Description of problem:
[GRC] Resource does not get created with an empty field and the policy check flip-flops alternatively marking the policy as being compliant and non-compliant
Version-Release number of selected component (if applicable): ACM 2.7.0
How reproducible: Always
Steps to Reproduce:
- Create the GRC policy from ACM hub
- Propagate the policy on the managed cluster
- Check the details of the created resource from the managed cluster
- Check the compliance history of the GRC policy
Actual results:
Resource is created without the empty field and the policy flip-flops from being compliant to being non-compliant
Expected results:
Resource should get created with the empty field and the policy needs to be marked as compliant.
Additional info:
1) apiVersion: policy.open-cluster-management.io/v1
kind: Policy
metadata:
name: self-provisioning
namespace: acm-policies
annotations:
apps.open-cluster-management.io/do-not-delete: "true"
spec:
disabled: false
policy-templates:
- objectDefinition:
apiVersion: policy.open-cluster-management.io/v1
kind: ConfigurationPolicy
metadata:
name: self-provisioning
spec:
remediationAction: enforce
severity: high
pruneObjectBehavior: None
object-templates: - complianceType: mustonlyhave
objectDefinition:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
annotations:
rbac.authorization.kubernetes.io/autoupdate: "false"
name: self-provisioners
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: self-provisioner
subjects: []
2) Resource is created without the empty field:
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: self-provisioners
annotations:
rbac.authorization.kubernetes.io/autoupdate: 'false'
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: self-provisioner
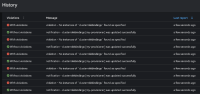
3) The compliance status is alternating between compliant and non compliant (report from ACM Dashboard):
Without violations notification - clusterrolebindings [self-provisioners] was updated successfully a few seconds ago
With violations violation - No instances of `clusterrolebindings` found as specified a few seconds ago
Without violations notification - clusterrolebindings [self-provisioners] was updated successfully a few seconds ago
With violations violation - No instances of `clusterrolebindings` found as specified a few seconds ago
Without violations notification - clusterrolebindings [self-provisioners] was updated successfully a few seconds ago
With violations violation - No instances of `clusterrolebindings` found as specified a few seconds ago
Without violations notification - clusterrolebindings [self-provisioners] was updated successfully a few seconds ago