","get","list","patch","update","watch"],"apiGroups":["route.openshift.io"],"resources":["routes","routes/custom-host"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create"],"apiGroups":["authentication.k8s.io"],"resources":["tokenreviews"]}
status: Satisfied
version: v1
- group: rbac.authorization.k8s.io
kind: PolicyRule
message: cluster rule:{"verbs":["create"],"apiGroups":["authorization.k8s.io"],"resources":["subjectaccessreviews"]}
status: Satisfied
version: v1
group: ""
kind: ServiceAccount
message: ""
name: cert-manager-operator-controller-manager
status: Present
version: v1// code placeholder
Expected result: Please remove clusterPermissions in Operator CSVs. Use just "permissions" instead. Thanks.
- account is impacted by
-
RFE-8072 CSV cert-manager-operator.v1.15.1 has cluster permissions
-
- Backlog
-